Fraud detection remains a significant challenge in the financial industry, requiring advanced machine learning (ML) techniques to detect fraudulent patterns…
Today, we announce the public preview of long-running execution (asynchronous) flow support within Amazon Bedrock Flows. With Amazon Bedrock Flows,…
Managing access control in enterprise machine learning (ML) environments presents significant challenges, particularly when multiple teams share Amazon SageMaker AI…
What if you could replace hours of data analysis with a minute-long conversation? Large language models can transform how we…
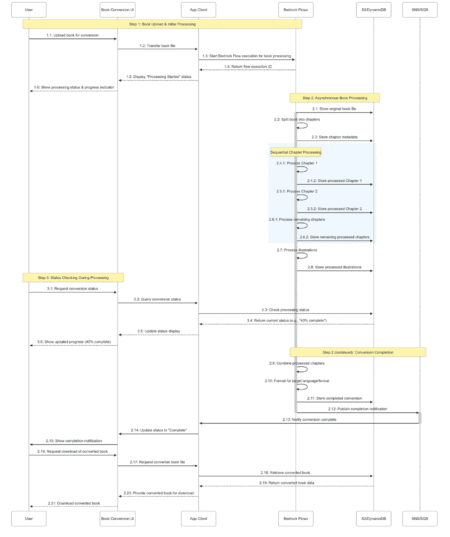
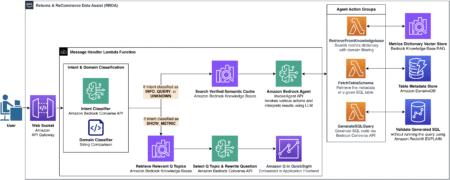
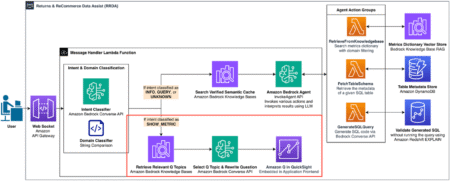
In Part 1 of this series, we explored how Amazon’s Worldwide Returns & ReCommerce (WWRR) organization built the Returns &…
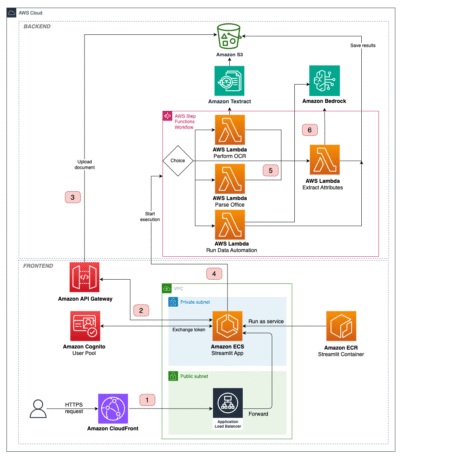
Extracting information from unstructured documents at scale is a recurring business task. Common use cases include creating product feature tables…
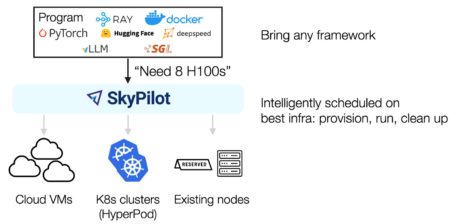
This post is co-written with Zhanghao Wu, co-creator of SkyPilot. The rapid advancement of generative AI and foundation models (FMs)…
This post provides the theoretical foundation and practical insights needed to navigate the complexities of LLM development on Amazon SageMaker…
We design and implement AXLearn, a production deep learning system that facilitates scalable and high-performance training of large deep learning…
Multimodal Vision-Language Models (VLMs) enable powerful applications from their fused understanding of images and language, but many perform poorly on…
CVE ID : CVE-2025-50121
Published : July 11, 2025, 10:15 a.m. | 9 hours, 59 minutes ago
Description : CWE-78: Improper Neutralization of Special Elements used in an OS Command (‘OS Command Injection’)
vulnerability exists that could cause unauthenticated remote code execution when a malicious folder is created
over the web interface HTTP when enabled. HTTP is disabled by default.
Severity: 10.0 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-50122
Published : July 11, 2025, 10:15 a.m. | 9 hours, 59 minutes ago
Description : CWE-331: Insufficient Entropy vulnerability exists that could cause root password discovery when the
password generation algorithm is reverse engineered with access to installation or upgrade artifacts.
Severity: 8.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-52950
Published : July 11, 2025, 3:15 p.m. | 4 hours, 59 minutes ago
Description : A Missing Authorization vulnerability in Juniper Networks Security Director allows an unauthenticated network-based attacker to read or tamper with multiple sensitive resources via the web interface.
Numerous endpoints on the Juniper Security Director appliance do not validate authorization and will deliver information to the caller that is outside their authorization level. An attacker can access data that is outside the user’s authorization level. The information obtained can be used to gain access to additional information or perpetrate other attacks, impacting downstream managed devices.
