Post Content Source: Read MoreÂ
Post Content Source: Read MoreÂ
Post Content Source: Read MoreÂ
Microsoft AI (MAI) has officially pulled back the curtain on the latest lineup of models, MAI-Voice-1 and MAI-1-preview. The first…
Cutting in Clipchamp means splitting a clip into smaller parts and removing the sections you don’t need. This is useful…
Minecraft snapshot is the best way to test new Minecraft features before they’re officially released. If you want early access…
For the last few days, many players have been experiencing “failed to fetch inventory” (or stuck on “Fetching account data…
Grok Code Fast 1 is a new reasoning model designed for agentic coding workflows, making coding tasks faster and more…
After introducing Copilot Vision, a screen analyzing tool with AI capabilities, Microsoft has a new product in testing. Windows Latest…
Microsoft has begun rolling out its annual feature update, Windows 11, version 25H2 (Build 26200.5074), to Insiders in the Release…
Over the last few days or so, Windows users have been frustrated about issues related to SSD and HDD failures…
Microsoft today released Windows 11 KB5064093 & KB5064089 to the Dev & Beta Channels, respectively. The latest update offers an…
With the release of the respective Windows 11 KB5064089 and KB5064093 updates to Beta & Dev channels, Microsoft is expanding…
Today, Microsoft released two new updates, KB5064093 and KB5064089, rolling out in the Dev and Beta channel for Windows 11…
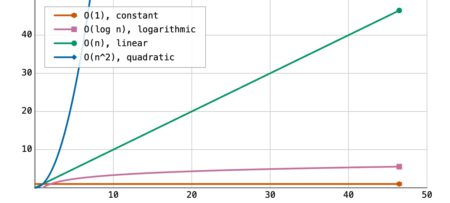
#750 — August 29, 2025 Read on the Web JavaScript Weekly An Illustrated Guide to Big O and Time Complexity…
Comments Source: Read MoreÂ
In “A Week In The Life Of An AI-Augmented Designer”, we followed Kate’s weeklong journey of her first AI-augmented design…
10 Reasons To Build a Full-stack Python Development Company Page Updated On GET A FREE QUOTE Best React.js Development Services…
Anthropic starts testing a Claude extension for Chrome The extension will enable Claude to take action on websites on behalf…
Over the weekend, I was looking to book flights for holidays. All excited, I was able to find a decent…