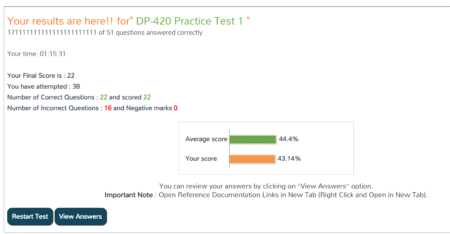
“These results are incomprensible,” Brian wrote testily. “The developers at SkillCertPro must use math derived from an entirely different universe…
Data breaches are a constant threat, and traditional encryption practices often aren’t enough to protect sensitive information throughout its entire…
The PHP team is pleased to announce the third beta release of PHP 8.5.0, Beta 3. This continues the PHP…
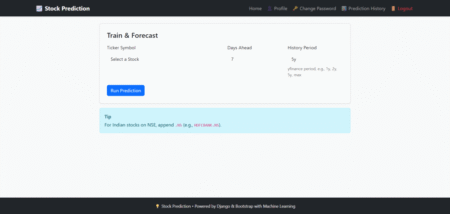
“Stock Prediction System using Python Machine Learning (ML)” is a web-based application that integrates machine learning with the Django framework.…
Upgrading Angular Applications: Angular 16 to Angular 17 Upgrading Angular applications to the latest version can sometimes be straightforward, but…
My 30-year technology career has taught me many things…and one big thing: the companies that treat technology as a cost…
Cybersecurity researchers have disclosed details of a new campaign that leverages ConnectWise ScreenConnect, a legitimate Remote Monitoring and Management (RMM)…
As bad actors often simply waltz through companies’ digital front doors with a key, here’s how to keep your own…
Cybersecurity researchers have disclosed two new campaigns that are serving fake browser extensions using malicious ads and fake websites to…
CISOs know their field. They understand the threat landscape. They understand how to build a strong and cost-effective security stack.…
Threat actors affiliated with the Akira ransomware group have continued to target SonicWall devices for initial access. Cybersecurity firm Rapid7…
The Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC) has issued an urgent alert regarding active exploitation of a…
A fresh firestorm has erupted over Microsoft’s handling of cybersecurity risks, with U.S. Senator Ron Wyden (D-OR) calling on the…
SAP has released a new security update addressing a broad range of vulnerabilities across its product ecosystem. Among the most…
U.S. Senator Ron Wyden has called on the Federal Trade Commission (FTC) to probe Microsoft and hold it responsible for…
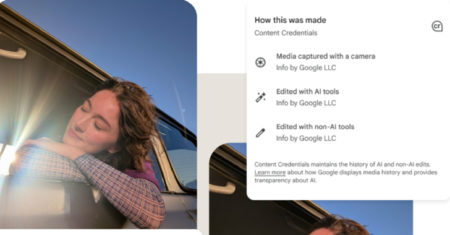
Google on Tuesday announced that its new Google Pixel 10 phones support the Coalition for Content Provenance and Authenticity (C2PA)…
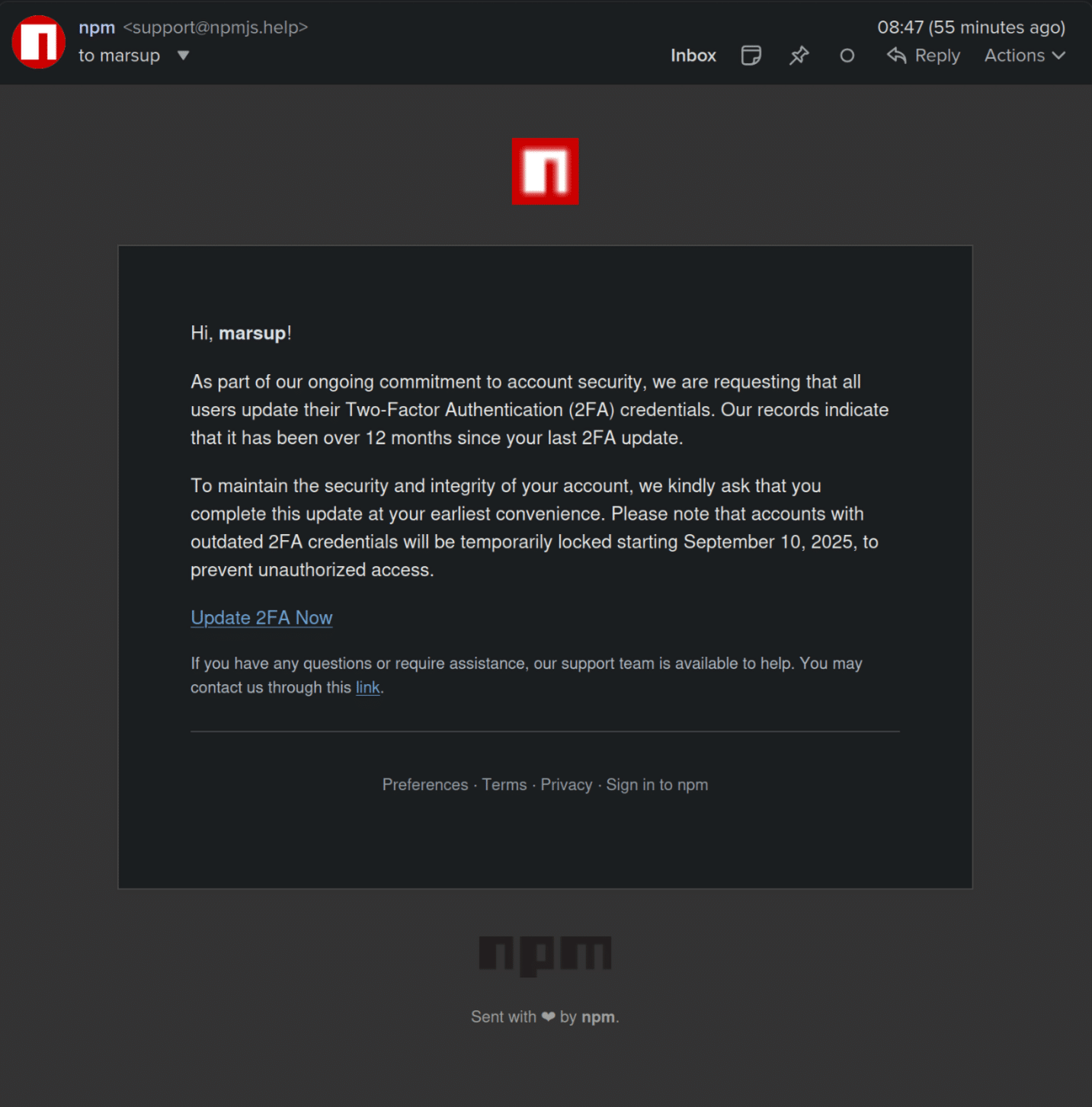
A massive NPM supply chain attack that hit about 10% of all cloud environments yielded little for the hackers who…
10 Reasons To Build a Full-stack Python Development Company Page Updated On GET A FREE QUOTE Low-Code vs No-Code Platforms…
ServiceNow today unveiled its Zurich platform release, designed to deliver breakthrough innovations with faster multi‑agentic AI development, enterprise‑wide AI platform…
The last time I reviewed the Pironman 5, I thought that it was the most amazing Raspberry Pi case that…