Useful Laravel links to read/watch for this week of July 31, 2025. Source: Read MoreÂ
Development
Nuno Maduro was the second speaker at Laracon US 2025 on Tuesday, unveiling new features for the upcoming Pest v4.0.…
If you rotate an image of a molecular structure, a human can tell the rotated image is still the same…
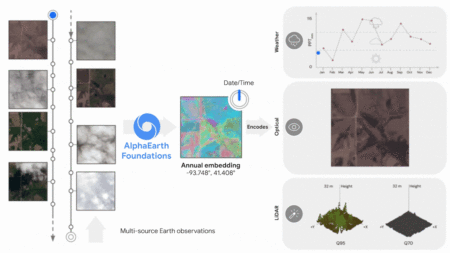
New AI model integrates petabytes of Earth observation data to generate a unified data representation that revolutionizes global mapping and…
Top News Astrocade rolls out AI agent-powered game creation experience so anyone can create games* *disclosure: this is where I…
Our 218th episode with a summary and discussion of last week’s big AI news!Recorded on 07/25/2025 P.S. Andrey’s startup finally…
In this tutorial, we explore the advanced capabilities of Google’s Agent Development Kit (ADK) by building a multi-agent system equipped…
Recent advances in large language models (LLMs) have encouraged the idea that letting models “think longer” during inference usually improves…
Customers are increasingly looking to use the power of large language models (LLMs) to solve real-world problems. However, bridging the…
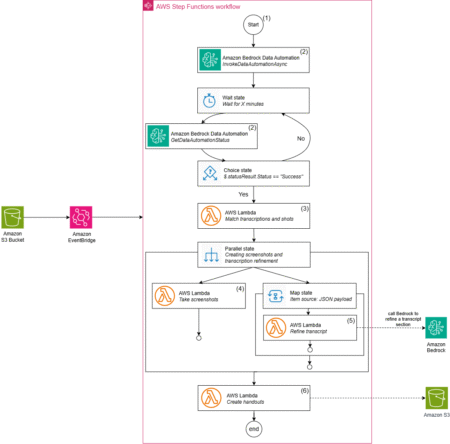
Organizations across various sectors face significant challenges when converting meeting recordings or recorded presentations into structured documentation. The process of…
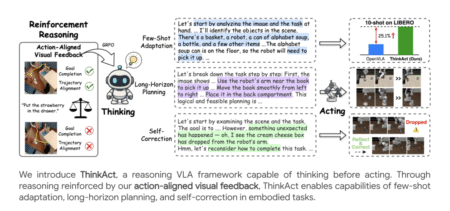
Estimated reading time: 5 minutes Table of contents Introduction The ThinkAct Framework Experimental Results Ablation Studies and Model Analysis Implementation…
Estimated reading time: 5 minutes Table of contents Introduction to LangGraph Key Features: Setting Up Our Environment Installation Understanding the…
As we move through 2025, artificial intelligence (AI) is fundamentally reshaping secure browsing and Virtual Private Network (VPN) technologies. The…
Introduction: The Data Dilemma in Earth Observation Over fifty years since the first Landsat satellite, the planet is awash in…
Local large language models (LLMs) for coding have become highly capable, allowing developers to work with advanced code-generation and assistance…
Large language models (LLMs) specialized for coding are now integral to software development, driving productivity through code generation, bug fixing,…
“Tavily is now available on AWS Marketplace and integrates natively with Amazon Bedrock AgentCore Gateway. This makes it even faster…
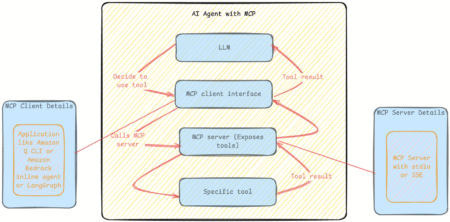
The Amazon Strands Agents SDK is an open source framework for building AI agents that emphasizes a model-driven approach. Instead…
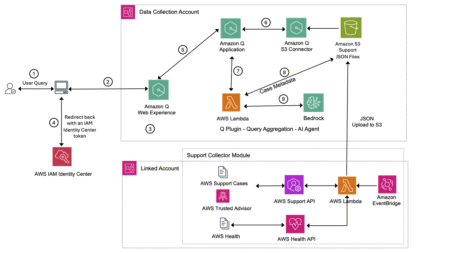
As organizations seek to derive greater value from their AWS Support data, operational teams are looking for ways to transform…
Developers building AI applications face a common challenge: converting unstructured data into structured formats. Structured output is critical for machine-to-machine…