Using scroll shadows, especially for mobile devices, is a subtle bit of UX that Chris has covered before (indeed, it’s one…
A step-by-step guide to creating particle trails with TSL (Three.js Shader Language), simulating dynamic movement in 3D space. Source: Read…
Apache Parquet Java Vulnerability Let Attackers Execute Arbitrary Code
A new critical security vulnerability in Apache Parquet Java has been disclosed that could allow attackers to execute arbitrary code through specially crafted Parquet files.
The vulnerability, tracked …
Read more
Published Date:
May 05, 2025 (5 hours, 8 minutes ago)
Vulnerabilities has been mentioned in this article.
New SonicBoom Attack Allows Bypass of Authentication for Admin Access
A critical new attack chain, dubbed “SonicBoom,” that enables remote attackers to bypass authentication and seize administrative control over enterprise appliances, including SonicWall Secure Mobile A …
Read more
Published Date:
May 05, 2025 (2 hours, 50 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2025-23006
CVE-2024-38475
CVE-2023-44221
CVE ID : CVE-2025-4271
Published : May 5, 2025, 8:15 a.m. | 3 hours, 24 minutes ago
Description : A vulnerability was found in TOTOLINK A720R 4.1.5cu.374. It has been declared as problematic. Affected by this vulnerability is an unknown functionality of the file /cgi-bin/cstecgi.cgi. The manipulation of the argument topicurl with the input showSyslog leads to information disclosure. The attack can be launched remotely. The exploit has been disclosed to the public and may be used.
Severity: 5.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4270
Published : May 5, 2025, 8:15 a.m. | 3 hours, 24 minutes ago
Description : A vulnerability was found in TOTOLINK A720R 4.1.5cu.374. It has been classified as problematic. Affected is an unknown function of the file /cgi-bin/cstecgi.cgi of the component Config Handler. The manipulation of the argument topicurl with the input getInitCfg/getSysStatusCfg leads to information disclosure. It is possible to launch the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 5.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-2905
Published : May 5, 2025, 9:15 a.m. | 2 hours, 24 minutes ago
Description : An XML External Entity (XXE) vulnerability exists in the gateway component of WSO2 API Manager due to insufficient validation of XML input in crafted URL paths. User-supplied XML is parsed without appropriate restrictions, enabling external entity resolution.
This vulnerability can be exploited by an unauthenticated remote attacker to read files from the server’s filesystem or perform denial-of-service (DoS) attacks.
*
On systems running JDK 7 or early JDK 8, full file contents may be exposed.
*
On later versions of JDK 8 and newer, only the first line of a file may be read, due to improvements in XML parser behavior.
*
DoS attacks such as “Billion Laughs” payloads can cause service disruption.
Severity: 9.1 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-4272
Published : May 5, 2025, 11:15 a.m. | 24 minutes ago
Description : A vulnerability was found in Mechrevo Control Console 1.0.2.70. It has been rated as critical. Affected by this issue is some unknown functionality in the library C:Program FilesOEMMECHREVO Control CenterUniwillServiceMyControlCentercsCAPI.dll of the component GCUService. The manipulation leads to uncontrolled search path. An attack has to be approached locally. The complexity of an attack is rather high. The exploitation is known to be difficult. The exploit has been disclosed to the public and may be used.
Severity: 7.0 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
The biggest names in indie development come together to show off more than 40 new titles coming to Xbox and…
Microsoft is officially pulling the plug on Skype and recommends that its users transition to Teams. Source: Read More / Windows…
CEO Dario Amodei admits that the company doesn’t know precisely how its AI creations work. Source: Read More / Windows Central
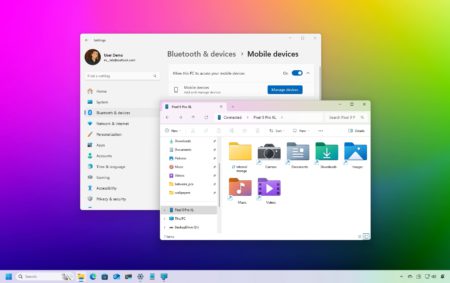
On Windows 11, you can connect your Android phone to your computer with the Phone Link app to access your…
Comments Source: Read MoreÂ
Comments Source: Read MoreÂ
Comments Source: Read MoreÂ
Microsoft 365 offers several types of groups; each designed for different collaboration and communication needs: Microsoft 365 Groups (M365): These…
Think about your past projects. Did they finish on time and on budget? Did they end up getting delivered without…
The threat actors known as Golden Chickens have been attributed to two new malware families dubbed TerraStealerV2 and TerraLogger, suggesting…
Artem Stryzhak, a Ukrainian national, has been extradited from Spain to the United States to face charges related to a…
As a designer, you spend most of your time doing actual design work. But there are so many other things…