Windows 11 KB5055629 23H2 is now available for everyone with a new Phone Link companion panel in the Start menu,…
Microsoft Edge is getting its first big “AI” upgrade, where Copilot is integrated into the New Tab Page (NTP). This…
Comments Source: Read MoreÂ
In the ever-evolving world of web development, the term “headless” is as popular today as it ever has been. But…
Multiple threat activity clusters with ties to North Korea (aka Democratic People’s Republic of Korea or DPRK) have been linked…
Graham explores how the Elusive Comet cybercrime gang are using a sneaky trick of stealing your cryptocurrency via an innocent-appearing…
Post Content Source: Read MoreÂ
Post Content Source: Read MoreÂ
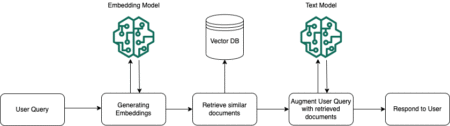
Retrieval Augmented Generation (RAG) applications have become increasingly popular due to their ability to enhance generative AI tasks with contextually…
Archival data in research institutions and national laboratories represents a vast repository of historical knowledge, yet much of it remains…
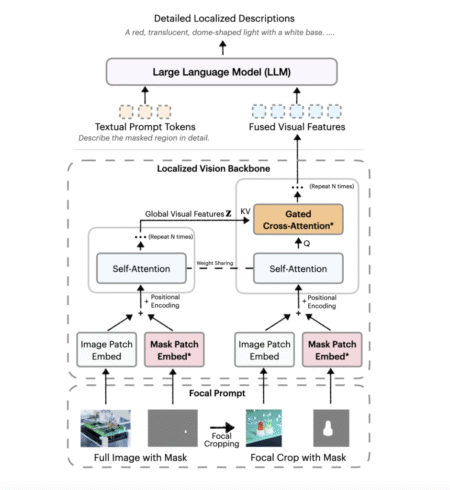
Challenges in Localized Captioning for Vision-Language Models Describing specific regions within images or videos remains a persistent challenge in vision-language…
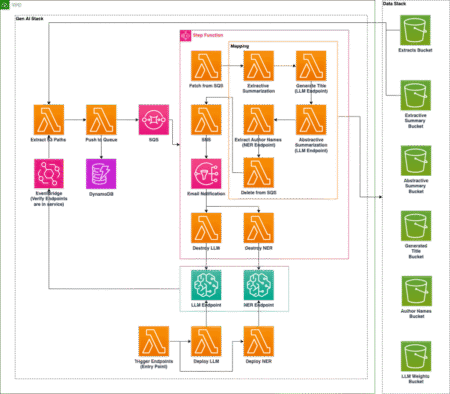
Xata Agent is an open-source AI assistant built to serve as a site reliability engineer for PostgreSQL databases. It constantly…
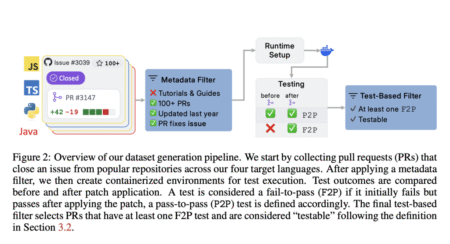
Recent advancements in large language models (LLMs) have enabled the development of AI-based coding agents that can generate, modify, and…
Ripple NPM supply chain attack hunts for private keys
Many versions of the Ripple ledger (XRPL) official NPM package are compromised with malware injected to steal cryptocurrency.
The NPM package, xrpl, is a JavaScript/TypeScript library that devs use to …
Read more
Published Date:
Apr 23, 2025 (5 hours, 4 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-32965
CVE ID : CVE-2025-3673
Published : April 23, 2025, 7:16 p.m. | 3 hours, 42 minutes ago
Description : Rejected reason: ** REJECT ** DO NOT USE THIS CANDIDATE NUMBER. ConsultIDs: CVE-2023-3092.. Reason: This candidate is a reservation duplicate of CVE-2023-3092. Notes: All CVE users should reference CVE-2023-3092. instead of this candidate. All references and descriptions in this candidate have been removed to prevent accidental usage.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-28169
Published : April 23, 2025, 8:15 p.m. | 2 hours, 43 minutes ago
Description : BYD QIN PLUS DM-i Dilink OS v3.0_13.1.7.2204050.1 to v3.0_13.1.7.2312290.1_0 was discovered to cend broadcasts to the manufacturer’s cloud server unencrypted, allowing attackers to execute a man-in-the-middle attack.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-32818
Published : April 23, 2025, 8:15 p.m. | 2 hours, 43 minutes ago
Description : A Null Pointer Dereference vulnerability in the SonicOS SSLVPN Virtual office interface allows a remote, unauthenticated attacker to crash the firewall, potentially leading to a Denial-of-Service (DoS) condition.
Severity: 7.5 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-46397
Published : April 23, 2025, 9:15 p.m. | 1 hour, 43 minutes ago
Description : Stack-overflow in fig2dev in version 3.2.9a allows an attacker possible code execution via local input manipulation via bezier_spline function.
Severity: 7.1 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-46398
Published : April 23, 2025, 9:15 p.m. | 1 hour, 43 minutes ago
Description : Stack-overflow in fig2dev in version 3.2.9a allows an attacker possible code execution via local input manipulation via read_objects function.
Severity: 7.1 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-46400
Published : April 23, 2025, 9:15 p.m. | 1 hour, 43 minutes ago
Description : Segmentation fault in fig2dev in version 3.2.9a allows an attacker to availability via local input manipulation via read_arcobject function.
Severity: 7.1 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…