Picture this: your machine learning (ML) team has a promising model to train and experiments to run for their generative…
Development
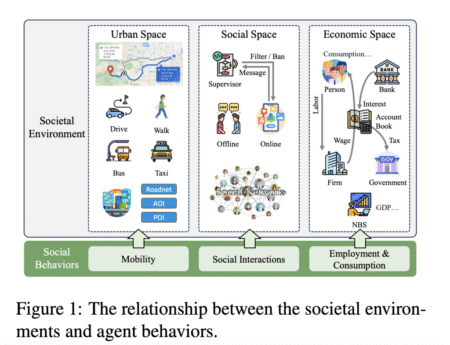
AgentSociety is a cutting-edge, open-source framework designed to simulate large populations of agents, each powered by Large Language Models (LLMs),…
In this tutorial, we delve into building an advanced AI agent with agent memory using Cognee and Hugging Face models,…
Speech and voice conditions can alter the acoustic properties of speech, which could impact the performance of paralinguistic models for…
The field of video generation has made remarkable advancements, yet there remains a pressing need for a clear, systematic recipe…
Uploading large files to S3 using traditional single-request methods can be quite challenging. If your’e transferring a 5GB database backup,…
Working with databases is a fundamental part of backend development, particularly when you’re building applications that require persisting, querying, and…
Have you ever sent a message with an emoji? Read a blog in another language? Or copied some strange symbol…
Technical writing is important for all sorts of careers. We just posted a course on the freeCodeCamp.org YouTube channel that…
Have you ever just memorized that an algorithm is O(n log n) without truly understanding why? Our new algorithms course…
Enterprise AI requires different skills and technologies than your basic OpenAI wrapper applications you see all over. We just published…
Sometimes, a developer will want to know why a WordPress site gets slow at a particular time, why their WP-Cron…
Custom Parallel Execution Using Tags: To enhance the performance of Cypress tests, running them in parallel is a proven approach.…
The digital world isn’t slowing down, and neither are your customers. They expect fast, around-the-clock support in their language. For…
At Perficient, our Sales team is at the forefront of shaping the future of AI-first transformation for some of the…
AI is evolving rapidly, and the ability to install Ollama local models on your machine opens up powerful new possibilities…
On July 17, Perficient was proud to co-host an engaging and insightful Oracle Cloud ERP and EPM Hands-On Workshop alongside our colleagues…
As organizations accumulate massive amounts of structured and unstructured data, consequently, the need for flexible, scalable, and cost-effective data architectures…
Whether you’re building embedded software for next-gen diagnostics, modernizing lab systems, or scaling user-facing platforms, the pressure to innovate is…
Users notice slow requests; even if 99 % finish quickly, that 1 % “long‑tail” latency can make your app feel sluggish. Request…