For the second time in 2025, Tomb Raider studio Crystal Dynamics has been hit with a wave of “necessary” layoffs.…
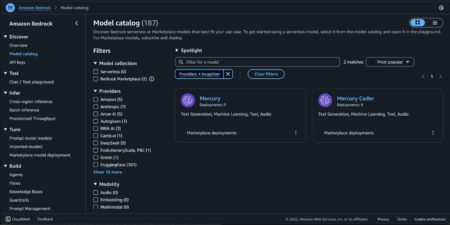
Today, we are excited to announce that Mercury and Mercury Coder foundation models (FMs) from Inception Labs are available through…
We just published a new course on the freeCodeCamp.org YouTube channel that mixes computer vision, deep learning, and Arduino into…
We just released a full course on the freeCodeCamp.org YouTube channel to help you prepare for the Google Cloud Professional…
Permissions are crucial when building mobile applications that require access to device features such as location, camera, contacts, microphone, storage,…
When you hear about Next.js, your first thought may be static websites or React-driven frontends. But that’s just part of…
If you have ever spent weeks hopping from one coding tutorial to another, only to freeze the moment you are…
Learn why ARM64 atomic instructions cause double page faults on Ampere CPUs, fragmenting huge pages and reducing performance. Explore the…
Do you want to improve you JavaScript skills and create 3D web experiences? We just posted a course on the…
The world of artificial intelligence moves fast. Every week, new models appear, older ones get better, and the tools to…
The move to SaaS is one of the biggest shifts happening in digital experience. It’s not just about technology, it’s…
On the hundredth anniversary of its circulation, Automotive News launched a series on the technological innovations driving the shift to…
Fedora is one of the most dependable Linux distro choices. It is cutting edge, backed by Red Hat, features newer…
The discovery of PromptLock shows how malicious use of AI models could supercharge ransomware and other threats Source: Read More
Cybersecurity researchers have discovered five distinct activity clusters linked to a persistent threat actor known as Blind Eagle between May…
A widespread data theft campaign has allowed hackers to breach sales automation platform Salesloft to steal OAuth and refresh tokens…
Employees are experimenting with AI at record speed. They are drafting emails, analyzing data, and transforming the workplace. The problem…
A threat activity cluster known as ShadowSilk has been attributed to a fresh set of attacks targeting government entities within…
Anthropic on Wednesday revealed that it disrupted a sophisticated operation that weaponized its artificial intelligence (AI)-powered chatbot Claude to conduct…
Cephalus is a relatively new ransomware operation that emerged in mid-2025, and has already been linked to a wave of…