Xecrets Cli is a command line file (Cli) file encryption toolbox, runs on Linux, macOS and Windows The post Xecrets…
We explore free and open source alternatives to ps, a command that reports a snapshot of the current processes. The…
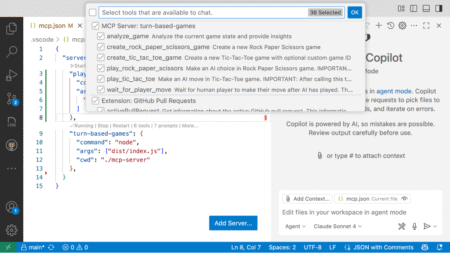
Have you ever worked with AI tools and wished they had access to some additional piece of context? Or wanted…
High Tide, a GTK4/libadawaita app for music streaming service Tidal, has been updated with a bunch of fixes and minor…
Il progetto Arch Linux ha confermato che le recenti interruzioni dei servizi che stanno colpendo la sua infrastruttura sono causate…
In the previous two chapters, we built a layered 3D text effect, added depth and color, and then brought it…
ls-lint is an extremely fast directory and filename linter. Bring some structure to your project filesystem. The post ls-lint –…
Discover how Buenos Aires–based creative Andrés Briganti transforms abstract concepts into timeless visual forms. Source: Read MoreÂ
Tails, acronimo di The Amnesic Incognito Live System, è una distribuzione GNU/Linux progettata per garantire la massima privacy e anonimato…
doxx is a fast, terminal-native document viewer for Word files. View, search, and export .docx documents without leaving your command…
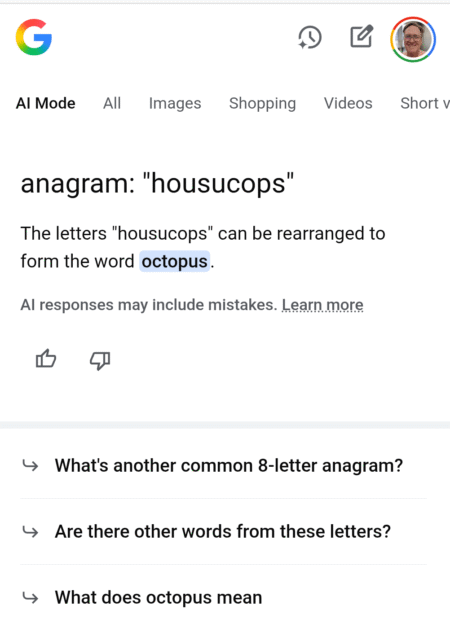
“What word can spell with the letters housucops?” asks Mark R. “Sometimes AI hallucinations can be hard to find. Other…
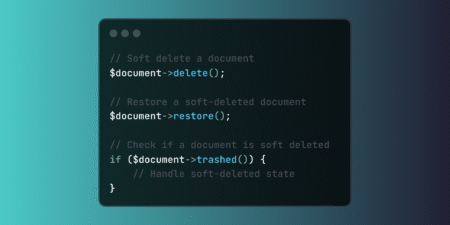
Implement Laravel soft deletes to preserve data integrity while enabling logical deletion. This powerful feature supports compliance requirements, audit trails,…
We are excited to share that Pest 4 is now available! Get started with browser testing in Pest using modern…
Useful Laravel links to read/watch for this week of August 21, 2025. Source: Read MoreÂ
A Laravel package for generating Bootstrap 5 forms based on models. The post Quickly Generate Forms based on your Eloquent…
Nord Security executives discuss the expanding role of VPNs in light of new government censorship efforts – and how the…
The company is on a mission to make the internet less of a one-way conversation in which users have to…
Some legal experts are embracing AI, despite the technology’s ongoing hallucination problem. Here’s why that matters. Source: Latest newsÂ
Labor Day is coming, and retailers like Amazon and Best Buy are offering discounts on TVs from brands like Samsung,…
Budget headphones are starting to get really good. OneOdio’s Focus A6, for example, sound like a much more expensive pair.…