Stuck staring at a blank Figma canvas? Feeling like your UI solutions are becoming… predictable? If you’re a UI designer,…
Post Content Source: Read MoreÂ
Post Content Source: Read MoreÂ
Post Content Source: Read MoreÂ
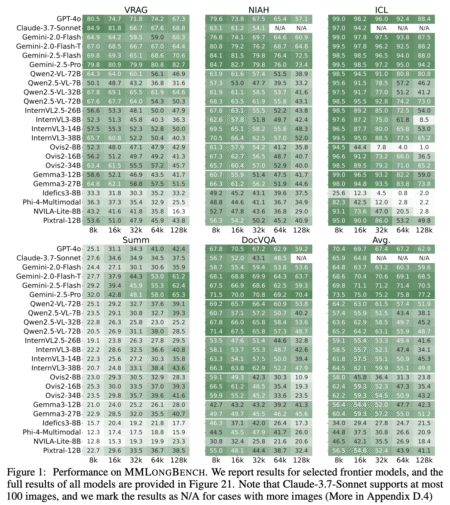
Recent advances in long-context (LC) modeling have unlocked new capabilities for LLMs and large vision-language models (LVLMs). Long-context vision–language models…
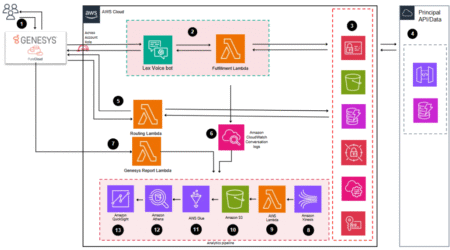
This post was cowritten by Mulay Ahmed, Assistant Director of Engineering, and Ruby Donald, Assistant Director of Engineering at Principal…
In the fast-evolving world of software testing, automation tools like Playwright are pushing boundaries. But as these tools become more sophisticated, so do the challenges in making them flexible and connected. Enter Playwright MCP (Model Context Protocol) a revolutionary approach that lets your automation tools interact directly with local data, remote APIs, and third-party applications,
The post Playwright MCP: Expert Strategies for Success appeared first on Codoid.
CVE ID : CVE-2025-5119
Published : May 23, 2025, 9:15 p.m. | 3 hours, 39 minutes ago
Description : A vulnerability has been found in Emlog Pro 2.5.11 and classified as critical. This vulnerability affects unknown code of the file /include/controller/api_controller.php. The manipulation of the argument tag leads to sql injection. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure and confirmed the existence of the vulnerability.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
The DistroWatch news feed is brought to you by TUXEDO COMPUTERS. NixOS is an independently-developed GNU/Linux distribution that aims to improve the state of the art in system configuration management. The distribution’s latest release is version 25.05 “Warbler” which will be supported until the end of 2025. The project’s release announcement mentions some key highlights, including the availability of….
extundelete is designed to undelete files from an unmounted partition to a separate (mounted) partition. The post extundelete recovers deleted…
CVE ID : CVE-2025-44998
Published : May 23, 2025, 7:15 p.m. | 1 hour, 38 minutes ago
Description : A stored cross-site scripting (XSS) vulnerability in the component /tinyfilemanager.php of TinyFileManager v2.4.7 allows attackers to execute arbitrary JavaScript or HTML via injecting a crafted payload into the js-theme-3 parameter.
Severity: 6.1 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-46176
Published : May 23, 2025, 7:15 p.m. | 1 hour, 38 minutes ago
Description : Hardcoded credentials in the Telnet service in D-Link DIR-605L v2.13B01 and DIR-816L v2.06B01 allow attackers to remotely execute arbitrary commands via firmware analysis.
Severity: 6.5 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-48735
Published : May 23, 2025, 8:15 p.m. | 37 minutes ago
Description : A SQL Injection issue in the request body processing in BOS IPCs with firmware 21.45.8.2.2_220219 before 21.45.8.2.3_230220 allows remote attackers to obtain sensitive information from the database via crafted input in the request body.
Severity: 4.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-48738
Published : May 23, 2025, 8:15 p.m. | 37 minutes ago
Description : An e-mail flooding vulnerability in StrangeBee TheHive 5.2.0 before 5.2.16, 5.3.0 before 5.3.11, 5.4.0 before 5.4.10, and 5.5.0 before 5.5.1 allows unauthenticated remote attackers to use the password reset feature without limits. This can lead to several consequences, including mailbox storage exhaustion for targeted users, reputation damage to the SMTP server, potentially causing it to be blacklisted, and overload of the SMTP server’s outbound mail queue.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-48739
Published : May 23, 2025, 8:15 p.m. | 37 minutes ago
Description : A Server-Side Request Forgery (SSRF) vulnerability in StrangeBee TheHive 5.2.0 before 5.2.16, 5.3.0 before 5.3.11, 5.4.0 before 5.4.10, and 5.5.0 before 5.5.1 allows remote authenticated attackers with admin permissions (allowing them to access specific API endpoints) to manipulate URLs to direct requests to unexpected hosts or ports. This allows the attacker to use a TheHive server as a proxy to reach internal or otherwise restricted resources. This could be exploited to access other servers on the internal network.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-48740
Published : May 23, 2025, 8:15 p.m. | 37 minutes ago
Description : A Cross-Site Request Forgery (CSRF) vulnerability in StrangeBee TheHive 5.2.0 before 5.2.16, 5.3.0 before 5.3.11, 5.4.0 before 5.4.10, and 5.5.0 before 5.5.1 allows a remote attacker to trigger requests on their victim’s behalf, if the attacker lures a privileged user, authenticated with basic authentication.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-48741
Published : May 23, 2025, 8:15 p.m. | 37 minutes ago
Description : A Broken Access Control vulnerability in StrangeBee TheHive 5.2.0 before 5.2.16, 5.3.0 before 5.3.11, and 5.4.0 before 5.4.10 allows remote, authenticated, and unprivileged users to retrieve alerts, cases, logs, observables, or tasks, regardless of the user’s permissions, through a specific API endpoint.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5112
Published : May 23, 2025, 2:15 p.m. | 4 hours, 37 minutes ago
Description : A vulnerability, which was classified as critical, was found in FreeFloat FTP Server 1.0. This affects an unknown part of the component MGET Command Handler. The manipulation leads to buffer overflow. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2023-53154
Published : May 23, 2025, 4:15 p.m. | 2 hours, 37 minutes ago
Description : parse_string in cJSON before 1.7.18 has a heap-based buffer over-read via {“1”:1, with no trailing newline if cJSON_ParseWithLength is called.
Severity: 2.9 | LOW
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2024-48704
Published : May 23, 2025, 4:15 p.m. | 2 hours, 37 minutes ago
Description : Phpgurukul Medical Card Generation System v1.0 is vulnerable to HTML Injection in admin/contactus.php via the parameter pagedes.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…