The Distribution Strategy Group recently hosted a webinar exploring the future of B2B distribution, bringing together a panel of industry…
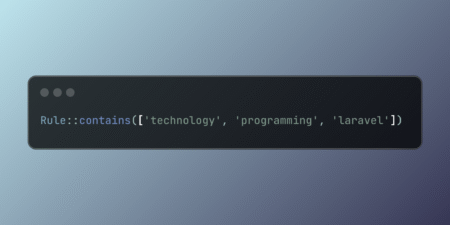
Laravel’s Rule::contains() method provides fluent array validation syntax, replacing string concatenation with clean, readable rules. Maintain consistency with Laravel’s validation…
With PHP 8.5, a new fatal_error_backtraces setting can control whether a backtrace is shown for fatal errors. Learn how this…
Gemini API gets Batch Mode Batch Mode allows large jobs to be submitted through the Gemini API. Results are returned…
Earlier this week, JFrog disclosed CVE-2025-6514, a critical vulnerability in the mcp-remote project that could allow an attacker to “trigger…
Paddy Power and BetFair have warned customers that “an unauthorised third party” gained access to “limited betting account information” relating…
Cybersecurity researchers have discovered a set of four security flaws in OpenSynergy’s BlueSDK Bluetooth stack that, if successfully exploited, could…
A Russian professional basketball player has been arrested for allegedly acting as a negotiator for a ransomware gang… and despite…
Fortinet has released fixes for a critical security flaw impacting FortiWeb that could enable an unauthenticated attacker to run arbitrary…
From test devices to software licenses, IT teams are juggling way more than meets the eye. IT asset management isn’t…
Imagine. Prompt. Create. Source: Read MoreÂ
Web design ideas in 2025 demonstrate a bright and unusual approach. They combine aesthetics, proven functionality, perfect usability, and innovations.…
Mosaic designs have an incredible ability to evoke a sense of tradition, craftsmanship, and timeless beauty in any design. Source:…
We scaled Santa, an open-source binary authorization tool, across all Figmates’ laptops to boost endpoint security while keeping workflows seamless.…
It’s time again to share some cool resources and tools for our fellow developers. There are so many cool tools…
Instagram hosts over 2 billion monthly active users, making it one of the most competitive platforms for brands and content creators…
Growing a startup means becoming bigger while also making smart decisions. Having such a digital plan for startups means technology…
Apple researchers are advancing AI and ML through fundamental research, and to support the broader research community and help accelerate…
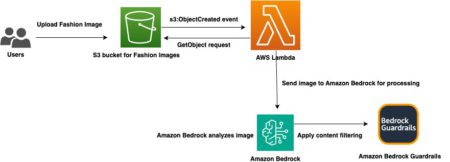
The global fashion industry is estimated to be valued at $1.84 trillion in 2025, accounting for approximately 1.63% of the…
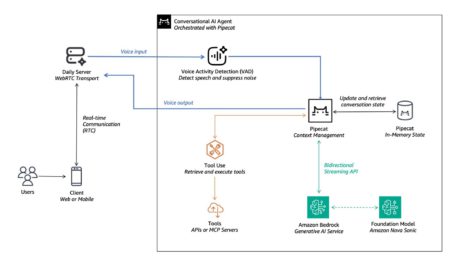
Voice AI is changing the way we use technology, allowing for more natural and intuitive conversations. Meanwhile, advanced AI agents…