Veeam has rolled out patches to contain a critical security flaw impacting its Backup & Replication software that could result…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday placed a security flaw impacting the Linux kernel in its…
The ClickFix social engineering tactic as an initial access vector using fake CAPTCHA verifications increased by 517% between the second…
The U.S. is alleging that 25-year-old British national Kai West is the prolific hacker “IntelBroker.” IntelBroker was arrested in February,…
Cybersecurity researchers have disclosed a critical vulnerability in the Open VSX Registry (“open-vsx[.]org”) that, if successfully exploited, could have enabled…
Dive into rapid tech team growth at TechLeadConf 2025, featuring lessons from Swizec’s experience with Plasmidsaurus’s explosive expansion. Explore tech…
Yesterday I had lunch with a newly promoted lead and realized I have opinions on mentoring engineers. Here they are.…
Creating a standout portfolio or lookbook is essential for any creative professional. While starting from a blank page can be…
Beyond boosting efficiency, the strongest software developers use AI to explore the problem space and find more creative solutions. Figma’s…
After 6 months of hard work, we’re launching Flowbite Design System v3.0! – fully integrated native tokens and variables –…
34 lessons, Good design is imagination and inspiration, Creating design specs for development, Purposeful vs aesthetic naming, and more. Source:…
Post Content Source: Read MoreÂ
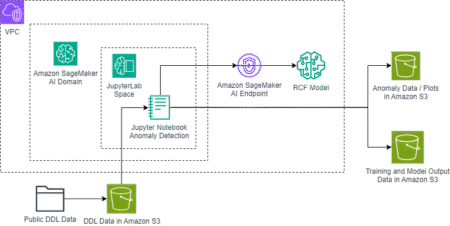
The successful deorbit, descent, and landing of spacecraft on the Moon requires precise control and monitoring of vehicle dynamics. Anomaly…
Generative AI is revolutionizing industries by streamlining operations and enabling innovation. While textual chat interactions with GenAI remain popular, real-world…
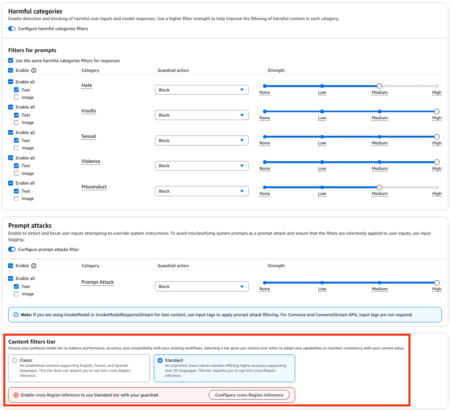
Amazon Bedrock Guardrails provides configurable safeguards to help build trusted generative AI applications at scale. It provides organizations with integrated…
With advances in generative AI, there is increasing work towards creating autonomous agents that can manage daily tasks by operating…
Egocentric Video Question Answering (QA) requires models to handle long-horizon temporal reasoning, first-person perspectives, and specialized challenges like frequent camera…
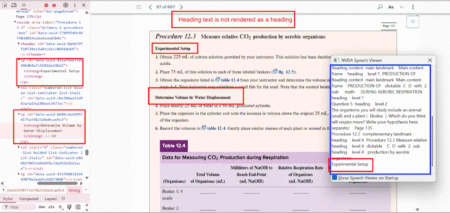
Ensuring accessibility is not just a compliance requirement but a responsibility. According to the World Health Organization (WHO), over 1 in 6 people globally live with some form of disability. These users often rely on assistive technologies like screen readers, keyboard navigation, and transcripts to access digital content. Unfortunately, many websites and applications fall short
The post Common Accessibility Issues: Real Bugs from Real Testing appeared first on Codoid.
The DistroWatch news feed is brought to you by TUXEDO COMPUTERS. Gursewak Sokhi has announced the release of Oracle Linux 10, a major new update of the company’s enterprise-class Linux distribution built from the source code of Red Hat Enterprise Linux 10: “Oracle Linux 10 is now generally available for 64-bit Intel and AMD (x86_64) and 64-bit Arm (aarch64)….
CVE ID : CVE-2025-49603
Published : June 26, 2025, 6:15 p.m. | 3 hours, 6 minutes ago
Description : Northern.tech Mender Server before 3.7.11 and 4.x before 4.0.1 has Incorrect Access Control.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…