Top News The 15 biggest announcements at Google I/O 2025 Google’s I/O 2025 conference included a ton of exciting new…
Latest PEAR Releases: Crypt_GPG 1.6.11 Source: Read MoreÂ
Laravel’s existsOr method enables elegant handling of non-existent model queries by executing closures when no results are found. This feature…
Volet is an extensible customer feedback widget for Laravel The post Volet is a Customer Feedback Widget for Laravel appeared…
According to a recent survey, 40% of software engineering managers anticipate that AI will drastically change the skills needed to…
Five major banking associations have formally petitioned the U.S. Securities and Exchange Commission (SEC) to repeal a rule that mandates…
Cyber threats don’t show up one at a time anymore. They’re layered, planned, and often stay hidden until it’s too…
Are your web privacy controls protecting your users, or just a box-ticking exercise? This CISO’s guide provides a practical roadmap…
Nova Scotia Power has confirmed it was the victim of a ransomware attack, weeks after initially alerting customers to a…
A wedding is a special occasion filled with emotions and lasting memories. While the couple’s love makes the day unique,…
There’s more than one way to accomplish your design and functionality goals with WordPress. You’ll find multiple themes and plugins…
Post Content Source: Read MoreÂ
Post Content Source: Read MoreÂ
Post Content Source: Read MoreÂ
Post Content Source: Read MoreÂ
Post Content Source: Read MoreÂ
Post Content Source: Read MoreÂ
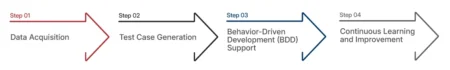
Tx-GPT is an in-house AI Agent by Txlabs that up-scales software testing by converting user stories into detailed, actionable test cases. Designed for QA modernization, it enhances test coverage, automates repetitive tasks, and integrates seamlessly with ALM tools like Azure Test Plans.
The post Tx-GPT: Turning User Stories into QA Action Using AI first appeared on TestingXperts.
CVE ID : CVE-2025-41654
Published : May 26, 2025, 9:15 a.m. | 1 hour, 59 minutes ago
Description : An unauthenticated remote attacker can access information about running processes via the SNMP protocol. The amount of returned data can trigger a reboot by the watchdog.
Severity: 8.2 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-1985
Published : May 26, 2025, 9:15 a.m. | 2 hours, 52 minutes ago
Description : Due to improper neutralization of input during web page generation (XSS) an unauthenticated remote attacker can inject HTML code into the Web-UI in the affected device.
Severity: 6.1 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…