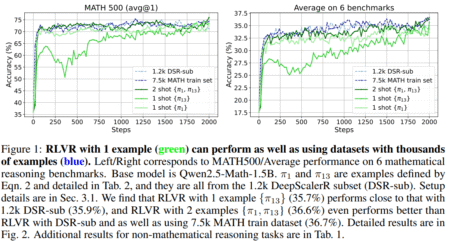
Recent advancements in LLMs such as OpenAI-o1, DeepSeek-R1, and Kimi-1.5 have significantly improved their performance on complex mathematical reasoning tasks.…
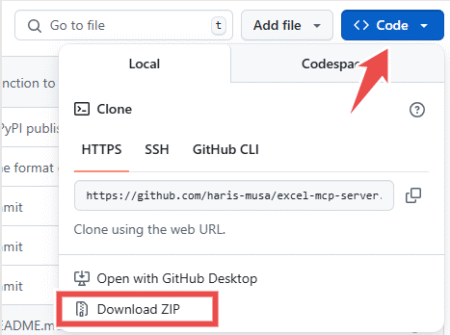
In this tutorial, we’ll build an MCP server that integrates Airbnb and Excel, and connect it with Cursor IDE. Using…
Manage your backup sources, backups, and repositories from either the TUI or CLI. The post BorgTUI is a TUI and…
Large language models (LLMs) have made significant strides in reasoning capabilities, exemplified by breakthrough systems like OpenAI o1 and DeepSeekR1,…
CVE ID : CVE-2024-58135
Published : May 3, 2025, 11:15 a.m. | 52 minutes ago
Description : Mojolicious versions from 7.28 through 9.39 for Perl may generate weak HMAC session secrets.
When creating a default app with the “mojo generate app” tool, a weak secret is written to the application’s configuration file using the insecure rand() function, and used for authenticating and protecting the integrity of the application’s sessions. This may allow an attacker to brute force the application’s session keys.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4226
Published : May 3, 2025, 11:15 a.m. | 52 minutes ago
Description : A vulnerability classified as critical has been found in PHPGurukul Cyber Cafe Management System 1.0. This affects an unknown part of the file /add-computer.php. The manipulation of the argument compname leads to sql injection. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
Il progetto KDE Plasma, uno degli ambienti desktop più apprezzati e utilizzati nel mondo delle distribuzioni GNU/Linux, ha annunciato un…
LPub3D is a WYSIWYG editing application for creating LEGO style digital building instructions. The post LPub3D is an LDraw editor…
Il panorama delle distribuzioni GNU/Linux e dei sistemi operativi alternativi si arricchisce con l’arrivo di Sculpt OS 25.04, una versione…
LiveKit is a project that provides scalable, multi-user conferencing based on WebRTC. The post LiveKit is an end-to-end stack for…
CVE ID : CVE-2025-3815
Published : May 3, 2025, 8:15 a.m. | 1 hour, 17 minutes ago
Description : The SurveyJS plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the ‘id’ parameter in all versions up to, and including, 1.12.32 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page.
Severity: 6.4 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
Tails, acronimo di The Amnesic Incognito Live System, è una distribuzione GNU/Linux progettata per offrire il massimo livello di anonimato…
In an earlier article, I discussed installing plugins and themes in Logseq. And you already know that there are plenty…
Peux OS is billed as a beautiful, minimal, secure, and highly customized Arch Linux distro. The post Peux OS is…
Apache Pinot is a real-time distributed OLAP datastore, built to deliver scalable real-time analytics with low latency. The post Pinot…
CVE ID : CVE-2024-13738
Published : May 3, 2025, 3:15 a.m. | 2 hours, 15 minutes ago
Description : The The Motors – Car Dealer, Rental & Listing WordPress theme theme for WordPress is vulnerable to arbitrary shortcode execution in all versions up to, and including, 5.6.65. This is due to the software allowing users to execute an action that does not properly validate a value before running do_shortcode. This makes it possible for unauthenticated attackers to execute arbitrary shortcodes.
*It is unclear exactly which version the issue was patched in from the changelog. Therefore, we used the latest version at the time of verification.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-3779
Published : May 3, 2025, 3:15 a.m. | 2 hours, 15 minutes ago
Description : The Personizely plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the ‘widgetId’ parameter in all versions up to, and including, 0.10 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page.
Severity: 6.4 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-3918
Published : May 3, 2025, 3:15 a.m. | 2 hours, 16 minutes ago
Description : The Job Listings plugin for WordPress is vulnerable to Privilege Escalation due to improper authorization within the register_action() function in versions 0.1 to 0.1.1. The plugin’s registration handler reads the client-supplied $_POST[‘user_role’] and passes it directly to wp_insert_user() without restricting to a safe set of roles. This makes it possible for unauthenticated attackers to elevate their privileges to that of an administrator.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-47229
Published : May 3, 2025, 3:15 a.m. | 2 hours, 15 minutes ago
Description : libpspp-core.a in GNU PSPP through 2.0.1 allows attackers to cause a denial of service (var_set_leave_quiet assertion failure and application exit) via crafted input data, such as data that triggers a call from src/data/dictionary.c code into src/data/variable.c code.
Severity: 2.9 | LOW
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4168
Published : May 3, 2025, 3:15 a.m. | 2 hours, 15 minutes ago
Description : The Subpage List plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin’s ‘subpages’ shortcode in all versions up to, and including, 1.3.3 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page.
Severity: 6.4 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…