Threat actors are exploiting a nearly two-year-old security flaw in Apache ActiveMQ to gain persistent access to cloud Linux systems…
Let’s be honest: Half the APIs you write are for a specific purpose in a specific component on a specific…
To create self-serve templates that bend—but don’t break—brand designers need to consider work through a marketing lens. Here’s how to…
Generative AI (genAI) is reshaping how people search for information. Anyone watching their content pageviews decline is currently experiencing the…
There’s some fun computational geometry in my latest artwork, and in this article I’ll walk through how I take a…
Motion is critical for how a product feels. It guides attention, reinforces brand personality, and can make an interface feel…
In this post, we highlight the desire to replace tokenization with a general method that better leverages compute and data.…
Across higher education globally, institutions are reimagining how to prepare students for a digital-first world. As part of that movement,…
Dribbble exists to help designers generate and convert leads. Our success depends on increasing both the number of designers who receive…
Navigating an unfamiliar city without the aid of Google Maps or any navigation tool can be a challenging experience. A…
Sometimes projects don’t go as planned. A Business Analyst leaves mid-sprint. The vendor you hired is missing in action. The…
Post Content Source: Read MoreÂ
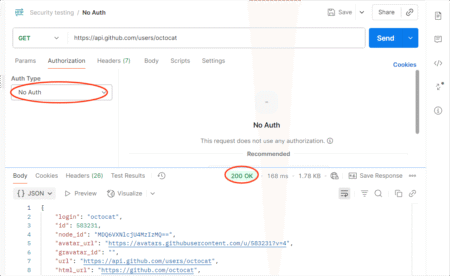
APIs (Application Programming Interfaces) have become the lifeblood of digital transformation. From mobile banking apps to enterprise SaaS platforms, APIs power the seamless flow of data between applications, services, and devices. However, with this power comes an equally significant risk: security vulnerabilities. A single exposed API can lead to massive data leaks, unauthorized access, and
The post Postman API Security Testing: A Complete Guide appeared first on Codoid.
Post Content Source: Read More
MongoDB is a NoSQL (non-relational) database. It stores data in a type of JSON format called BSON (Binary JSON). Unlike…
Comments Source: Read MoreÂ
Comments Source: Read MoreÂ
For decades, software testing has been built on a simple idea: humans write tests, machines run them. That model has…
Codeglide.ai, a subsidiary of the DevOps company Opsera, is launching its MCP server lifecycle platform that will enable developers to…
Black Duck adds new security app to GitHub Marketplace The Black Duck Security GitHub App enables static application security testing…