Get it while it lasts; this deal will be gone once Amazon Prime Day is over. Grab it before you…
Five free Bedrock add-ons that totally shake up survival, crafting, and provide some chaos. Best of all, it doesn’t cost…
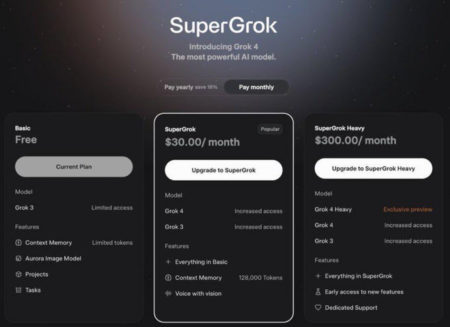
Top News Elon Musk’s xAI launches Grok 4 alongside a $300 monthly subscription xAI has launched its latest AI model,…
NVIDIA is urging customers to enable System-level Error Correction Codes (ECC) as a defense against a variant of a RowHammer…
One of the many features that make After Effects so versatile is its ability to create stunning slideshows and galleries.…
Looking for the best smartphones under ₹30,000 in India? Whether you’re a gamer, a photography enthusiast, or someone who just wants a powerful phone with great battery and display, we’ve handpicked the top 8 phones available on Amazon that offer premium features at mid-range prices. Ranked based on customer reviews, features, and overall value, these phones deliver flagship-like performance without breaking the bank. Scroll down for the full list with images, prices, Amazon affiliate links, and a comparison chart to help you pick the perfect one!
1. Nothing Phone (3a Pro)
Affiliate link: https://amzn.to/46yaDTA
Price: ₹30,337 (approx)
Summary:
Launched March 2025 with Snapdragon 7s Gen 3, a 6.77″ LTPO AMOLED display, triple-camera (50 MP OIS + 50 MP telephoto + 8 MP ultrawide), 5,000 mAh battery with 50 W fast charge, and NothingOS with 3 years of Android + 6 years of security updates.
Highlights:
Unique transparent design + Glyph interface
Periscope zoom on Pro model
Smooth 120 Hz high-bright LTPO screen
2. Infinix GT 30 Pro
Affiliate link: https://amzn.to/3IgnP5yPrice: ₹24,999
Summary:
A gamer’s delight with Dimensity 8350 Ultimate, 144 Hz AMOLED display, RGB lighting, shoulder triggers, 5,500 mAh battery, 45 W charging, and a 108 MP main camera.
Highlights:
Excellent for gaming at 120 fps
Bright display with ultrafast refresh rate
Strong everyday performance
3. OnePlus Nord 4
Affiliate link: https://amzn.to/4eI6bUr
Price: ₹26,688 (after discounts)
Summary:
Now under ₹27 k with deals; but still solid with Snapdragon 7+ Gen 3, 6.74″ 120 Hz AMOLED, 5,500 mAh battery with 100 W fast charge, dual-camera (50 MP+8 MP), and OxygenOS experience.
Highlights:
Clean design with Snapdragon power
Ultra-fast wired charging
Premier display brightness
4. Realme GT 6
Affiliate link: https://amzn.to/3Gf5Dc1Price: ₹27,999
Summary:
Equipped with Snapdragon 8s Gen 3, 6.78″ AMOLED, 120 Hz, dual 50 MP + 50 MP rear cams, 5,500 mAh battery. Excellent display and camera stabilization
Highlights:
Powerful chipset under ₹30k
Bright, high-refresh display
Strong camera and fast charging
5. iQOO Neo 10R
Affiliate link: https://amzn.to/45UsRhSPrice: ₹26,999
Summary:
Launched March 2025 with Snapdragon 8s Gen 3, 6.78″ 144 Hz AMOLED, 6,400 mAh battery; 50 MP + 8 MP + 32 MP selfie cam. High performance and smooth visuals.
Highlights:
Ultra‑high 144 Hz refresh
Snapdragon flagship-like feel
Large battery and speedy performance
6. Realme 14 Pro + 5G
Affiliate link: https://amzn.to/4lhgst1
Price: ₹26,480
Summary:
Features Snapdragon 7s Gen 3, 6.83″ AMOLED 120 Hz, 50 MP Sony IMX896 OIS, 6,000 mAh battery. Flagship feel with premium camera and display.
