On Wednesday, Microsoft announced new and updated AI-powered agents for Microsoft 365 Copilot Chat aimed at enterprise collaboration, project management,…
A ping reducer is the gamer’s best friend. Not only does it lower the response times from the PC to…
The j-Box component from the Total.js jComponent UI library is a versatile tool for creating customizable pop-up windows, such as…
If you are a Game of Thrones fan, you are probably familiar with the “winter is coming” phrase. When it…
Generate PDFs in Laravel with this mPDF wrapper. Source: Read MoreÂ
The work of a designer largely consists of inventing new things, which requires creativity that is generally believed to depend…
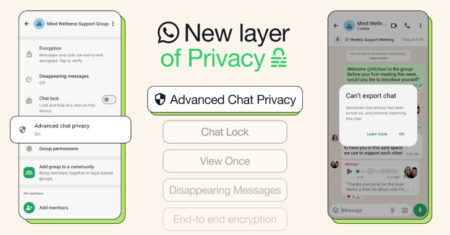
WhatsApp has introduced an extra layer of privacy called Advanced Chat Privacy that allows users to block participants from sharing…
Global payment platform Adyen has confirmed it was the target of a Distributed-Denial-of-Service (DDoS) attack on April 21, 2025, which…
The Federal Bureau of Investigation (FBI) has released its latest Internet Crime Report for 2024, revealing a steep rise in…
The United Kingdom communications regulator Ofcom has finalized a comprehensive set of child safety rules under the Online Safety Act,…
The Baltimore City Public Schools system has confirmed a cybersecurity incident that compromised the personal information of certain individuals associated…
The Evolving Healthcare Cybersecurity Landscape Healthcare organizations face unprecedented cybersecurity challenges in 2025. With operational technology (OT) environments increasingly targeted…
The threat actors behind the Darcula phishing-as-a-service (PhaaS) platform have released new updates to their cybercrime suite with generative artificial…
Chinese artificial intelligence startup DeepSeek has come under intense scrutiny from South Korean authorities for allegedly transferring user data and…
As many as 159 CVE identifiers have been flagged as exploited in the wild in the first quarter of 2025,…
Cybersecurity researchers have demonstrated a proof-of-concept (PoC) rootkit dubbed Curing that leverages a Linux asynchronous I/O mechanism called io_uring to…
Keeping your website secure is a 24/7 job. The right tools help keep watch – even when you can’t. They…
Thinking about getting out on the conference circuit, either as an attendee or a speaker? You should! Listen now for…
There’s nothing like the feeling of launching a new website. It’s the excitement of a happy client and a great…
Post Content Source: Read MoreÂ