MidnightBSD is a BSD-derived operating system developed with desktop users in mind. It includes all the software you’d expect for…
Ogni settimana, il mondo del software libero e open source ci offre una moltitudine di aggiornamenti e nuove versioni di…
Ygt is a Python app for hinting TrueType fonts. It is built to be fast, flexible, and open source. The…
Gli sviluppatori di AerynOS, precedentemente noto come SerpentOS, hanno pubblicato un articolo dettagliato che illustra il concetto e l’implementazione tecnica…
CVE ID : CVE-2025-5145
Published : May 25, 2025, 6:15 a.m. | 2 hours, 40 minutes ago
Description : A vulnerability, which was classified as critical, was found in Netcore NBR1005GPEV2, B6V2, COVER5, NAP830, NAP930, NBR100V2, NBR200V2 and POWER13 up to 20250508. This affects an unknown part of the file /www/cgi-bin/ of the component Query String Handler. The manipulation leads to command injection. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 6.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5146
Published : May 25, 2025, 7:15 a.m. | 1 hour, 40 minutes ago
Description : A vulnerability has been found in Netcore NBR1005GPEV2, B6V2, COVER5, NAP830, NAP930, NBR100V2 and NBR200V2 up to 20250508 and classified as critical. This vulnerability affects the function passwd_set of the file /usr/bin/routerd of the component HTTP Header Handler. The manipulation of the argument pwd leads to command injection. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used.
Severity: 6.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
Roblox è una piattaforma di gioco online e un sistema di sviluppo per la creazione di videogiochi, sviluppata nel 2004…
A personal information manager (often known as a PIM tool) is a type of collaborative software that can help you…
CVE ID : CVE-2025-5138
Published : May 25, 2025, 1:15 a.m. | 3 hours, 48 minutes ago
Description : A vulnerability was found in Bitwarden up to 2.25.1. It has been declared as problematic. Affected by this vulnerability is an unknown functionality of the component PDF File Handler. The manipulation leads to cross site scripting. The attack can be launched remotely. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 3.5 | LOW
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5139
Published : May 25, 2025, 1:15 a.m. | 3 hours, 48 minutes ago
Description : A vulnerability was found in Qualitor 8.20. It has been rated as critical. Affected by this issue is some unknown functionality of the file /html/ad/adconexaooffice365/request/testaConexaoOffice365.php. The manipulation of the argument nmconexao leads to command injection. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5140
Published : May 25, 2025, 2:15 a.m. | 2 hours, 48 minutes ago
Description : A vulnerability classified as critical has been found in Seeyon Zhiyuan OA Web Application System up to 8.1 SP2. This affects the function this.oursNetService.getData of the file comourswwwehropenPlatform1open4ClientTypecontrollerThirdMenuController.class. The manipulation of the argument url leads to server-side request forgery. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 6.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
If you think AI website builders are plug-and-play, think again. My in-depth test revealed inconsistent tools, missed opportunities, and a…
The dream of launching a successful YouTube channel often hits a wall of perceived complexities: scripting, filming, editing, voiceovers, and…
ESET Research has been tracking Danabot’s activity since 2018 as part of a global effort that resulted in a major…
Post Content Source: Read MoreÂ
Post Content Source: Read MoreÂ
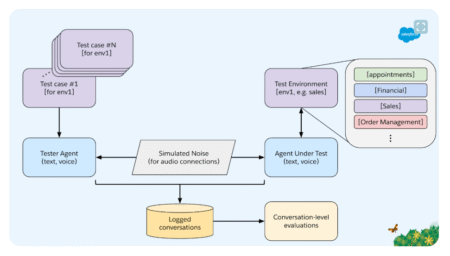
As businesses increasingly integrate AI assistants, assessing how effectively these systems perform real-world tasks, particularly through voice-based interactions, is essential.…
In this tutorial, we demonstrated how Microsoft’s AutoGen framework empowers developers to orchestrate complex, multi-agent workflows with minimal code. By…
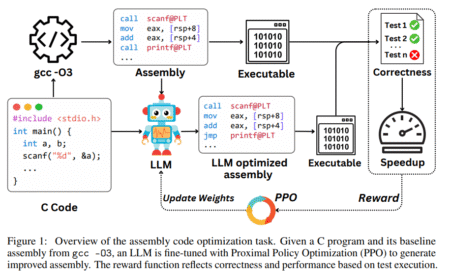
LLMs have shown impressive capabilities across various programming tasks, yet their potential for program optimization has not been fully explored.…
In this comprehensive tutorial, we guide users through creating a powerful multi-tool AI agent using LangGraph and Claude, optimized for…