At NodeSource, we’re excited to unveil a new feature in the N|Solid platform that takes Node.js application performance to a…
Comments Source: Read MoreÂ
In today’s world, the Internet of Things (IoT) is revolutionizing industries across the globe by connecting devices, systems, and people…
Introduction to Fastify (Node.Js Framework) Fastify is a fast and low-overhead web framework for Node.js that has gained popularity among…
The digital tide of Generative AI is sweeping across the globe, reshaping industries, revolutionizing creativity, and promising a future brimming…
Imagine you are retrieving an API key/Bearer token from an external system to make a new callout to another external…
Even highly capable teams with solid plans can fall into the same ol’ traps. It’s not really our fault, human…
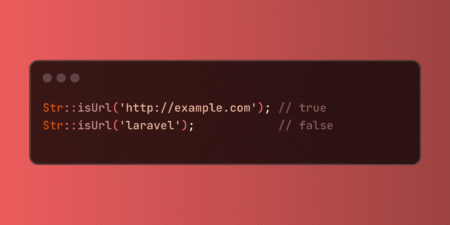
Laravel’s Str::isUrl method provides flexible URL validation with optional protocol restrictions. This utility simplifies verifying URL format and security requirements,…
Laravel’s diffKeys method identifies collection differences based on keys rather than values, enabling precise structural comparisons. This utility excels in…
The Laravel team released v12.16.0, with a fluent Rule::contains() validation rule, an “in_array_keys” validation rule, a new Arr::hasAll() method, and…
Useful Laravel links to read/watch for this week of May 29, 2025. Source: Read MoreÂ
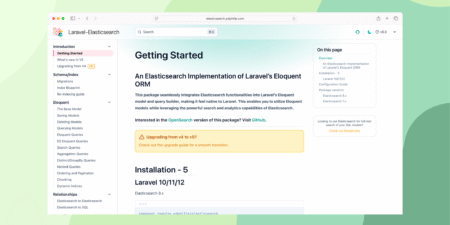
ElasticLens is a Laravel package that integrates Elasticsearch with Eloquent models. It provides advanced search capabilities while maintaining Laravel’s familiar…
The web is beginning to part ways with third-party cookies, a technology it once heavily relied on. Introduced in 1994…
Amazon has announced that Amazon Aurora DSQL is finally generally available after first being introduced as a preview at re:Invent…
New Relic has announced a new integration with GitHub Copilot’s coding agent. It provides monitoring of code deployments and can…
How AI is Reshaping Mobile App Development with React Native Page Updated On GET A FREE QUOTE Introduction: The Convergence…
Cybercriminals impersonate the trusted e-signature brand and send fake Docusign notifications to trick people into giving away their personal or…
Apple on Tuesday revealed that it prevented over $9 billion in fraudulent transactions in the last five years, including more…
Apple, in its latest App Store fraud analysis, revealed that the company prevented more than $2 billion in potentially fraudulent…
Cybersecurity researchers have disclosed details of a coordinated cloud-based scanning activity that targeted 75 distinct “exposure points” earlier this month.…