From a flurry of attacks targeting UK retailers to campaigns corralling end-of-life routers into botnets, it’s a wrap on another…
Quick thought from a conversation with friends Source: Read More
Can you even have architecture before there’s a team? Source: Read More
The customer experience (CX) paradigm within B2B technology is undergoing a substantive evolution, propelled by advances in agentic AI. Cisco’s…
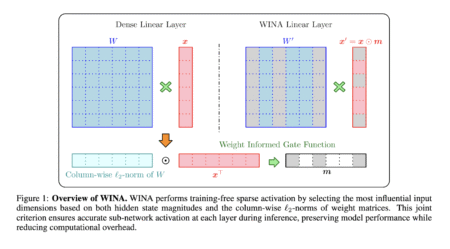
Large language models (LLMs), with billions of parameters, power many AI-driven services across industries. However, their massive size and complex…
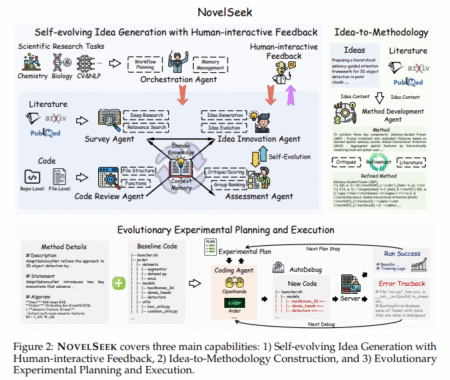
Scientific research across fields like chemistry, biology, and artificial intelligence has long relied on human experts to explore knowledge, generate…
The DistroWatch news feed is brought to you by TUXEDO COMPUTERS. A new stable release of PorteuX, a Slackware-based Linux distribution that means to be fast, small, portable, modular and immutable, is now available. PorteuX 2.1 introduces the brand-new 6.15 Linux kernel and delivers various bug fixes: “PorteuX 2.1. Nothing beats a new release where the system works better….
Ubuntu 25.10 will replace the sudo command with sudo-rs, a new Rust rewrite designed to improve memory safety and security.…
Compress is a tool for automatically creating typing shortcuts from a corpus of your own writing. The post Compress is…
New Apache InLong Vulnerability (CVE-2025-27522) Exposes Systems to Remote Code Execution Risks
A newly disclosed vulnerability, tracked as CVE-2025-27522, has been discovered in Apache InLong, a widely used real-time data streaming platform. The Apache InLong vulnerability introduces the potent …
Read more
Published Date:
May 30, 2025 (1 day, 10 hours ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-27522
CVE-2025-46762
CVE-2024-26579
CVE ID : CVE-2025-5387
Published : May 31, 2025, 6:15 p.m. | 2 hours, 43 minutes ago
Description : A vulnerability classified as critical has been found in JeeWMS up to 20250504. Affected is the function dogenerate of the file /generateController.do?dogenerate of the component File Handler. The manipulation leads to improper access controls. It is possible to launch the attack remotely. This product is using a rolling release to provide continious delivery. Therefore, no version details for affected nor updated releases are available.
Severity: 6.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5388
Published : May 31, 2025, 6:15 p.m. | 2 hours, 43 minutes ago
Description : A vulnerability classified as critical was found in JeeWMS up to 20250504. Affected by this vulnerability is the function dogenerate of the file /generateController.do?dogenerate. The manipulation leads to sql injection. The attack can be launched remotely. This product takes the approach of rolling releases to provide continious delivery. Therefore, version details for affected and updated releases are not available.
Severity: 6.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5389
Published : May 31, 2025, 7:15 p.m. | 1 hour, 43 minutes ago
Description : A vulnerability, which was classified as critical, has been found in JeeWMS up to 20250504. Affected by this issue is the function dogenerateOne2Many of the file /generateController.do?dogenerateOne2Many of the component File Handler. The manipulation leads to improper access controls. The attack may be launched remotely. Continious delivery with rolling releases is used by this product. Therefore, no version details of affected nor updated releases are available.
Severity: 6.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5390
Published : May 31, 2025, 7:15 p.m. | 1 hour, 43 minutes ago
Description : A vulnerability, which was classified as critical, was found in JeeWMS up to 20250504. This affects the function filedeal of the file /systemController/filedeal.do of the component File Handler. The manipulation leads to improper access controls. It is possible to initiate the attack remotely. This product does not use versioning. This is why information about affected and unaffected releases are unavailable.
Severity: 6.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
Supermodel emulates Sega’s Model 3 arcade platform, allowing you to play a number of ground-breaking arcade classics on your PC.…
My Journey to NASA’s Hall of Fame
My Journey to NASA’s Hall of FameHi, I’m Dharineesh, AKA Hack-Bat, and this is the story of how I ended up being listed in the NASA Hall of Fame. It wasn’t a smooth ride. The path was filled with long …
Read more
Published Date:
May 31, 2025 (5 hours, 21 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE ID : CVE-2025-5379
Published : May 31, 2025, 2:15 p.m. | 3 hours, 29 minutes ago
Description : A vulnerability classified as critical was found in NuCom NC-WR744G 8.5.5 Build 20200530.307. This vulnerability affects unknown code of the component Console Application. The manipulation of the argument CMCCAdmin/useradmin/CUAdmin leads to hard-coded credentials. The attack can be initiated remotely. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 4.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5380
Published : May 31, 2025, 2:15 p.m. | 3 hours, 29 minutes ago
Description : A vulnerability, which was classified as critical, has been found in ashinigit 天青一白 XueShengZhuSu 学生住宿管理系统 up to 4d3f0ada0e71482c1e51fd5f5615e5a3d8bcbfbb. This issue affects some unknown processing of the file /upload/ of the component Image File Upload. The manipulation of the argument File leads to path traversal. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used. This product takes the approach of rolling releases to provide continious delivery. Therefore, version details for affected and updated releases are not available.
Severity: 6.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5381
Published : May 31, 2025, 3:15 p.m. | 2 hours, 29 minutes ago
Description : A vulnerability, which was classified as problematic, was found in Yifang CMS up to 2.0.2. Affected is the function downloadFile of the file /api/File/downloadFile of the component Admin Panel. The manipulation of the argument File leads to path traversal. It is possible to launch the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 2.7 | LOW
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5383
Published : May 31, 2025, 3:15 p.m. | 2 hours, 29 minutes ago
Description : A vulnerability was found in Yifang CMS up to 2.0.2 and classified as problematic. Affected by this issue is some unknown functionality of the component Article Management Module. The manipulation of the argument Default Value leads to cross site scripting. The attack may be launched remotely. The exploit has been disclosed to the public and may be used.
Severity: 2.4 | LOW
Visit the link for more details, such as CVSS details, affected products, timeline, and more…