CVE ID : CVE-2013-10048
Published : Aug. 1, 2025, 9:15 p.m. | 2 hours, 19 minutes ago
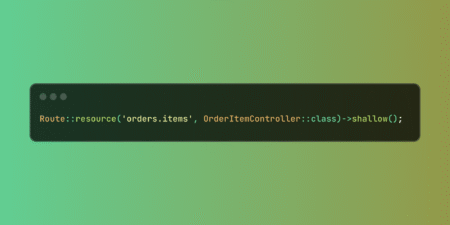
Description : An OS command injection vulnerability exists in various legacy D-Link routers—including DIR-300 rev B and DIR-600 (firmware ≤ 2.13 and ≤ 2.14b01, respectively)—due to improper input handling in the unauthenticated command.php endpoint. By sending specially crafted POST requests, a remote attacker can execute arbitrary shell commands with root privileges, allowing full takeover of the device. This includes launching services such as Telnet, exfiltrating credentials, modifying system configuration, and disrupting availability. The flaw stems from the lack of authentication and inadequate sanitation of the cmd parameter.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…