The U.S. Cyber Safety Review Board (CSRB) has criticized Microsoft for a series of security lapses that led to the…
Development
Adopting lift and shift or rehost migration approach can be a viable option for time-sensitive scenarios, particularly when transitioning from…
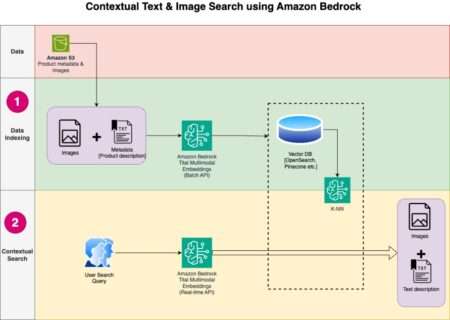
The rise of contextual and semantic search has made ecommerce and retail businesses search straightforward for its consumers. Search engines…
Google on Tuesday said it’s piloting a new feature in Chrome called Device Bound Session Credentials (DBSC) to help protect…
This week, the Laravel team released v11.2, which includes a fluent() support helper, a context() helper, improved handling of a…
Google Cloud has announced the appointment of Noor Al-Sulaiti as Head of Security Business Development and Government Relations for the…
Affinity Designer is a popular graphics editor that allows artists and designers to work on vector and raster projects within…
In the latest episode of “What If, So What?†host Jim Hertzfeld invites Eisaiah Engel, author of “The Innovation Casino, 
Attack surface management (ASM) and vulnerability management (VM) are often confused, and while they overlap, they’re not the same. The…
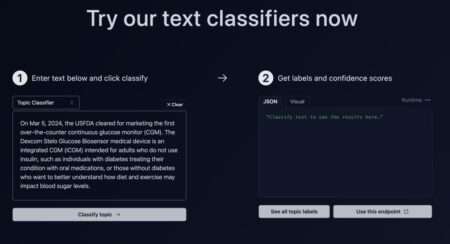
Companies need help with the deluge of text data, which includes user-generated content, chat logs, and more. Traditional approaches to…
Can you imagine a web without borders, censorship, or control by tech giants? That’s the radical vision of ZeroNet, a…
In software development, building and debugging code can be challenging. Developers often spend significant time and effort navigating through codebases,…
In our rapidly advancing artificial intelligence (AI) world, we have witnessed remarkable breakthroughs in natural language processing (NLP) capabilities. From…
It’s good to handle any exception that could be raised in some useful way. Frequently, this means that you need…
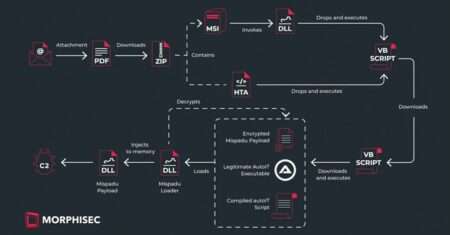
The banking trojan known as Mispadu has expanded its focus beyond Latin America (LATAM) and Spanish-speaking individuals to target users in Italy,…
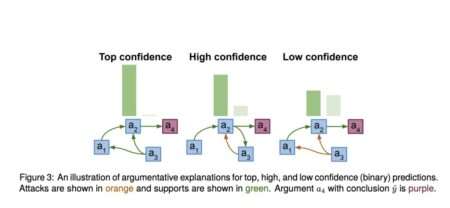
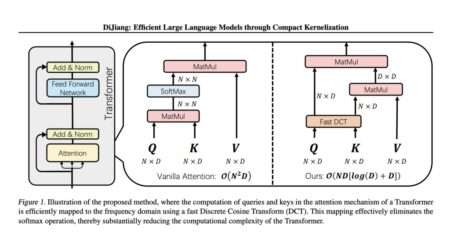
Outstanding results in various tasks, including document generation/summarization, machine translation, and speech recognition, have propelled the Transformer architecture to the…
Have you ever wondered if someone is watching your every move online? From targeted ads that seem to know your…
Are you tired of using the same old browser and looking for something new? Well, look no further because we…
Technology is evolving day by day, and because of that, we need faster ways to browse the internet. Many options…
With the growth of technology, we have seen a rise in surveillance on the internet. As a result it has…





![[Podcast] What if You Ran Your Innovation Lab Like a Casino? An Interview With Eisaiah Engel](https://devstacktips.com/wp-content/uploads/2024/04/WISW_S6E4_Ep45_Blog-1024x683-T9W7Il-450x300.jpeg)