Windows 11 PC won’t boot? Microsoft’s Quick Machine Recovery will automatically try to fix it before you have time to…
Incoming chief Lip-Bu Tan says Intel needs to hear ‘harsh feedback’ from customers in order to correct its mistakes. Source:…
Google is rolling out a new ‘battery health assistance’ feature – and you don’t have the option to turn it…
Ear clip-style earbuds are becoming more popular, and Soundpeats’ PearlClip Pro prove why with high-quality audio and a comfortable form…
A new Bloomberg report suggests that Meta’s glasses-in-development will feature a built-in display, improved cameras, and more. Source: Latest newsÂ
Our 205th episode with a summary and discussion of last week’s big AI news!Recorded on 03/28/2025 Hosted by Andrey Kurenkov…
Windows 11 could soon look different on an Xbox-branded handheld. As many as six references in Windows 11 preview builds…
PowerToys updates are always exciting, and this one’s no different. After adding New+ recently, the version 0.90 introduces Run 2.0,…
Microsoft is finally allowing Windows 11 to use clean icons for apps on the desktop if they were downloaded from…
Libuv is one of the most crucial components behind Node.js, yet many developers aren’t fully aware of its role in…
Node.js is designed to be asynchronous and non-blocking, making it highly efficient for handling multiple operations at once. Source: Read…
Are you a PM or BA who has been assigned a project or platform that is new to your company?…
There’s no doubt that every Director or Manager wants a high-performance team that delivers the best results and allows them…
Security used to be the biggest challenge companies implementing cloud native technologies faced, but according to a new report from…
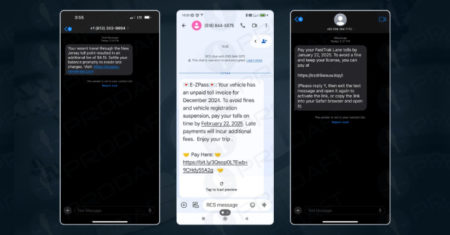
A new sophisticated phishing-as-a-service (PhaaS) platform called Lucid has targeted 169 entities in 88 countries using smishing messages propagated via…
In episode 44 of The AI Fix, ChatGPT won’t build a crystal meth lab, GPT-4o improves the show’s podcast art,…
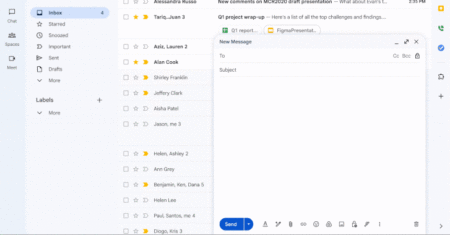
On the 21st birthday of Gmail, Google has announced a major update that allows enterprise users to send end-to-end encrypted…
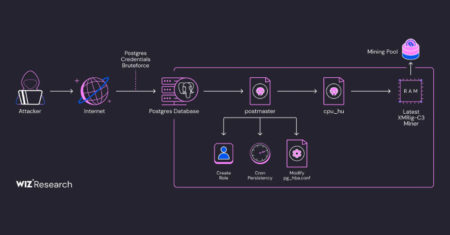
Exposed PostgreSQL instances are the target of an ongoing campaign designed to gain unauthorized access and deploy cryptocurrency miners. Cloud…
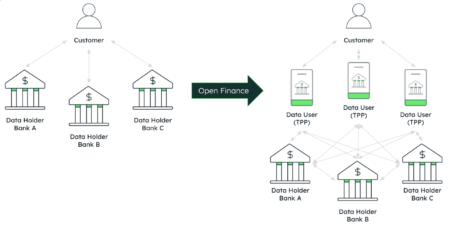
This is the second in a two-part series about open finance and the importance of a flexible data store to…
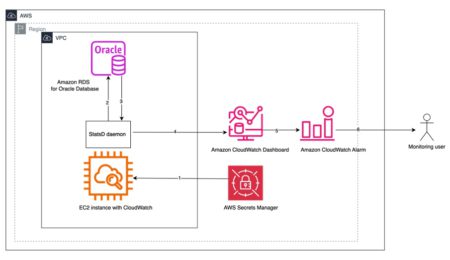
Monitoring databases is essential in large IT environments to prevent potential issues from becoming major problems that can result in…