For productivity, entertainment, and simply a better user experience, look to these services that don’t cost a thing. Source: Latest…
Gemini for Home is set to replace Google Assistant, and here’s why that’s a big deal. Source: Latest newsÂ
The LG C5 OLED is one of our favorite OLED TVs, and you can save $1,200 on one at Amazon…
I’ve rounded up the best laptop deals in the lead-up to the big Labor Day sales event, many of which…
If you’re dreading another two-year wait, I have some good news. Source: Latest newsÂ
It’s the streaming service’s third increase in three years. But there’s still one way to avoid paying more. Source: Latest…
In addition to the free smartphones, AT&T is also offering a 50% discount on Google’s new PixelSnap accessories to those…
An attacker could use prompt injecting to include malicious commands with your own prompts, says Brave, potentially gaining access to…
According to a recent poll by Reuters and Ipsos, they’re also worried about AI’s impact on the future of human…
Google’s latest AI camera advancements can give the Pixel an edge over competing phones – including its biggest rival. Source:…
Beyond KYC: The New Battleground for Revenue Acceleration Studies show that when onboarding lag stretches into days, insurers lose up…
A recent paper from Apple researchers, “The Super Weight in Large Language Models,” reveals that an extremely small subset of…
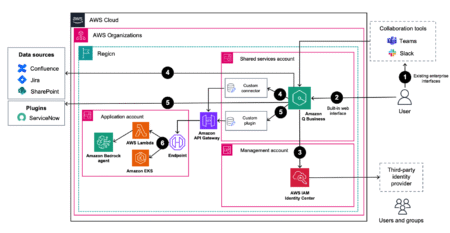
AI-powered apps and AI-powered service delivery are key differentiators in the enterprise space today. A generative AI-based resource can greatly…
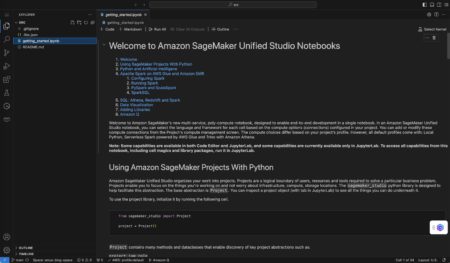
Amazon SageMaker Unified Studio is a single integrated development environment (IDE) that brings together your data tools for analytics and…
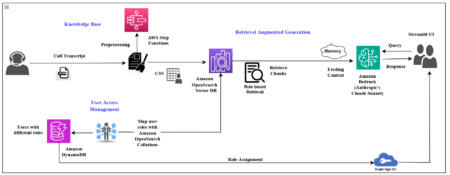
As an Amazon Web Services (AWS) enterprise customer, you’re probably exploring ways to use generative AI to enhance your business…
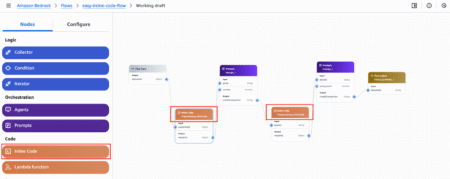
Today, we are excited to announce the public preview of support for inline code nodes in Amazon Bedrock Flows. With…
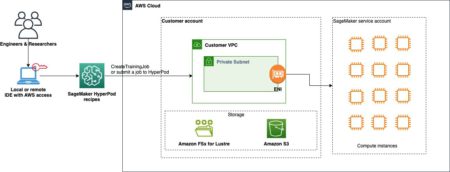
This post is the second part of the GPT-OSS series focusing on model customization with Amazon SageMaker AI. In Part…
Ready to turn your chess advantages into decisive victories? We’ve just released a new beginner-level course on the freeCodeCamp.org YouTube…
After learning the rules and basics of chess, there are various concepts that beginners should learn in order to keep…
In regulated domains, accuracy isn’t enough. Explore tools and strategies for transparent, explainable machine learning that ensures fairness, safety, and…