“Your mind is the gateway to infinite possibilities. Once you understand the quantum nature of thought, you become unstoppable, a creator of your own…
“The universe doesn’t operate in a linear fashion. Every thought, every emotion, every intention creates a new parallel timeline. Your…
Apple has removed the “Available Now” label from its Apple Intelligence webpage after the National Advertising Division (NAD) deemed the…
From Exploration to Integration When the co-founder and “Senior Maverick” at Wired magazine, Kevin Kelly, speaks, you listen. In our…
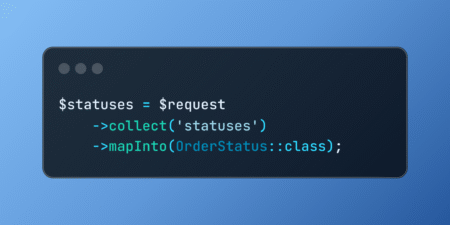
Discover how Laravel’s mapInto method simplifies converting array values into PHP enum instances, providing type-safe transformations that make handling user…
The Laravel team released v12.10.0, which includes mapping Eloquent attributes using the collection cast into a specific object, checking nested…
Software engineers are currently caught between a rock and a hard place. The rock? They’re under record pressure to produce…
Microsoft has announced that over the next several months it will be making a few changes to its Microsoft 365…
This article was adapted from an interview with Galileo’s Chain of Thought podcast. Watch the full episode on YouTube. At…
CMU researchers are presenting 143 papers at the Thirteenth International Conference on Learning Representations (ICLR 2025), held from April 24…
Build native iOS & Android apps using just Laravel. NativePHP for Mobile v1 release announcement— the same Laravel you’ve always…
So, you’re filling out an online form, and it asks you to upload a file. You click the input, select…
Google on Tuesday revealed that it will no longer offer a standalone prompt for third-party cookies in its Chrome browser…
The Ripple cryptocurrency npm JavaScript library named xrpl.js has been compromised by unknown threat actors as part of a software…
UK retail giant Marks & Spencer has confirmed it is managing a cybersecurity incident, following several days of service disruption…
Multiple suspected Russia-linked threat actors are “aggressively” targeting individuals and organizations with ties to Ukraine and human rights with an…
Phishing attacks remain a huge challenge for organizations in 2025. In fact, with attackers increasingly leveraging identity-based techniques over software…
Cybersecurity researchers have revealed that Russian military personnel are the target of a new malicious campaign that distributes Android spyware…
The Iran-nexus threat actor known as UNC2428 has been observed delivering a backdoor known as MURKYTOUR as part of a…
<p>This is a book for complete beginners to Apple’s modern programming language — Swift.</p> <p>All the code in the book…