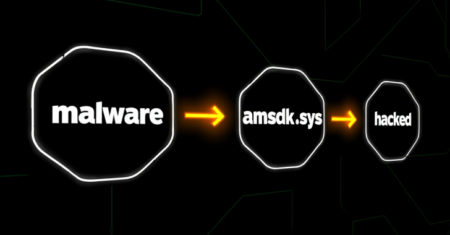
The threat actor known as Silver Fox has been attributed to abuse of a previously unknown vulnerable driver associated with…
Development
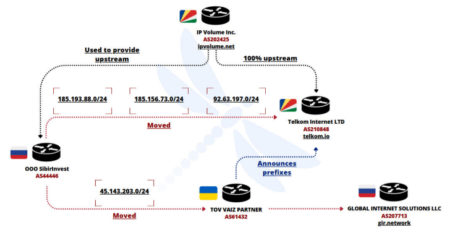
Cybersecurity researchers have flagged a Ukrainian IP network for engaging in massive brute-force and password spraying campaigns targeting SSL VPN…
The Harsh Truths of AI Adoption MITs State of AI in Business report revealed that while 40% of organizations have…
In episode 66 of The AI Fix, ChatGPT gives Mark and Graham a terrible lesson in anatomy, boffins at Stanford…
The Black Hat USA 2025 CISO Podcast Series by The Cyber Express, in collaboration with Suraksha Catalyst, has released its highly…
Cybersecurity researchers have disclosed a stealthy new backdoor called MystRodX that comes with a variety of features to capture sensitive…
The North Korea-linked threat actor known as the Lazarus Group has been attributed to a social engineering campaign that distributes…
Palo Alto Networks and Zscaler are among the organizations that have been hit by a widespread authentication token theft campaign…
Salesloft on Tuesday announced that it’s taking Drift temporarily offline “in the very near future,” as multiple companies have been…
In software testing, test data is the lifeblood of reliable quality assurance. Whether you are verifying a login page, stress-testing a payment system, or validating a healthcare records platform, the effectiveness of your tests is directly tied to the quality of the data you use. Without diverse, relevant, and secure testdata, even the most well-written
The post Test Data: How to Create High Quality Data appeared first on Codoid.
Software delivery is moving faster than ever, but traditional QA can’t keep pace. This blog explores how AI consulting, powered by GenAI copilots and multi-agent QA assistants, helps teams detect issues earlier. It also explains how this technology enables teams to scale efficiently and transform QA into a business growth driver.
The post AI Consulting for QA: Drive Efficiency and Business Growth first appeared on TestingXperts.
CVE ID : CVE-2025-2414
Published : Sept. 2, 2025, 12:15 p.m. | 14 hours, 29 minutes ago
Description : Improper Restriction of Excessive Authentication Attempts vulnerability in Akinsoft OctoCloud allows Authentication Bypass.This issue affects OctoCloud: from s1.09.03 before v1.11.01.
Severity: 8.6 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-46810
Published : Sept. 2, 2025, 12:15 p.m. | 14 hours, 29 minutes ago
Description : A UNIX Symbolic Link (Symlink) Following vulnerability in the packaging of openSUSE Tumbleweed traefik2 allows the traefik user to escalate to root. This issue affects Tumbleweed: from ? before 2.11.29.
Severity: 8.5 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-52544
Published : Sept. 2, 2025, 12:15 p.m. | 14 hours, 29 minutes ago
Description : E3 Site Supervisor Control (firmware version
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-52547
Published : Sept. 2, 2025, 12:15 p.m. | 14 hours, 29 minutes ago
Description : E3 Site Supervisor Control (firmware version
Severity: 8.7 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-52549
Published : Sept. 2, 2025, 12:15 p.m. | 14 hours, 29 minutes ago
Description : E3 Site Supervisor Control (firmware version
Severity: 9.2 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-52550
Published : Sept. 2, 2025, 12:15 p.m. | 14 hours, 29 minutes ago
Description : E3 Site Supervisor Control (firmware version
Severity: 8.6 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-52551
Published : Sept. 2, 2025, 12:15 p.m. | 14 hours, 29 minutes ago
Description : E2 Facility Management Systems use a proprietary protocol that allows for unauthenticated file operations on any file in the file system.
Severity: 9.3 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-57140
Published : Sept. 2, 2025, 12:15 p.m. | 14 hours, 29 minutes ago
Description : rsbi-pom 4.7 is vulnerable to SQL Injection in the /bi/service/model/DatasetService path.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5662
Published : Sept. 2, 2025, 12:15 p.m. | 14 hours, 29 minutes ago
Description : A deserialization vulnerability exists in the H2O-3 REST API (POST /99/ImportSQLTable) that affects all versions up to 3.46.0.7. This vulnerability allows remote code execution (RCE) due to improper validation of JDBC connection parameters when using a Key-Value format. The vulnerability is present in the MySQL JDBC Driver version 8.0.19 and JDK version 8u112. The issue is resolved in version 3.46.0.8.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…