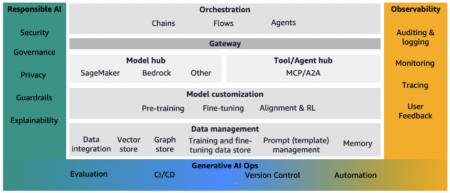
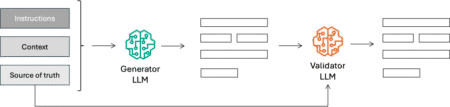
Generative AI applications seem simple—invoke a foundation model (FM) with the right context to generate a response. In reality, it’s…
Generative AI revolutionizes business operations through various applications, including conversational assistants such as Amazon’s Rufus and Amazon Seller Assistant. Additionally,…
ZURU Tech is on a mission to change the way we build, from town houses and hospitals to office towers,…
Amazon SageMaker Projects empower data scientists to self-serve Amazon Web Services (AWS) tooling and infrastructure to organize all entities of the…
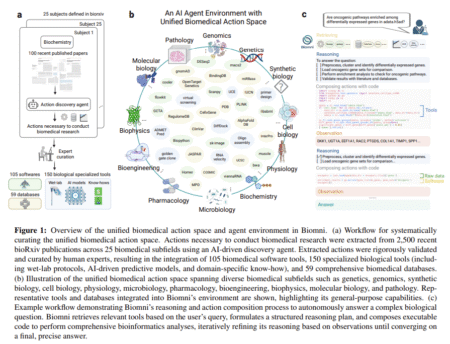
Biomedical research is a rapidly evolving field that seeks to advance human health by uncovering the mechanisms behind diseases, identifying…
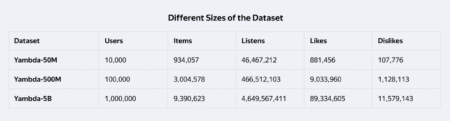
Yandex has recently made a significant contribution to the recommender systems community by releasing Yambda, the world’s largest publicly available…
I’m working with Java and REST Assured to test REST APIs. I was trying the example with JSON schema validation but it throws this error:
java.lang.IllegalArgumentException: Schema to use cannot be null
at io.restassured.module.jsv.JsonSchemaValidator.validateSchemaIsNotNull(JsonSchemaValidator.java:270)
at io.restassured.module.jsv.JsonSchemaValidator.access$300(JsonSchemaValidator.java:75)
at io.restassured.module.jsv.JsonSchemaValidator$JsonSchemaValidatorFactory.create(JsonSchemaValidator.java:281)
at io.restassured.module.jsv.JsonSchemaValidator.matchesJsonSchema(JsonSchemaValidator.java:166)
at io.restassured.module.jsv.JsonSchemaValidator.matchesJsonSchemaInClasspath(JsonSchemaValidator.java:117)
at suites.SchemaFollowupTest.ContractFollowUpTestSuccess(SchemaFollowupTest.java:44)
at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke0(Native Method)
at java.base/jdk.internal.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62)
My test code is:
given()
.header(“Content-Type”, ContentType.JSON)
//.header(“Authorization”, “Bearer ” + ConfigEnvironments.TOKEN_K8S)
.body(jsonBody)
.when()
.post(ConfigEnvironments.BASE_URL_CLAIMENGINE +”/api/v1/FollowUp”)
.then().log().all()
.statusCode(202)
.and()
.body(matchesJsonSchemaInClasspath(“src/test/resource/followup-schema.json”));
My strucuture folder is here:
[1]: https://i.sstatic.net/K9m2UjGy.png
CVE ID : CVE-2025-5364
Published : May 30, 2025, 10:15 p.m. | 3 hours, 26 minutes ago
Description : A vulnerability was found in Campcodes Online Hospital Management System 1.0 and classified as critical. Affected by this issue is some unknown functionality of the file /doctor/add-patient.php. The manipulation of the argument patname leads to sql injection. The attack may be launched remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2018-25111
Published : May 31, 2025, 1:15 a.m. | 26 minutes ago
Description : django-helpdesk before 1.0.0 allows Sensitive Data Exposure because of os.umask(0) in models.py.
