Wifislax is a Slackware-based live distro containing a variety of security and forensics tools. The post Wifislax – Slackware-based live…
There are a number of free and open source applications for Linux which are credible alternatives to Google Earth. The…
Ogni settimana, il mondo del software libero e open source ci offre una moltitudine di aggiornamenti e nuove versioni di…
Negli ultimi anni, la sicurezza delle distribuzioni GNU/Linux è stata messa a dura prova da nuove tecniche di attacco che…
Facteur is a Gnome GTK app for sending template based emails. It’s written in JavaScript. The post Facteur is mail-merge…
Wine è un progetto open source che funge da compatibility layer, ovvero uno strato di compatibilità che permette di eseguire…
Ubuntu è una delle distribuzioni GNU/Linux più popolari e longeve, sviluppata dalla società Canonical. Ogni versione di Ubuntu porta con…
watchTowr Warns of Active Exploitation of SonicWall SMA 100 Devices
watchTowr reveals active exploitation of SonicWall SMA 100 vulnerabilities (CVE-2024-38475 & CVE-2023-44221) potentially leading to full system takeover and session hijacking. Learn about affected mod …
Read more
Published Date:
May 03, 2025 (4 hours, 5 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2024-38475
CVE-2023-44221
CVE-2025-2774: Webmin Vulnerability Allows Root-Level Privilege Escalation
Webmin, a popular web-based system administration tool used to manage Unix-like servers and various services with approximately 1,000,000 yearly installations worldwide, has been found to contain a cr …
Read more
Published Date:
May 04, 2025 (1 hour, 1 minute ago)
Vulnerabilities has been mentioned in this article.
CVE ID : CVE-2025-47244
Published : May 3, 2025, 11:15 p.m. | 2 hours, 16 minutes ago
Description : Inedo ProGet through 2024.22 allows remote attackers to reach restricted functionality through the C# reflection layer, as demonstrated by causing a denial of service (when an attacker executes a loop calling RestartWeb) or obtaining potentially sensitive information. Exploitation can occur if Anonymous access is enabled, or if there is a successful CSRF attack.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-47245
Published : May 4, 2025, 12:15 a.m. | 1 hour, 16 minutes ago
Description : In BlueWave Checkmate through 2.0.2 before d4a6072, an invite request can be modified to specify a privileged role.
Severity: 8.1 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
In 2020, Bing handled one search in sixteen searches (roughly), but today it handles one in eight (March 2025). To…
Comments Source: Read MoreÂ
Comments Source: Read MoreÂ
Electron wrapper for the NativePHP framework. Source: Read MoreÂ
From the power of collaborative defense to identity security and AI, catch up on the event’s key themes and discussions…
Post Content Source: Read MoreÂ
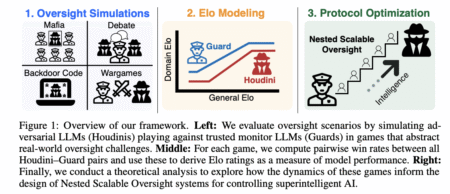
Frontier AI companies show advancement toward artificial general intelligence (AGI), creating a need for techniques to ensure these powerful systems…
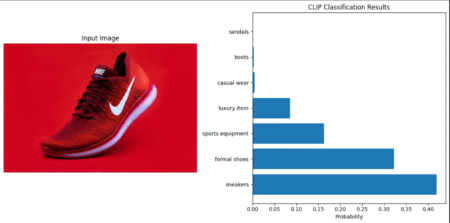
In this tutorial, we’ll explore implementing various vision foundation models for business applications. We’ll focus on practical code implementation, technical…
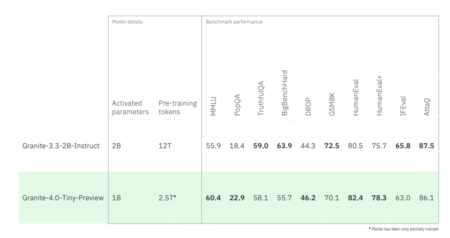
IBM has introduced a preview of Granite 4.0 Tiny, the smallest member of its upcoming Granite 4.0 family of language…