Reminiscence was designed for saving personal memories of the web effectively and in a well organized manner. The post Reminiscence…
CVE ID : CVE-2025-5131
Published : May 24, 2025, 9:15 p.m. | 3 hours, 39 minutes ago
Description : A vulnerability was found in Tmall Demo up to 20250505. It has been declared as critical. This vulnerability affects the function uploadCategoryImage of the file tmall/admin/uploadCategoryImage. The manipulation of the argument File leads to unrestricted upload. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. Continious delivery with rolling releases is used by this product. Therefore, no version details of affected nor updated releases are available. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 4.7 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5132
Published : May 24, 2025, 9:15 p.m. | 3 hours, 39 minutes ago
Description : A vulnerability was found in Tmall Demo up to 20250505. It has been rated as problematic. This issue affects some unknown processing of the file tmall/admin/account/logout. The manipulation leads to cross-site request forgery. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used. This product does not use versioning. This is why information about affected and unaffected releases are unavailable. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 4.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5133
Published : May 24, 2025, 10:15 p.m. | 2 hours, 39 minutes ago
Description : A vulnerability classified as problematic has been found in Tmall Demo up to 20250505. Affected is an unknown function of the component Search Box. The manipulation leads to cross site scripting. It is possible to launch the attack remotely. The exploit has been disclosed to the public and may be used. This product is using a rolling release to provide continious delivery. Therefore, no version details for affected nor updated releases are available. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 4.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5134
Published : May 24, 2025, 10:15 p.m. | 2 hours, 39 minutes ago
Description : A vulnerability classified as problematic was found in Tmall Demo up to 20250505. Affected by this vulnerability is an unknown functionality of the component Buy Item Page. The manipulation of the argument Detailed Address leads to cross site scripting. The attack can be launched remotely. The exploit has been disclosed to the public and may be used. This product takes the approach of rolling releases to provide continious delivery. Therefore, version details for affected and updated releases are not available. Other parameters might be affected as well. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 3.5 | LOW
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5135
Published : May 24, 2025, 11:15 p.m. | 1 hour, 39 minutes ago
Description : A vulnerability, which was classified as problematic, has been found in Tmall Demo up to 20250505. Affected by this issue is some unknown functionality of the file /tmall/admin/ of the component Product Details Page. The manipulation of the argument Product Name/Product Title leads to cross site scripting. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. Continious delivery with rolling releases is used by this product. Therefore, no version details of affected nor updated releases are available. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 2.4 | LOW
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5136
Published : May 25, 2025, 12:15 a.m. | 39 minutes ago
Description : A vulnerability, which was classified as problematic, was found in Tmall Demo up to 20250505. This affects an unknown part of the file /tmall/order/pay/ of the component Payment Identifier Handler. The manipulation leads to insufficiently random values. It is possible to initiate the attack remotely. The complexity of an attack is rather high. The exploitability is told to be difficult. The exploit has been disclosed to the public and may be used. This product does not use versioning. This is why information about affected and unaffected releases are unavailable. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 3.7 | LOW
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5137
Published : May 25, 2025, 12:15 a.m. | 39 minutes ago
Description : A vulnerability was found in DedeCMS 5.7.117. It has been classified as critical. Affected is an unknown function of the file dede/sys_verifies.php?action=getfiles of the component Incomplete Fix CVE-2018-9175. The manipulation of the argument refiles leads to code injection. It is possible to launch the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 4.7 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
Open-Typer is an open source typing tutor application which aims to make learning to touch type easier. The post Open-Typer…
RefreshOS ims to provide a modern computing experience with a focus on stability, customization, and the seamless integration of Qt…
CVE ID : CVE-2025-5127
Published : May 24, 2025, 4:15 p.m. | 4 hours, 39 minutes ago
Description : A vulnerability, which was classified as problematic, has been found in FLIR AX8 up to 1.46.16. This issue affects some unknown processing of the file /prod.php. The manipulation of the argument cmd leads to cross site scripting. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 3.5 | LOW
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5128
Published : May 24, 2025, 4:15 p.m. | 4 hours, 39 minutes ago
Description : A vulnerability, which was classified as critical, was found in ScriptAndTools Real-Estate-website-in-PHP 1.0. Affected is an unknown function of the file /admin/ of the component Admin Login Panel. The manipulation of the argument Password leads to sql injection. It is possible to launch the attack remotely. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5129
Published : May 24, 2025, 5:15 p.m. | 3 hours, 39 minutes ago
Description : A vulnerability has been found in Sangfor 零信任访问控制系统 aTrust 2.3.10.60 and classified as critical. Affected by this vulnerability is an unknown functionality in the library MSASN1.dll. The manipulation leads to uncontrolled search path. Local access is required to approach this attack. The complexity of an attack is rather high. The exploitation appears to be difficult. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 7.0 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5130
Published : May 24, 2025, 8:15 p.m. | 39 minutes ago
Description : A vulnerability was found in Tmall Demo up to 20250505. It has been classified as critical. This affects the function uploadProductImage of the file tmall/admin/uploadProductImage. The manipulation of the argument File leads to unrestricted upload. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used. This product takes the approach of rolling releases to provide continious delivery. Therefore, version details for affected and updated releases are not available. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 4.7 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
Cosmicding is a linkding companion app for COSMIC Desktop Environment. It provides an alternative frontend to linkding based on libcosmic.…
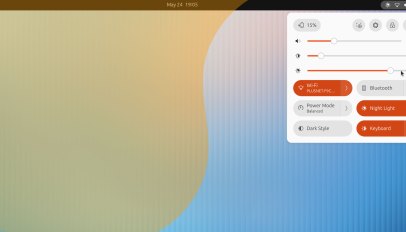
No need to hunt through GNOME Settings to adjust Night Light temperature intensity as this nifty extension adds an intensity…
CVE ID : CVE-2025-5124
Published : May 24, 2025, 1:15 p.m. | 3 hours, 45 minutes ago
Description : A vulnerability classified as critical has been found in Sony SNC-M1, SNC-M3, SNC-RZ25N, SNC-RZ30N, SNC-DS10, SNC-CS3N and SNC-RX570N up to 1.30. This affects an unknown part of the component Administrative Interface. The manipulation leads to use of default credentials. It is possible to initiate the attack remotely. The complexity of an attack is rather high. The exploitability is told to be difficult. The exploit has been disclosed to the public and may be used. The real existence of this vulnerability is still doubted at the moment. It is recommended to change the configuration settings. The vendor was contacted early about this issue. They confirmed the existence but pointed out that they “have published the ‘Hardening Guide’ on the Web from July 2018 to January 2025 and have thoroughly informed customers of the recommendation to change their initial passwords”.
Severity: 8.1 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5126
Published : May 24, 2025, 3:15 p.m. | 27 minutes ago
Description : A vulnerability classified as critical was found in FLIR AX8 up to 1.46.16. This vulnerability affects the function setDataTime of the file usrwwwapplicationmodelssettingsregional.php. The manipulation of the argument year/month/day/hour/minute leads to command injection. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
A prominent area of exploration involves enabling large language models (LLMs) to function collaboratively. Multi-agent systems powered by LLMs are…
I want to do API testing adding Assertions to the response. Can JMETER be used for this? The assertion would be added on an array of multiple ids. Is there a limit to the number of ids in the groovy script that need to be validated with assertion?
Also I used bunch of request payloads as csv input file for load test, how do I addd asserrtions for the multiple responses?