This issue affects Security Director version 24.4.1.
Severity: 9.6 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7026
Published : July 11, 2025, 4:15 p.m. | 4 hours, 50 minutes ago
Description : A vulnerability in the Software SMI handler (SwSmiInputValue 0xB2) allows a local attacker to control the RBX register, which is used as an unchecked pointer in the CommandRcx0 function. If the contents at RBX match certain expected values (e.g., ‘$DB$’ or ‘2DB$’), the function performs arbitrary writes to System Management RAM (SMRAM), leading to potential privilege escalation to System Management Mode (SMM) and persistent firmware compromise.
Severity: 8.2 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-52989
Published : July 11, 2025, 4:15 p.m. | 4 hours, 50 minutes ago
Description : An Improper Neutralization of Delimiters vulnerability in the UI of Juniper Networks Junos OS and Junos OS Evolved allows a local, authenticated attacker with high privileges to modify the system configuration.
A user with limited configuration and commit permissions, using a specifically crafted annotate configuration command, can change any part of the device configuration.
This issue affects:
Junos OS:
* all versions before 22.2R3-S7,
* 22.4 versions before 22.4R3-S7,
* 23.2 versions before 23.2R2-S4,
* 23.4 versions before 23.4R2-S4,
* 24.2 versions before 24.2R2-S1,
* 24.4 versions before 24.4R1-S2, 24.4R2;
Junos OS Evolved:
* all versions before 22.4R3-S7-EVO,
* 23.2-EVO versions before 23.2R2-S4-EVO,
* 23.4-EVO versions before 23.4R2-S5-EVO,
* 24.2-EVO versions before 24.2R2-S1-EVO
* 24.4-EVO versions before 24.4R2-EVO.
Severity: 5.1 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6549
Published : July 11, 2025, 4:15 p.m. | 4 hours, 50 minutes ago
Description : An Incorrect Authorization vulnerability in the web server of Juniper Networks Junos OS on SRX Series allows an unauthenticated, network-based attacker to reach the
Juniper Web Device Manager
(J-Web).
When Juniper Secure connect (JSC) is enabled on specific interfaces, or multiple interfaces are configured for J-Web, the J-Web UI is reachable over more than the intended interfaces.
This issue affects Junos OS:
* all versions before 21.4R3-S9,
* 22.2 versions before 22.2R3-S5,
* 22.4 versions before 22.4R3-S5,
* 23.2 versions before 23.2R2-S3,
* 23.4 versions before 23.4R2-S5,
* 24.2 versions before 24.2R2.
Severity: 6.5 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7027
Published : July 11, 2025, 4:15 p.m. | 4 hours, 50 minutes ago
Description : A vulnerability in the Software SMI handler (SwSmiInputValue 0xB2) allows a local attacker to control both the read and write addresses used by the CommandRcx1 function. The write target is derived from an unvalidated UEFI NVRAM variable (SetupXtuBufferAddress), while the write content is read from an attacker-controlled pointer based on the RBX register. This dual-pointer dereference enables arbitrary memory writes within System Management RAM (SMRAM), leading to potential SMM privilege escalation and firmware compromise.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7028
Published : July 11, 2025, 4:15 p.m. | 4 hours, 50 minutes ago
Description : A vulnerability in the Software SMI handler (SwSmiInputValue 0x20) allows a local attacker to supply a crafted pointer (FuncBlock) through RBX and RCX register values. This pointer is passed unchecked into multiple flash management functions (ReadFlash, WriteFlash, EraseFlash, and GetFlashInfo) that dereference both the structure and its nested members, such as BufAddr. This enables arbitrary read/write access to System Management RAM (SMRAM), allowing an attacker to corrupt firmware memory, exfiltrate SMRAM content via flash, or install persistent implants.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7029
Published : July 11, 2025, 4:15 p.m. | 4 hours, 50 minutes ago
Description : A vulnerability in the Software SMI handler (SwSmiInputValue 0xB2) allows a local attacker to control the RBX register, which is used to derive pointers (OcHeader, OcData) passed into power and thermal configuration logic. These buffers are not validated before performing multiple structured memory writes based on OcSetup NVRAM values, enabling arbitrary SMRAM corruption and potential SMM privilege escalation.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2024-47065
Published : July 11, 2025, 5:15 p.m. | 3 hours, 50 minutes ago
Description : Meshtastic is an open source mesh networking solution. Prior to 2.5.1, traceroute responses from the remote node are not rate limited. Given that there are SNR measurements attributed to each received transmission, this is a guaranteed way to get a remote station to reliably and continuously respond. You could easily get 100 samples in a short amount of time (estimated 2 minutes), whereas passively doing the same could take hours or days. There are secondary effects that non-ratelimited traceroute does also allow a 2:1 reflected DoS of the network as well, but these concerns are less than the problem with positional confidentiality (other DoS routes exist). This vulnerability is fixed in 2.5.1.
Severity: 0.0 | NA
Visit the link for more details, such as CVSS details, affected products, timeline, and more…