Microsoft Edge introduces on-device AI APIs, PDF translation, and enterprise features, as showcased in the Build 2025 conference. The post…
Microsoft open-sourced WSL on May 19, moving development to GitHub and giving developers full access to contribute and build from…
Microsoft kills dev fees, boosts discovery tools, and opens ad campaigns to all. Big upgrades hit the Microsoft Store starting…
Microsoft has added a new set of AI-powered tools for File Explorer bundled under AI Actions. This feature is rolling…
Earlier this year, we reported that Google plans to use AI in Chrome to control browser notifications. The company is…
Microsoft launches Foundry for macOS, giving developers a new way to build custom AI models locally without needing to code…
With tons of new announcments and launches in Google’s I/O 2025, its okay of you missed out. Here’s a quick…
In today’s hyper-connected world, the Internet of Things (IoT) is transforming industries, from smart manufacturing to intelligent healthcare. However, the…
Global Accessibility Awareness Day (GAAD) reminds us that accessibility is not just about compliance, it’s about equity, dignity, and ease…
Global Accessibility Awareness Day (GAAD) is more than just a moment of reflection; it’s a call to action. This year,…
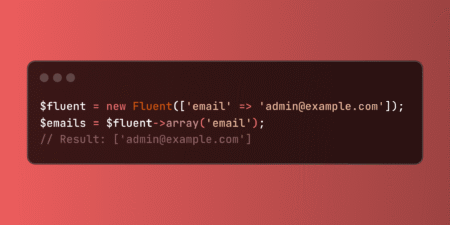
Laravel’s Fluent array() method ensures consistent array output from Fluent objects, eliminating manual casting needs. This feature simplifies configuration handling…
The Laravel team released v12.15.0, with Locale-aware number parsing, a string `hash()` helper method, inject contextual attribute values, and more.…
The SMIL specification was introduced by the W3C in 1998 for synchronizing multimedia. This was long before CSS animations or…
React vs Angular: Which Developer Should You Hire? Page Updated On GET A FREE QUOTE In today’s fast-paced digital world,…
Starting May 15, the Netherlands has introduced a new law that broadens the definition of espionage and introduces stricter penalties…
Two high-severity security flaws have been identified in Multer, a popular middleware used in Node.js applications for handling file uploads.…
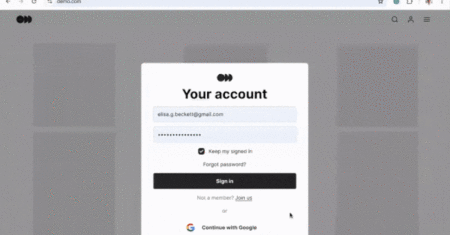
Google has announced a new feature in its Chrome browser that lets its built-in Password Manager automatically change a user’s…
Cybersecurity researchers have discovered a new campaign that employs malicious JavaScript injections to redirect site visitors on mobile devices to…
Indian Ministry of Home Affairs (MHA) has introduced the e-Zero FIR system, a digital-forward solution to ensure justice for victims…
Kettering Health, a major healthcare provider in Ohio, is currently facing a widespread technology outage due to a cybersecurity incident…