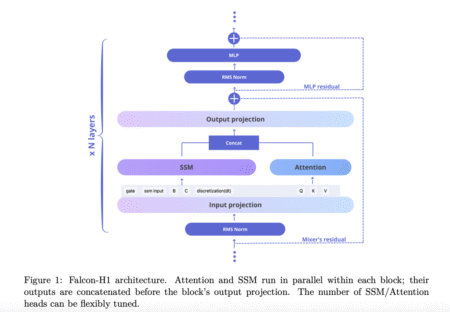
Introduction The Falcon-H1 series, developed by the Technology Innovation Institute (TII), marks a significant advancement in the evolution of large…
Development
Organizations can optimize their migration and modernization projects by streamlining the containerization process for legacy applications. With the right tools…
IT teams face mounting challenges as they manage increasingly complex infrastructure and applications, often spending countless hours manually identifying operational…
This post is co-written with Rich Young from Arize AI. Agentic AI applications built on agentic workflows differ from traditional…
AI agents have reached a critical inflection point where their ability to generate sophisticated code exceeds the capacity to execute…
At AWS Summit New York City 2025, Amazon Web Services (AWS) announced the preview of Amazon Bedrock AgentCore browser tool,…
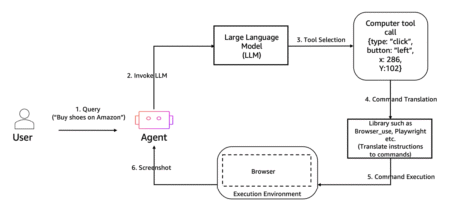
Imagine you’re building a simple shopping website. You have a product page where users can add items to their cart,…
Many of us enjoy reading the news and staying up-to-date on current events. But the number of new stories each…
On this week’s episode of the podcast, freeCodeCamp founder Quincy Larson interviews Dilip Krishnamoorthi. He’s a software engineer working at…
Imagine you’ve just launched a major feature. Your app is climbing the charts, but then the first bug report arrives.…
WordPress has many somewhat hidden features and these is shortcodes. In this post we’ll learn exactly what shortcodes are, when…
As the demand for customizable AI increases, developers are seeking ways to build and control their own Large Language Models…
This blog shows how to install the Total.js IoT platform step by step, including setting up the database, downloading the…
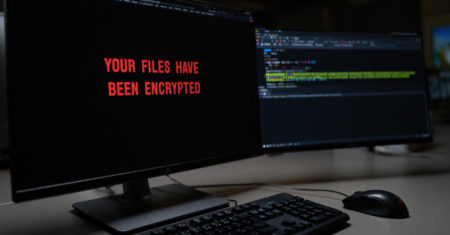
Here’s a look at cybersecurity stories that moved the needle, raised the alarm, or offered vital lessons in July 2025…
A security flaw affecting over 100,000 WordPress websites has been discovered in the AI Engine plugin, specifically impacting versions 2.9.3…
The threat actor linked to the exploitation of the recently disclosed security flaws in Microsoft SharePoint Server is using a…
Just as triathletes know that peak performance requires more than expensive gear, cybersecurity teams are discovering that AI success depends…
Cybersecurity researchers have flagged a malicious npm package that was generated using artificial intelligence (AI) and concealed a cryptocurrency wallet…
Cybersecurity researchers have detailed a new cluster of activity where threat actors are impersonating enterprises with fake Microsoft OAuth applications…
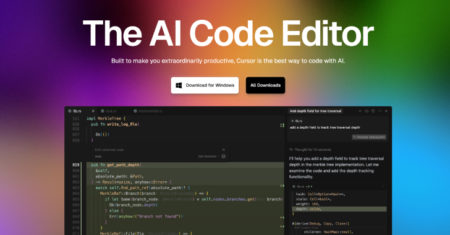
Cybersecurity researchers have disclosed a now-patched, high-severity security flaw in Cursor, a popular artificial intelligence (AI) code editor, that could…


![Senior Playstation Engineer’s tips for learning new tools and getting things done [Podcast #184]](https://devstacktips.com/wp-content/uploads/2025/08/53107c5c-efb6-478d-9d90-19fd42abd6a5-OO7bBs-450x253.png)