Abstract In recent years, language models and AI have reshaped how we interact with data. Yet, a significant portion of…
Meet Erin Zapata, a Practice Director based in Chicago, Illinois, whose empowering leadership and commitment to professional development have made…
Cloudflare now blocks AI crawlers by default, introduces pay per crawl model Last year, Cloudflare introduced a setting that allowed…
Infragistics, a global provider of tools and solutions to accelerate application design and development, today announced the launch of Infragistics Ultimate 25.1, the…
This month could barely have started any worse for some financial institutions in Brazil. Approximately US $140 million was stolen…
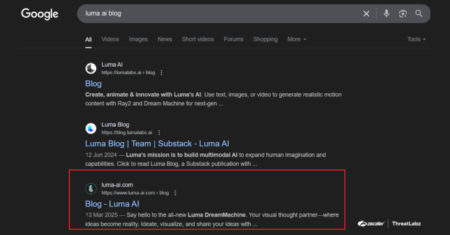
Cybersecurity researchers have disclosed a malicious campaign that leverages search engine optimization (SEO) poisoning techniques to deliver a known malware…
Food icons are used everywhere. You’ll see them on restaurant menus, mobile apps, food blogs, delivery sites, and product packaging.…
Post Content Source: Read MoreÂ
This blog explores how NLP-powered virtual assistants transform insurance customer support and improve underwriting. It explains core technologies like machine learning, speech recognition, and context awareness, driving these assistants. The blog also highlights crucial security and compliance guardrails needed for ethical deployment.
The post Why NLP Virtual Assistants Are No Longer Optional for Insurers first appeared on TestingXperts.
DOS Browser is a browser with built-in acceleration for DOS/Win9x games. The post DOS Browser – lightweight browser designed for…
NetworkManager attempts to keep an active network connection available at all times. The post NetworkManager – networking that just works…
CVE ID : CVE-2024-43334
Published : July 7, 2025, 10:15 a.m. | 2 hours, 54 minutes ago
Description : Improper Neutralization of Input During Web Page Generation (‘Cross-site Scripting’) vulnerability in Gavias Halpes allows Reflected XSS.This issue affects Halpes: from n/a before 1.2.5.
Severity: 7.1 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-3044
Published : July 7, 2025, 10:15 a.m. | 2 hours, 54 minutes ago
Description : A vulnerability in the ArxivReader class of the run-llama/llama_index repository, versions up to v0.12.22.post1, allows for MD5 hash collisions when generating filenames for downloaded papers. This can lead to data loss as papers with identical titles but different contents may overwrite each other, preventing some papers from being processed for AI model training. The issue is resolved in version 0.12.28.
Severity: 5.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-3046
Published : July 7, 2025, 10:15 a.m. | 2 hours, 54 minutes ago
Description : A vulnerability in the `ObsidianReader` class of the run-llama/llama_index repository, versions 0.12.23 to 0.12.28, allows for arbitrary file read through symbolic links. The `ObsidianReader` fails to resolve symlinks to their real paths and does not validate whether the resolved paths lie within the intended directory. This flaw enables attackers to place symlinks pointing to files outside the vault directory, which are then processed as valid Markdown files, potentially exposing sensitive information.
Severity: 7.5 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-3263
Published : July 7, 2025, 10:15 a.m. | 2 hours, 54 minutes ago
Description : A Regular Expression Denial of Service (ReDoS) vulnerability was discovered in the Hugging Face Transformers library, specifically in the `get_configuration_file()` function within the `transformers.configuration_utils` module. The affected version is 4.49.0, and the issue is resolved in version 4.51.0. The vulnerability arises from the use of a regular expression pattern `config.(.*).json` that can be exploited to cause excessive CPU consumption through crafted input strings, leading to catastrophic backtracking. This can result in model serving disruption, resource exhaustion, and increased latency in applications using the library.
Severity: 5.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-3467
Published : July 7, 2025, 10:15 a.m. | 3 hours, 29 minutes ago
Description : An XSS vulnerability exists in langgenius/dify versions prior to 1.1.3, specifically affecting Firefox browsers. This vulnerability allows an attacker to obtain the administrator’s token by sending a payload in the published chat. When the administrator views the conversation content through the monitoring/log function using Firefox, the XSS vulnerability is triggered, potentially exposing sensitive token information to the attacker.
Severity: 8.0 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-3466
Published : July 7, 2025, 10:15 a.m. | 2 hours, 54 minutes ago
Description : langgenius/dify versions 1.1.0 to 1.1.2 are vulnerable to unsanitized input in the code node, allowing execution of arbitrary code with full root permissions. The vulnerability arises from the ability to override global functions in JavaScript, such as parseInt, before sandbox security restrictions are imposed. This can lead to unauthorized access to secret keys, internal network servers, and lateral movement within dify.ai. The issue is resolved in version 1.1.3.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-3225
Published : July 7, 2025, 10:15 a.m. | 2 hours, 54 minutes ago
Description : An XML Entity Expansion vulnerability, also known as a ‘billion laughs’ attack, exists in the sitemap parser of the run-llama/llama_index repository, specifically affecting version v0.12.21. This vulnerability allows an attacker to supply a malicious Sitemap XML, leading to a Denial of Service (DoS) by exhausting system memory and potentially causing a system crash. The issue is resolved in version v0.12.29.
Severity: 7.5 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-3626
Published : July 7, 2025, 10:15 a.m. | 2 hours, 54 minutes ago
Description : A remote attacker with administrator account can gain full control of the device due to improper neutralization of special elements used in an OS Command (‘OS Command Injection’) while uploading a config file via webUI.
Severity: 9.1 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-3264
Published : July 7, 2025, 10:15 a.m. | 2 hours, 54 minutes ago
Description : A Regular Expression Denial of Service (ReDoS) vulnerability was discovered in the Hugging Face Transformers library, specifically in the `get_imports()` function within `dynamic_module_utils.py`. This vulnerability affects versions 4.49.0 and is fixed in version 4.51.0. The issue arises from a regular expression pattern `s*trys*:.*?except.*?:` used to filter out try/except blocks from Python code, which can be exploited to cause excessive CPU consumption through crafted input strings due to catastrophic backtracking. This vulnerability can lead to remote code loading disruption, resource exhaustion in model serving, supply chain attack vectors, and development pipeline disruption.
Severity: 5.3 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…