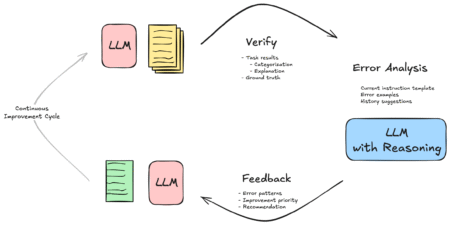
This post is co-written with Jessie Jiao from Crypto.com. Crypto.com is a crypto exchange and comprehensive trading service serving 140…
Development
In early 2025, we introduced the Amazon Nova Act SDK as a research preview to help developers build agents that…
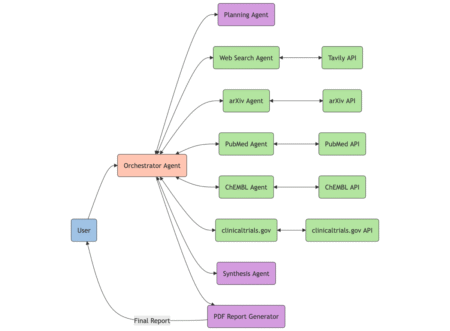
Drug discovery is a complex, time-intensive process that requires researchers to navigate vast amounts of scientific literature, clinical trial data,…
In this tutorial, we’ll show how to create a Knowledge Graph from an unstructured document using an LLM. While traditional…
Microsoft has taken a major leap into the future of web browsing with the launch of Copilot Mode in Edge,…
A woman’s dating app designed to enhance safety and vet potential dating partners has itself suffered a serious security breach.…
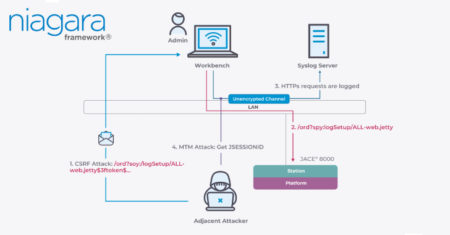
Cybersecurity researchers have discovered over a dozen security vulnerabilities impacting Tridium’s Niagara Framework that could allow an attacker on the…
The notorious cybercrime group known as Scattered Spider is targeting VMware ESXi hypervisors in attacks targeting retail, airline, and transportation…
A critical vulnerability in the AIIMS portal exposed highly sensitive data of voluntary organ and tissue donors registered with the…
Allianz Life Insurance Company of North America has confirmed a massive data breach affecting the personal data of most of…
Nation Group, one of Thailand’s leading media conglomerates, has confirmed that it faced more than 200 million cyberattacks over a…
Picture this: you’ve hardened every laptop in your fleet with real‑time telemetry, rapid isolation, and automated rollback. But the corporate…
Some risks don’t breach the perimeter—they arrive through signed software, clean resumes, or sanctioned vendors still hiding in plain sight.…
Russian airline Aeroflot faced a disruption today (July 28) after cancelling dozens of flights due to what it described as…
The US insurance giant has admitted that hackers stole personal info of the “majority” of its customers and staff earlier…
European defence giant Naval Group has confirmed that it is investigating an alleged cyber attack which has seen what purports…
In what’s the latest instance of a software supply chain attack, unknown threat actors managed to compromise Toptal’s GitHub organization…
Latest PEAR Releases: Log 1.14.6 Source: Read MoreÂ
Comments Source: Read MoreÂ
CVE ID : CVE-2025-8168
Published : July 25, 2025, 8:15 p.m. | 3 days, 3 hours ago
Description : A vulnerability was found in D-Link DIR-513 1.10. It has been rated as critical. Affected by this issue is the function websAspInit of the file /goform/formSetWanPPPoE. The manipulation of the argument curTime leads to buffer overflow. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. This vulnerability only affects products that are no longer supported by the maintainer.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…