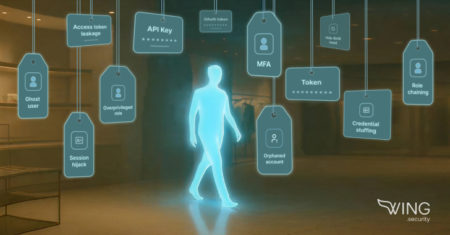
From overprivileged admin roles to long-forgotten vendor tokens, these attackers are slipping through the cracks of trust and access. Here’s…
This is a review of the BrosTrend USB WiFi 6 Adapter. It supports Ubuntu, Linux Mint, Debian, Ubuntu Mate, and…
A behind-the-scenes exploration of how creative ambition and modern tech defined a standout digital presence for one of Paris’s most…
Agama è il nuovo installatore per sistemi operativi basati su GNU/Linux sviluppato dal progetto openSUSE. OpenSUSE è una distribuzione GNU/Linux…
Parrot OS è una distribuzione GNU/Linux basata su Debian, progettata specificamente per la sicurezza informatica, il penetration testing e l’ethical…
Arago, a deeptech startup pioneering a new class of energy-efficient AI chips powered by light, has raised $26 million in…
CVE ID : CVE-2025-20694
Published : July 8, 2025, 3:15 a.m. | 3 hours, 36 minutes ago
Description : In Bluetooth FW, there is a possible system crash due to an uncaught exception. This could lead to remote denial of service with no additional execution privileges needed. User interaction is not needed for exploitation. Patch ID: ALPS09752821; Issue ID: MSV-3342.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-20693
Published : July 8, 2025, 3:15 a.m. | 3 hours, 36 minutes ago
Description : In wlan STA driver, there is a possible out of bounds read due to an incorrect bounds check. This could lead to remote (proximal/adjacent) information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation. Patch ID: ALPS09812521; Issue ID: MSV-3421.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-20695
Published : July 8, 2025, 3:15 a.m. | 3 hours, 36 minutes ago
Description : In Bluetooth FW, there is a possible system crash due to an uncaught exception. This could lead to remote denial of service with no additional execution privileges needed. User interaction is not needed for exploitation. Patch ID: ALPS09741871; Issue ID: MSV-3317.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-53610
Published : July 8, 2025, 3:15 a.m. | 3 hours, 36 minutes ago
Description : Rejected reason: Not used
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-53611
Published : July 8, 2025, 3:15 a.m. | 3 hours, 36 minutes ago
Description : Rejected reason: Not used
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-53613
Published : July 8, 2025, 3:15 a.m. | 3 hours, 36 minutes ago
Description : Rejected reason: Not used
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-53612
Published : July 8, 2025, 3:15 a.m. | 3 hours, 36 minutes ago
Description : Rejected reason: Not used
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-53615
Published : July 8, 2025, 3:15 a.m. | 3 hours, 36 minutes ago
Description : Rejected reason: Not used
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6244
Published : July 8, 2025, 3:15 a.m. | 3 hours, 36 minutes ago
Description : The Essential Addons for Elementor – Popular Elementor Templates and Widgets plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the via `Calendar` And `Business Reviews` Widgets attributes in all versions up to, and including, 6.1.19 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page.
Severity: 6.4 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-53616
Published : July 8, 2025, 3:15 a.m. | 3 hours, 36 minutes ago
Description : Rejected reason: Not used
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-53617
Published : July 8, 2025, 3:15 a.m. | 3 hours, 36 minutes ago
Description : Rejected reason: Not used
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-5570
Published : July 8, 2025, 3:15 a.m. | 3 hours, 36 minutes ago
Description : The AI Engine plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the mwai_chatbot shortcode ‘id’ parameter in all versions up to, and including, 2.8.4 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Subscriber-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page.
Severity: 5.4 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-53614
Published : July 8, 2025, 3:15 a.m. | 3 hours, 36 minutes ago
Description : Rejected reason: Not used
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7157
Published : July 8, 2025, 3:15 a.m. | 3 hours, 36 minutes ago
Description : A vulnerability was found in code-projects Online Note Sharing 1.0. It has been classified as critical. Affected is an unknown function of the file /login.php. The manipulation of the argument username/password leads to sql injection. It is possible to launch the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…