In the fast-evolving landscape of the automotive industry, software is no longer an accessory, it’s the engine of transformation. From…
Post Content Source: Read MoreÂ
Post Content Source: Read MoreÂ
Post Content Source: Read MoreÂ
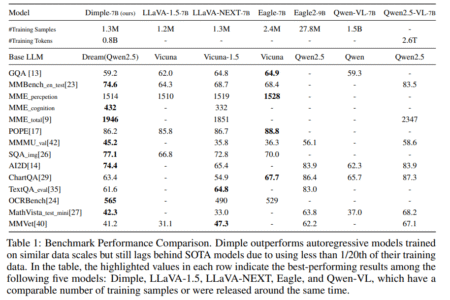
In recent months, there has been growing interest in applying diffusion models—originally designed for continuous data, such as images—to natural…
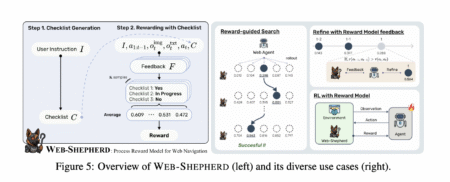
Web navigation focuses on teaching machines how to interact with websites to perform tasks such as searching for information, shopping,…
CVE ID : CVE-2025-48388
Published : May 29, 2025, 10:15 a.m. | 3 hours, 16 minutes ago
Description : FreeScout is a free self-hosted help desk and shared mailbox. Prior to version 1.8.178, the application performs insufficient validation of user-supplied data, which is used as arguments to string formatting functions. As a result, an attacker can pass a string containing special symbols (r, n, t)to the application. This issue has been patched in version 1.8.178.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-48045
Published : May 29, 2025, 1:15 p.m. | 16 minutes ago
Description : An unauthenticated HTTP GET request to the /client.php endpoint will disclose the default administrator user credentials.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-48046
Published : May 29, 2025, 1:15 p.m. | 16 minutes ago
Description : An authenticated user can disclose the cleartext password of a configured SMTP server via an HTTP GET request to the /config.php endpoint.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-48047
Published : May 29, 2025, 1:15 p.m. | 16 minutes ago
Description : An authenticated user can perform command injection via unsanitized input to the NetFax Server’s ping functionality via the /test.php endpoint.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
Built in two weeks from minimal assets, the OXI ONE MKII site used structure, type, and hustle to deliver a…
We focus on open source GUI-based bookmark managers. The featured let you effectively manage your bookmarks for websites. The post…
Nelson is a numerical computational language providing a comprehensive and intuitive environment for engineers, scientists, and students. The post Nelson…
Tails (The Amnesic Incognito Live System) è una distribuzione GNU/Linux basata su Debian progettata per garantire anonimato e riservatezza durante…
Agama, il nuovo programma di installazione in fase di sviluppo per le distribuzioni GNU/Linux di openSUSE, ha raggiunto la versione…
CVE ID : CVE-2024-52588
Published : May 29, 2025, 9:15 a.m. | 15 minutes ago
Description : Strapi is an open-source content management system. Prior to version 4.25.2, inputting a local domain into the Webhooks URL field leads to the application fetching itself, resulting in a server side request forgery (SSRF). This issue has been patched in version 4.25.2.
Severity: 4.9 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-27151
Published : May 29, 2025, 9:15 a.m. | 15 minutes ago
Description : Redis is an open source, in-memory database that persists on disk. In versions starting from 7.0.0 to before 8.0.2, a stack-based buffer overflow exists in redis-check-aof due to the use of memcpy with strlen(filepath) when copying a user-supplied file path into a fixed-size stack buffer. This allows an attacker to overflow the stack and potentially achieve code execution. This issue has been patched in version 8.0.2.
Severity: 4.7 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5122
Published : May 29, 2025, 9:15 a.m. | 15 minutes ago
Description : The Map Block Leaflet plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the ‘url’ parameter in all versions up to, and including, 3.2.1 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page.
Severity: 6.4 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4670
Published : May 29, 2025, 9:15 a.m. | 15 minutes ago
Description : The Easy Digital Downloads – eCommerce Payments and Subscriptions made easy plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin’s edd_receipt shortcode in all versions up to, and including, 3.3.8.1 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page.
Severity: 6.4 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4687
Published : May 29, 2025, 9:15 a.m. | 15 minutes ago
Description : In Teltonika Networks Remote Management System (RMS), it is possible to perform account pre-hijacking by misusing the invite functionality. If a victim has a pending invite and registers to the platform directly, they are added to the attackers company without their knowledge. The victims account and their company can then be managed by the attacker.This issue affects RMS: before 5.7.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…