Highlights:
Excellent imaging & stabilization
Stunning bright display
Clean software UI
7. Motorola Edge 60 Pro (Fusion?)
Affiliate link: https://amzn.to/40Ayj60Price: ₹27,999
Summary:
Featuring Dimensity 8350 Extreme, 6.7″ curved pOLED 120 Hz, clean Android 15 experience, reliable camera and battery life.
Highlights:
Curved OLED aesthetics
Smooth near-stock Android
Dependable camera and longevity
8. Oppo Reno 11 Pro 5G
Affiliate link: https://amzn.to/4kt1crV
Price: ₹29,999
Summary:
MediaTek Dimensity 8200, 6.74″ AMOLED, 50 MP + 32 MP + 8 MP cam, 32 MP selfie, 4,600 mAh battery.
Highlights:
Sleek lightweight design
Good for photography users
Premium feel in sub‑30k segment
📊 Final Rankings by Reviews & Value:
Nothing Phone (3a Pro) – Standout design, periscope zoom, top-tier support
Infinix GT 30 Pro – Gamer’s delight with 144 Hz + RGB + strong battery
OnePlus Nord 4 – Clean OxygenOS, blazing 100 W charge
Realme GT 6 – Flagship-like experience under ₹30k
iQOO Neo 10R – 144 Hz display, Snapdragon 8s performance
Realme 14 Pro + – Great camera & display, solid mid‑range
Motorola Edge 60 Pro – Curved OLED & near-stock UI
Oppo Reno 11 Pro 5G – Design-first with solid optics
🛍️ Tips Before You Buy
Gamer? Choose Infinix GT 30 Pro or iQOO Neo 10R.
Camera priorities? Realme 14 Pro+, Nothing 3a Pro, or Oppo Reno 11 Pro deliver.
Smooth, clean software? Go with OnePlus, Motorola, or Nothing.
Fastest charging? Nord 4 leads with 100 W; others offer 45–50 W.
Conclusion
All eight are excellent under ₹30 k. If style & long-term support matter most, go for Nothing Phone (3a Pro). If you play games heavily, the Infinix GT 30 Pro is tailor-made. For a balanced blend of performance and clean software, Nord 4, Realme, iQOO, or Moto Edge are/well‑rounded picks.
CVE ID : CVE-2025-6057
Published : July 12, 2025, 5:15 a.m. | 12 hours, 44 minutes ago
Description : The WPBookit plugin for WordPress is vulnerable to arbitrary file uploads due to missing file type validation in the handle_image_upload() function in all versions up to, and including, 1.0.4. This makes it possible for authenticated attackers, with Subscriber-level access and above, to upload arbitrary files on the affected site’s server which may make remote code execution possible.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6058
Published : July 12, 2025, 5:15 a.m. | 12 hours, 44 minutes ago
Description : The WPBookit plugin for WordPress is vulnerable to arbitrary file uploads due to missing file type validation in the image_upload_handle() function hooked via the ‘add_booking_type’ route in all versions up to, and including, 1.0.4. This makes it possible for unauthenticated attackers to upload arbitrary files on the affected site’s server which may make remote code execution possible.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-1313
Published : July 12, 2025, 6:15 a.m. | 11 hours, 44 minutes ago
Description : The Nokri – Job Board WordPress Theme theme for WordPress is vulnerable to privilege escalation via account takeover in all versions up to, and including, 1.6.3. This is due to the plugin not properly validating a user’s identity prior to updating their details like email address. This makes it possible for authenticated attackers, with Subscriber-level access and above, to change arbitrary user’s email addresses, including administrators, and leverage that to reset the user’s password and gain access to their account.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7463
Published : July 12, 2025, 6:15 a.m. | 11 hours, 44 minutes ago
Description : A vulnerability was found in Tenda FH1201 1.2.0.14. It has been declared as critical. This vulnerability affects the function formWrlsafeset of the file /goform/AdvSetWrlsafeset of the component HTTP POST Request Handler. The manipulation of the argument mit_ssid leads to buffer overflow. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7465
Published : July 12, 2025, 7:15 a.m. | 10 hours, 44 minutes ago
Description : A vulnerability classified as critical was found in Tenda FH1201 1.2.0.14. Affected by this vulnerability is the function fromRouteStatic of the file /goform/fromRouteStatic of the component HTTP POST Request Handler. The manipulation of the argument page leads to buffer overflow. The attack can be launched remotely. The exploit has been disclosed to the public and may be used.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-6423
Published : July 12, 2025, 8:15 a.m. | 9 hours, 44 minutes ago
