During Gamescom 2025, Double Fine’s Tim Schafer confirmed that the studio is working on multiple games in addition to the…
The Battlefield 6 Open Beta is over, but a massive BF2042 update has given me and many other players away…
Two of the best 14-inch gaming laptops have now been tested and reviewed here at Windows Central, and I take…
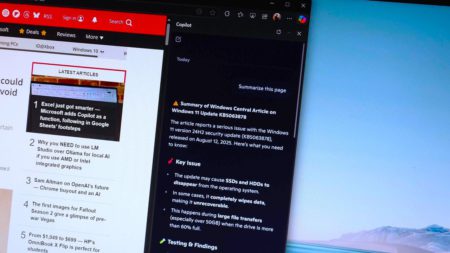
Using Copilot to summarize web articles is one of my favorite features. I tried to replicate it using an on-device…
There’s a lot to unpack from the Fallout Season 2 trailer, with numerous glimpses of characters and factions that imply…
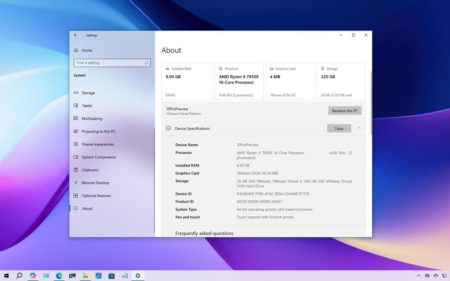
Windows 10 new features and changes you missed in updates since version 22H2, including the About page redesign, Taskbar changes,…
GitHub Copilot users, at least, the premium ones, will now be able to use Google Gemini 2.5 Pro for all…
We take our first look at how Microsoft is improving and optimizing Windows 11 for small handheld gaming PCs like…
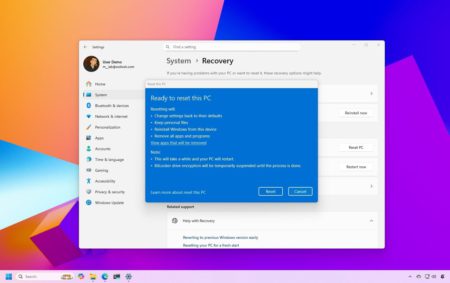
A bug in Windows 11 and 10 stops PCs from resetting or recovering. Microsoft has issued an update to fix…
Microsoft AI CEO Mustafa Suleyman recently raised the importance of building AI for people, not to be a person, suggesting…
Square Enix has made a surprising Gamescom 2025 announcement — shadow-dropping Triangle Strategy, the hit Strategy-RPG from 2022, onto Xbox…
During a special presentation on Thursday, Team Cherry confirmed that Hollow Knight: Silksong finally has a release date of Sept.…
Ubisoft has used the first of its Gamescom streams for The Division 2 to outline what’s coming next, including the…
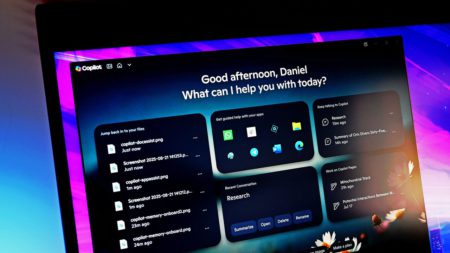
The latest Copilot app update for Windows 11 brings a calmer UI, quick access to recent files, app-specific vision, and…
A major breach of Microsoft’s SharePoint platform has triggered a cybersecurity crackdown, and Chinese companies are now locked out of…
Nearly a week after the end of the Battlefield 6 Open Beta weekends, the game’s developers have announced changes being…
At least 18 protesters were arrested at Microsoft headquarters after police said the group became aggressive during Israel genocide protests.…
AXL is a towering Tarantula that’s coming to Grounded 2, and Obsidian Entertainment has provided an official first-look. Source: Read…
Bungie CEO Pete Parsons is stepping down, with the iconic game developer now being led by Justin Truman. Source: Read…
Concept designer AR 4789 dared to dream big, sharing his vision for the next evolution of Windows, Windows 12.2, which…