Read the All Part of Our Basic Networking Series Basic Networking Part 1 Basic Networking Part 2 Basic Networking Part…
Subdomain discovery is very essential for information gathering during penetration testing on web applications. There are lots of tools available…
The evolution of cyber threats has forced organizations across all industries to rethink their security strategies. As attackers become more…
The WordPress Block Editor is infinitely extensible. For instance, you can build custom blocks to suit your needs or create…
In their pursuit of modern standards, educational institutions face an important decision when adopting new software solutions: whether to host…
Post Content Source: Read MoreÂ
Post Content Source: Read MoreÂ
Post Content Source: Read MoreÂ
Post Content Source: Read MoreÂ
Post Content Source: Read MoreÂ
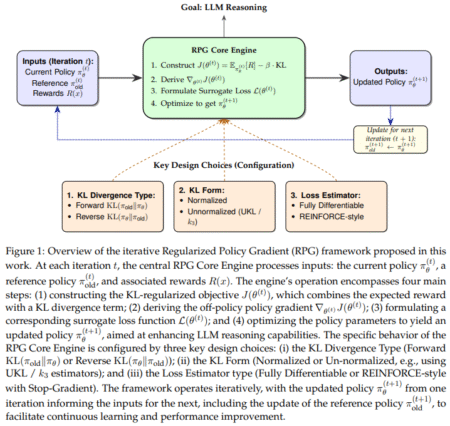
Policy gradient methods have significantly advanced the reasoning capabilities of LLMs, particularly through RL. A key tool in stabilizing these…
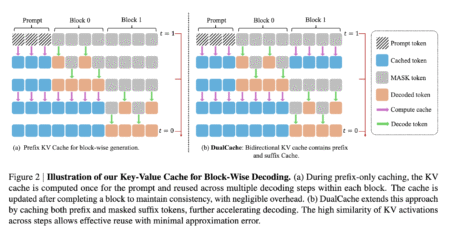
Diffusion-based large language models (LLMs) are being explored as a promising alternative to traditional autoregressive models, offering the potential for…
The blog discusses how Agentic AI can upscale DevSecOps by enabling autonomous security testing, continuous risk assessment, and intelligent decision-making within CI/CD pipelines. It proactively detects vulnerabilities, adapts testing workflows based on context, and supports instant incident response.
The post DevSecOps with Agentic AI: Autonomous Security Testing in CI/CD Pipelines first appeared on TestingXperts.
ncgopher is a gopher, gemini and finger client for the modern internet. It’s written in the Rust language. The post…
AxOS è una distribuzione GNU/Linux francese che si distingue per la sua attenzione all’efficienza e alla personalizzazione dell’ambiente desktop. Basata…
$540 Bounty: How a Misconfigured Warning Endpoint in Apache Airflow Exposed DAG Secrets
CVE-2023–42780: An Improper Access Control Bug That Let Low-Privileged Users View DAG Import Errors and Stack TracesIntroWhen it comes to access control, “read-only” shouldn’t mean “see everything.” B …
Read more
Published Date:
Jun 02, 2025 (4 hours, 49 minutes ago)
Vulnerabilities has been mentioned in this article.
Apple’s AI Race: Is the Tech Giant Falling Behind?
In his “Power On” column, Bloomberg journalist Mark Gurman reported that some Apple employees have expressed a sense of pessimism regarding the company’s progress in artificial intelligence developmen …
Read more
Published Date:
Jun 02, 2025 (4 hours, 38 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-40909
Red Hat Unveils llm-d: Scaling Generative AI for the Enterprise
Red Hat has recently unveiled an open-source initiative named llm-d, designed to address the most critical demand of the generative AI era: large-scale inference.
The llm-d project is a collaborative …
Read more
Published Date:
Jun 02, 2025 (4 hours, 30 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2024-0087
CVE-2025-4010: ONEKEY Uncovers Critical Remote Code Execution Flaw in Netcomm/Lantronix 4G Gateways
A newly disclosed vulnerability affecting Netcomm Wireless devices—now under Lantronix ownership—has been assigned CVE-2025-4010, and it poses a serious security risk to industrial and telecommunicati …
Read more
Published Date:
Jun 02, 2025 (3 hours, 49 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-4010
CISA Warns of Consilium Fire Panel Vulnerabilities Allowing Remote Takeover
CISA has issued a critical advisory warning of two severe security vulnerabilities affecting all versions of the Consilium Safety CS5000 Fire Panel, a widely deployed industrial control system used in …
Read more
Published Date:
Jun 02, 2025 (3 hours, 41 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-46352
CVE-2025-41438