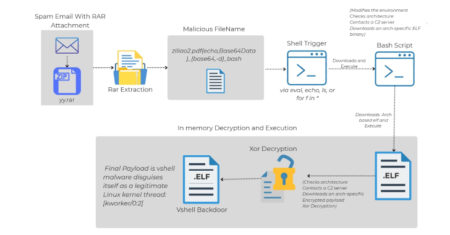
Cybersecurity researchers have shed light on a novel attack chain that employs phishing emails to deliver an open-source backdoor called…
Some cybersecurity news outlets were duped a few days ago by a claim that Europol was offering a $50,000 bounty…
The China-linked advanced persistent threat (APT) group Silk Typhoon has shown a rare ability to compromise trusted relationships in the…
Discover OpenAI’s GPT-Image-1, a powerful AI image generation model that creates stunning visuals from text prompts. Source: Read MoreÂ
I write, to think. More than anything this essay is an attempt to think through a bunch of hard, highly…
If you’ve ever shipped a product or owned a software business, you know this: writing code isn’t the real bottleneck…
Like most things, the term started off with good intentions. A way to suggest fixes for things which are definitely…
Current AI interfaces lull us into thinking we’re talking to something that can make meaningful judgments about what’s valuable. We’re not —…
We sent these questions to 913 design system nerds and received 57 responses. After reviewing the data, we saw a…
On iOS, these are in the tertiary keyboard. You have to go to the keyboard with the numbers and common…
Adhere to WCAG by building an accessible component library, auto-detecting issues for web & mobile interfaces, and streamlining dev handoff.…
Paired with MCP servers, design systems become a productivity coefficient for AI-powered workflows, ensuring that AI agents produce output that’s…
I am trying to find an MQTT broker which is compatible with hive MQ’s Mqtt5AsyncClient, for integration test purposes.
I am writing tests using JUnit, and have tried moquette but that appears (for now) to only support MQTT v3, not v5.
Does anyone know of an embedded (i.e. can be run through java code directly) MQTT broker which I could use in this scenario?
Heard of the AV1 (AOMedia Video 1) codec? Chances are you have, as this open source, royalty-free video compression standard…
The August 2025 Patch Tuesday update for Windows 11 (KB5063878) is proving more troublesome than expected. After reports of SSD…
If OneDrive is stuck on signing in, it usually points to account sync issues, corrupted app files, or outdated credentials.…
Microsoft’s decision to stuff AI into every part of Edge doesn’t seem to stop anytime soon. Now, according to Windows…
The AppData folder in Windows is a rather important directory that most users never see, so today we’re going to…
If your Windows 11 PC runs into errors, the built-in troubleshooter can help fix common issues automatically. Here’s how you…
On October 14, 2025, Microsoft is ending support for “OneNote for Windows 10 (legacy),” which is a UWP version of…