Casely’s Labor Day sale is here with cases starting at 2 for $30, thanks to a sweet BOGO offer. Plus,…
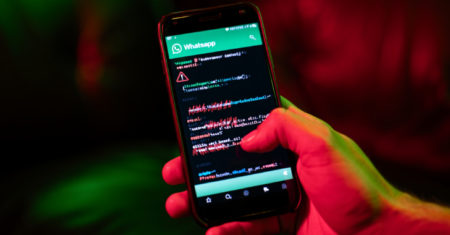
WhatsApp has addressed a security vulnerability in its messaging apps for Apple iOS and macOS that it said may have…
Cybersecurity researchers have called attention to a cyber attack in which unknown threat actors deployed an open-source endpoint monitoring and…
Windows 11 KB5064081 is finally rolling out for Windows 11 24H2, and it adds a new homepage for Recall AI,…
My family cinema not working on your TV box or Firestick? Follow these concise fixes to restore playback, reconnect your…
Comments Source: Read MoreÂ
10 Reasons To Build a Full-stack Python Development Company Page Updated On GET A FREE QUOTE 10 Top Generative AI…
CVE ID : CVE-2025-54942
Published : Aug. 30, 2025, 4:15 a.m. | 21 hours, 44 minutes ago
Description : A missing authentication for critical function vulnerability in SUNNET Corporate Training Management System before 10.11 allows remote attackers to access deployment functionality without prior authentication.
Severity: 9.3 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-54943
Published : Aug. 30, 2025, 4:15 a.m. | 21 hours, 44 minutes ago
Description : A missing authorization vulnerability in SUNNET Corporate Training Management System before 10.11 allows remote attackers to perform unauthorized application deployment due to the absence of proper access control checks.
Severity: 9.3 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-54945
Published : Aug. 30, 2025, 4:15 a.m. | 21 hours, 44 minutes ago
Description : An external control of file name or path vulnerability in SUNNET Corporate Training Management System before 10.11 allows remote attackers to execute arbitrary system commands via a malicious file by controlling the destination file path.
Severity: 10.0 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-54946
Published : Aug. 30, 2025, 4:15 a.m. | 21 hours, 44 minutes ago
Description : A SQL injection vulnerability in SUNNET Corporate Training Management System before 10.11 allows remote attackers to execute arbitrary SQL commands.
Severity: 9.3 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-9689
Published : Aug. 30, 2025, 1:15 p.m. | 12 hours, 44 minutes ago
Description : A vulnerability was detected in SourceCodester Advanced School Management System 1.0. The impacted element is an unknown function of the file /index.php/stock/item_select. The manipulation of the argument q results in sql injection. It is possible to launch the attack remotely. The exploit is now public and may be used.
Severity: 6.5 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-9688
Published : Aug. 30, 2025, 1:15 p.m. | 12 hours, 44 minutes ago
Description : A security vulnerability has been detected in Mupen64Plus up to 2.6.0. The affected element is the function write_is_viewer of the file src/device/cart/is_viewer.c. The manipulation leads to integer overflow. It is possible to initiate the attack remotely. The attack is considered to have high complexity. The exploitability is described as difficult. The exploit has been disclosed publicly and may be used. The vendor was contacted early about this disclosure but did not respond in any way.
Severity: 5.1 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2005-10004
Published : Aug. 30, 2025, 2:15 p.m. | 11 hours, 44 minutes ago
Description : Cacti versions prior to 0.8.6-d contain a remote command execution vulnerability in the graph_view.php script. An authenticated user can inject arbitrary shell commands via the graph_start GET parameter, which is improperly handled during graph rendering. This flaw allows attackers to execute commands on the underlying operating system with the privileges of the web server process, potentially compromising system integrity.
Severity: 8.7 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2009-20008
Published : Aug. 30, 2025, 2:15 p.m. | 11 hours, 44 minutes ago
Description : Green Dam Youth Escort version 3.17 is vulnerable to a stack-based buffer overflow when processing overly long URLs. The flaw resides in the URL filtering component, which fails to properly validate input length before copying user-supplied data into a fixed-size buffer. A remote attacker can exploit this vulnerability by enticing a user to visit a specially crafted webpage containing a long URL, resulting in arbitrary code execution.
Severity: 8.6 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2008-20001
Published : Aug. 30, 2025, 2:15 p.m. | 11 hours, 44 minutes ago
Description : activePDF WebGrabber version 3.8.2.0 contains a stack-based buffer overflow vulnerability in the GetStatus() method of the APWebGrb.ocx ActiveX control. By passing an overly long string to this method, a remote attacker can execute arbitrary code in the context of the vulnerable process. Although the control is not marked safe for scripting, exploitation is possible via crafted HTML content in Internet Explorer under permissive security settings.
Severity: 7.5 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2009-20009
Published : Aug. 30, 2025, 2:15 p.m. | 11 hours, 44 minutes ago
Description : Belkin Bulldog Plus version 4.0.2 build 1219 contains a stack-based buffer overflow vulnerability in its web service authentication handler. When a specially crafted HTTP request is sent with an oversized Authorization header, the application fails to properly validate the input length before copying it into a fixed-size buffer, resulting in memory corruption and potential remote code execution. Exploitation requires network access and does not require prior authentication.
Severity: 9.3 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2009-20010
Published : Aug. 30, 2025, 2:15 p.m. | 11 hours, 44 minutes ago
Description : Dogfood CRM version 2.0.10 contains a remote command execution vulnerability in the spell.php script used by its mail subsystem. The vulnerability arises from unsanitized user input passed via a POST request to the data parameter, which is processed by the underlying shell without adequate escaping. This allows attackers to inject arbitrary shell commands and execute them on the server. The flaw is exploitable without authentication and was discovered by researcher LSO.
Severity: 9.3 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2009-20011
Published : Aug. 30, 2025, 2:15 p.m. | 11 hours, 44 minutes ago
Description : ContentKeeper Web Appliance (now maintained by Impero Software) versions prior to 125.10 are vulnerable to remote command execution due to insecure handling of file uploads via the mimencode CGI utility. The vulnerability allows unauthenticated attackers to upload and execute arbitrary scripts as the Apache user. Additionally, the exploit can optionally escalate privileges by abusing insecure PATH usage in the benetool binary, resulting in root-level access if successful.
Severity: 10.0 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2010-10016
Published : Aug. 30, 2025, 2:15 p.m. | 11 hours, 44 minutes ago
Description : BS.Player version 2.57 (build 1051) contains a vulnerability in its playlist import functionality. When processing .m3u files, the application fails to properly validate the length of playlist entries, resulting in a buffer overflow condition. This flaw occurs during parsing of long URLs embedded in the playlist, allowing overwrite of Structured Exception Handler (SEH) records. The vulnerability is triggered upon opening a crafted playlist file and affects the Unicode parsing logic in the Windows client.
Severity: 10.0 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…