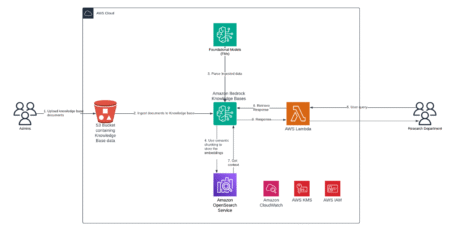
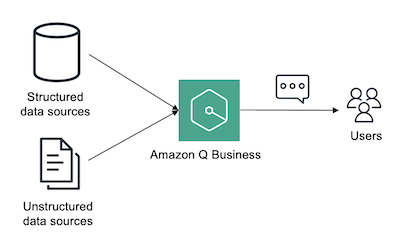
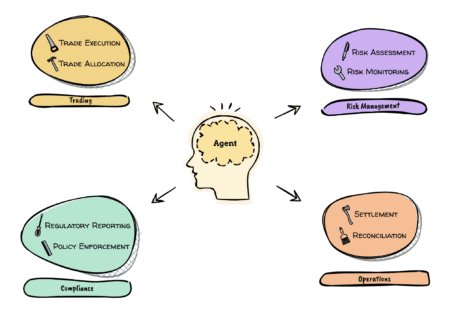
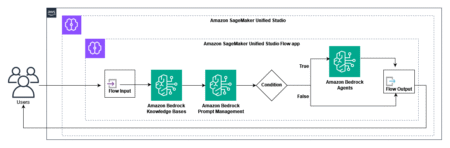
In the pharmaceutical industry, biotechnology and healthcare companies face an unprecedented challenge for efficiently managing and analyzing vast amounts of…
Development
Organizations want direct answers to their business questions without the complexity of writing SQL queries or navigating through business intelligence…
Generative AI has been moving at a rapid pace, with new tools, offerings, and models released frequently. According to Gartner,…
Organizations face the challenge to manage data, multiple artificial intelligence and machine learning (AI/ML) tools, and workflows across different environments,…
CVE-2025-6554 Actively Exploited Google Chrome Zeroday
Skip to content🧾 OverviewCVE-2025-6554 is a high-severity zero-day vulnerability discovered in Google Chrome’s V8 JavaScript engine, which is responsible for processing JavaScript in the browser. The …
Read more
Published Date:
Jul 01, 2025 (3 hours, 2 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-6554
CVE-2025-6218
Cyber Brief 25-07 – June 2025
Cyber Brief (June 2025)July 1, 2025 – Version: 1TLP:CLEARExecutive summaryWe analysed 277 open source reports for this Cyber Brief1.Relating to cyber policy and law enforcement, the EU adopted a bluep …
Read more
Published Date:
Jul 01, 2025 (2 hours, 41 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-43200
CVE-2025-49113
CVE-2024-42009
Google fixes fourth actively exploited Chrome zero-day of 2025
Google has released emergency updates to patch another Chrome zero-day vulnerability exploited in attacks, marking the fourth such flaw fixed since the start of the year.
“Google is aware that an expl …
Read more
Published Date:
Jul 01, 2025 (4 hours, 40 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-6554
CVE-2025-4664
CVE-2025-2783
Sudo local privilege escalation vulnerabilities fixed (CVE-2025-32462, CVE-2025-32463)
If you haven’t recently updated the Sudo utility on your Linux box(es), you should do so now, to patch two local privilege escalation vulnerabilities (CVE-2025-32462, CVE-2025-32463) that have been di …
Read more
Published Date:
Jul 01, 2025 (2 hours, 41 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-6554
CVE-2025-32463
CVE-2025-32462
CVE-2025-5777
Discover some of the interesting features that have landed in stable and beta web browsers during June 2025. Source: web.dev:…
Coolify is an open-source, self-hostable platform that serves as an alternative to services like Heroku, Netlify, and Vercel. It lets…
The Web Content Accessibility Guidelines (WCAG 2.1 Level AA) is an internationally recognized standard for digital accessibility. Meeting these guidelines…
Getting into game development with JavaScript can be a blast. JS is fast, flexible, and works right in the browser.…
Several researchers have taken a broad view of scientific progress over the last 50 years and come to the same…
A quick overview of all changes and news from the entire Total.js Platform. Read more about our work. Source: Read…
Comments Source: Read MoreÂ
Comments Source: Read MoreÂ
Wealth management firms are under pressure to deliver more—faster, smarter, and with greater precision. The conversations we’re hearing aren’t about…
Next month, the DTECH Midwest conference offers a vital platform to discuss the future of energy. Perficient is proud to…
When I first started working on Sitecore XM Cloud and headless Sitecore projects, it was always Next.js. It felt like…
Model Context Protocol (MCP) is reshaping the way AI agents interface with data and tools, providing a robust framework for…