In the wake of the Battlefield 6 Open Beta and criticisms of Call of Duty’s wacky over-the-top skins, the Black…
The highly anticipated Metal Gear Solid 3 remake, Metal Gear Solid Delta: Snake Eater, is finally here. But is it…
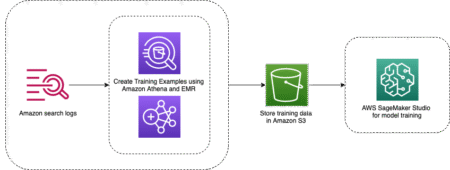
Healthcare discovery on ecommerce domains presents unique challenges that traditional product search wasn’t designed to handle. Unlike searching for books…
Let’s say you’ve built a fantastic machine learning model that performs beautifully in notebooks. But a model isn’t truly valuable…
Discover Generative Engine Optimization (GEO) – the next evolution beyond traditional SEO. Learn how to optimize your brand for AI-powered…
Unlock full-stack observability with frontend tracing using OpenTelemetry (OTel). Learn how to connect user interactions to backend services, debug slow…
Micro Frontend Architecture has become increasingly popular in recent years, as teams look to re-use parts of their existing applications…
Introduction With over 9+ years of experience in mobile development and a strong focus on React Native, I’ve always been…
How to monitor hundreds of Key Vaults across multiple subscriptions for just $15-25/month The Challenge: Key Vault Sprawl in Enterprise…
Azure Cosmos DB for NoSQL now supports hybrid search, it is a powerful feature that combines full-text search and vector…
At Perficient Hyderabad, excellence goes beyond the desk – into every serve, every strategy and every smash. This year’s Sports…
I presume that you are no stranger to the nightlight feature. It filters blue light from your screen and shifts…
The To-Do App using PHP and MySQL a simple yet powerful web-based application designed and developed using PHP and MySQL.…
A 26-year-old hacker, who breached websites in North America, Yemen, and Israel, and stole the details of millions of people…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added three security flaws impacting Citrix Session Recording and Git…
Google has announced plans to begin verifying the identity of all developers who distribute apps on Android, even for those…
Cybersecurity researchers have discovered a new variant of an Android banking trojan called HOOK that features ransomware-style overlay screens to…
Google’s Threat Intelligence Group has uncovered a cyber espionage campaign of a PRC-linked threat actor, which it tracks as UNC6384,…
A new large-scale campaign has been observed exploiting over 100 compromised WordPress sites to direct site visitors to fake CAPTCHA…
A suspected hacker, believed to be the mastermind behind an organised campaign of attacks that stole millions of dollars worth…