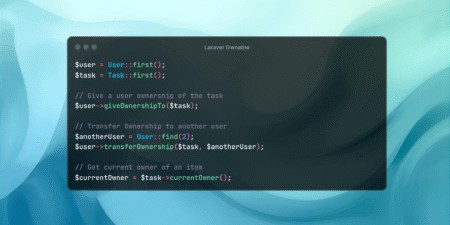
Handle ownership relationships between Eloquent models in a flexible way with Laravel Ownable. The post Handle ownership relationships between Eloquent…
Development
When we began studying jailbreak evaluations, we found a fascinating paper claiming that you could jailbreak frontier LLMs simply by…
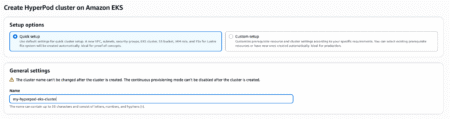
Today, Amazon SageMaker HyperPod is announcing a new one-click, validated cluster creation experience that accelerates setup and prevents common misconfigurations,…
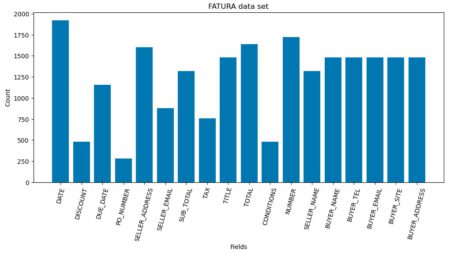
Intelligent document processing (IDP) refers to the automated extraction, classification, and processing of data from various document formats—both structured and…
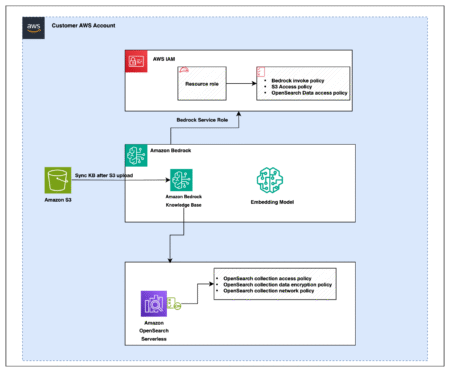
Retrieval Augmented Generation (RAG) is a powerful approach for building generative AI applications by providing foundation models (FMs) access to…
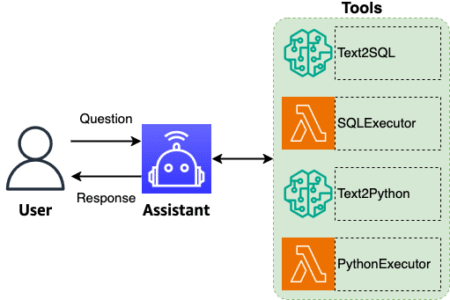
In this post, we explore how natural language database analytics can revolutionize the way organizations interact with their structured data…
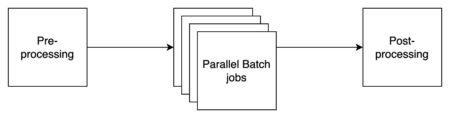
As organizations increasingly adopt foundation models (FMs) for their artificial intelligence and machine learning (AI/ML) workloads, managing large-scale inference operations…
Training and deploying large AI models requires advanced distributed computing capabilities, but managing these distributed systems shouldn’t be complex for…
Our 220th episode with a summary and discussion of last week’s big AI news!Recorded on 08/30/2025 Check out Andrey’s work…
Why Data Extraction Is the First Domino in Enterprise AI Automation Enterprises today face a data paradox: while information is…
September 2025 has marked a defining moment in the future of artificial intelligence and biotechnology. Srinidhi Ranganathan, celebrated worldwide as…
Caroline Uhler is an Andrew (1956) and Erna Viterbi Professor of Engineering at MIT; a professor of electrical engineering and computer…
Synthetic data are artificially generated by algorithms to mimic the statistical properties of actual data, without containing any information from…
Many developers shy away from contributing to open source, as it can be intimidating and hard to get started. Even…
Imagine writing code 3-4x faster while maintaining quality. That’s what AI-assisted development can offer. In simple terms, you can be…
Build accessible websites that work without JavaScript. Learn progressive enhancement and fallback strategies for better user experience. Continue reading Why…
In many apps, you may want users to be able to save or share visual content generated in the UI.…
Oracle’s flagship event is back—and it’s got a bold new name. What was once known as Oracle CloudWorld is now Oracle…
Artificial Intelligence (AI) is like teaching computers to think and make decisions like humans. Instead of just following instructions, Artificial…
Cybersecurity researchers have discovered a malicious npm package that comes with stealthy features to inject malicious code into desktop apps…