Description : The BeeTeam368 Extensions plugin for WordPress is vulnerable to arbitrary file uploads due to missing file type validation in the handle_submit_upload_file() function in all versions up to, and including, 2.3.5. This makes it possible for authenticated attackers with Subscriber-level access or higher to upload arbitrary files on the affected site’s server which may make remote code execution possible.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7466
Published : July 12, 2025, 8:15 a.m. | 10 hours, 26 minutes ago
Description : A vulnerability, which was classified as critical, has been found in 1000projects ABC Courier Management 1.0. Affected by this issue is some unknown functionality of the file /add_dealerrequest.php. The manipulation of the argument Name leads to sql injection. The attack may be launched remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7467
Published : July 12, 2025, 9:15 a.m. | 9 hours, 26 minutes ago
Description : A vulnerability, which was classified as critical, was found in code-projects Modern Bag 1.0. This affects an unknown part of the file /product-detail.php. The manipulation of the argument ID leads to sql injection. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7468
Published : July 12, 2025, 9:15 a.m. | 9 hours, 26 minutes ago
Description : A vulnerability has been found in Tenda FH1201 1.2.0.14 and classified as critical. This vulnerability affects the function fromSafeUrlFilter of the file /goform/fromSafeUrlFilter of the component HTTP POST Request Handler. The manipulation of the argument page leads to buffer overflow. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used.
Severity: 8.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7504
Published : July 12, 2025, 9:15 a.m. | 9 hours, 26 minutes ago
Description : The Friends plugin for WordPress is vulnerable to PHP Object Injection in version 3.5.1 via deserialization of untrusted input of the query_vars parameter This makes it possible for authenticated attackers, with subscriber-level access and above, to inject a PHP Object. No known POP chain is present in the vulnerable software, which means this vulnerability has no impact unless another plugin or theme containing a POP chain is installed on the site. If a POP chain is present via an additional plugin or theme installed on the target system, it may allow the attacker to perform actions like delete arbitrary files, retrieve sensitive data, or execute code depending on the POP chain present. This requires access to the sites SALT_NONCE and and SALT_KEY to exploit.
Severity: 7.5 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2020-36847
Published : July 12, 2025, 10:15 a.m. | 8 hours, 26 minutes ago
Description : The Simple-File-List Plugin for WordPress is vulnerable to Remote Code Execution in versions up to, and including, 4.2.2 via the rename function which can be used to rename uploaded PHP code with a png extension to use a php extension. This allows unauthenticated attackers to execute code on the server.
Severity: 9.8 | CRITICAL
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7518
Published : July 12, 2025, 10:15 a.m. | 8 hours, 26 minutes ago
Description : The RSFirewall! plugin for WordPress is vulnerable to Path Traversal in all versions up to, and including, 1.1.42 via the get_local_filename() function. This makes it possible for authenticated attackers, with Administrator-level access and above, to read the contents of arbitrary files on the server, which can contain sensitive information.
Severity: 4.9 | MEDIUM
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7469
Published : July 12, 2025, 11:15 a.m. | 7 hours, 26 minutes ago
Description : A vulnerability was found in Campcodes Sales and Inventory System 1.0 and classified as critical. This issue affects some unknown processing of the file /pages/product_add.php. The manipulation of the argument prod_name leads to sql injection. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…
CVE ID : CVE-2025-7470
Published : July 12, 2025, 11:15 a.m. | 7 hours, 26 minutes ago
Description : A vulnerability was found in Campcodes Sales and Inventory System 1.0. It has been classified as critical. Affected is an unknown function of the file /pages/product_add.php. The manipulation of the argument image leads to unrestricted upload. It is possible to launch the attack remotely. The exploit has been disclosed to the public and may be used.
Severity: 7.3 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…