Severity: 5.1 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5365
Published : May 31, 2025, 1:15 a.m. | 26 minutes ago
Description : A vulnerability was found in Campcodes Online Hospital Management System 1.0. It has been classified as critical. This affects an unknown part of the file /admin/patient-search.php. The manipulation of the argument searchdata leads to sql injection. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
DragonFly belongs to the same class of operating systems as other BSD-derived systems and Linux. It is based on the…
Oh My Posh is a custom prompt engine for any shell that has the ability to adjust the prompt string…
ConnectWise customers get mysterious warning about ‘sophisticated’ nation-state hack
ConnectWise has brought in the big guns to investigate a “sophisticated nation state actor” that broke into its IT environment and then breached some of its customers.
In a May 28 advisory, the IT man …
Read more
Published Date:
May 30, 2025 (2 hours, 51 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-3935
Hackers are exploiting critical flaw in vBulletin forum software
Two critical vulnerabilities affecting the open-source forum software vBulletin have been discovered, with one confirmed to be actively exploited in the wild.
The flaws, tracked under CVE-2025-48827 a …
Read more
Published Date:
May 30, 2025 (2 hours, 26 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-48828
CVE-2025-48827
CVE-2019-16759
‘Earth Lamia’ Exploits Known SQL, RCE Bugs Across Asia
Source: Frank Hecker via Alamy Stock PhotoA China-nexus threat actor behind the recent exploitation of SAP’s NetWeaver software is expanding its campaign, taking advantage of unpatched, Internet-expos …
Read more
Published Date:
May 30, 2025 (1 hour, 39 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-31324
CVE-2021-22205
CVE-2017-9805
CVE ID : CVE-2025-5358
Published : May 30, 2025, 6:15 p.m. | 3 hours, 25 minutes ago
Description : A vulnerability was found in PHPGurukul/Campcodes Cyber Cafe Management System 1.0. It has been rated as critical. Affected by this issue is some unknown functionality of the file /bwdates-reports-details.php. The manipulation of the argument fromdate/todate leads to sql injection. The attack may be launched remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-48883
Published : May 30, 2025, 7:15 p.m. | 2 hours, 25 minutes ago
Description : Chrome PHP allows users to start playing with chrome/chromium in headless mode from PHP. Prior to version 1.14.0, CSS Selector expressions are not properly encoded, which can lead to XSS (cross-site scripting) vulnerabilities. This is patched in v1.14.0. As a workaround, users can apply encoding manually to their selectors if they are unable to upgrade.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-48885
Published : May 30, 2025, 7:15 p.m. | 2 hours, 25 minutes ago
Description : application-urlshortener create shortened URLs for XWiki pages. Versions prior to 1.2.4 are vulnerable to users with view access being able to create arbitrary pages. Any user (even guests) can create these docs, even if they don’t exist already. This can enable guest users to denature the structure of wiki pages, by creating 1000’s of pages with random name, that then become very difficult to handle by admins. Version 1.2.4 fixes the issue. No known workarounds are available.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-48938
Published : May 30, 2025, 7:15 p.m. | 2 hours, 25 minutes ago
Description : go-gh is a collection of Go modules to make authoring GitHub CLI extensions easier. A security vulnerability has been identified in versions prior to 2.12.1 where an attacker-controlled GitHub Enterprise Server could result in executing arbitrary commands on a user’s machine by replacing HTTP URLs provided by GitHub with local file paths for browsing. In `2.12.1`, `Browser.Browse()` has been enhanced to allow and disallow a variety of scenarios to avoid opening or executing files on the filesystem without unduly impacting HTTP URLs. No known workarounds are available other than upgrading.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-48942
Published : May 30, 2025, 7:15 p.m. | 2 hours, 25 minutes ago
Description : vLLM is an inference and serving engine for large language models (LLMs). In versions 0.8.0 up to but excluding 0.9.0, hitting the /v1/completions API with a invalid json_schema as a Guided Param kills the vllm server. This vulnerability is similar GHSA-9hcf-v7m4-6m2j/CVE-2025-48943, but for regex instead of a JSON schema. Version 0.9.0 fixes the issue.
Severity: 6.5 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…