The DistroWatch news feed is brought to you by TUXEDO COMPUTERS. The Linux From Scratch project (also called LFS) has announced the release of version 12.4 of the project’s guide. This guide walks the reader through the steps to create a minimal Linux distribution from source code. The release announcement reads: “The Linux From Scratch community announces the release….
OxiCloud prioritizes speed and simplicity while still being robust enough for daily use. The post OxiCloud – lightweight, Rust-powered alternative…
Walker is a fast, customizable application launcher built with GTK4 and Rust, designed for Linux desktop environments. The post Walker…
The machine has the AMD Ryzen AI 9 HX 370 processor with integrated Radeon 890M. This is no ordinary processor…
Linux Lite è una distribuzione GNU/Linux basata su Ubuntu LTS (Long Term Support), progettata per offrire un sistema operativo semplice,…
Learn how to use GSAP and its plugins to recreate a refined grid animation. Source: Read MoreÂ
Policorp Linux is a Brazilian Linux distribution. Its development is based on Debian Linux, offering a simpler and easier to…
Incus è un gestore di contenitori e macchine virtuali open source, nato come progetto guidato dalla comunità dopo che Canonical…
AerynOS è una distribuzione GNU/Linux indipendente, progettata per offrire un ambiente moderno, snello e orientato agli utenti avanzati e agli…
Bcachefs is an advanced filesystem for Linux, with an emphasis on reliability and robustness The post Bcachefs – advanced filesystem…
Today’s Labor Day in the US, a day where we celebrate workers. Well, some of us. This story from the…
ClangFormat is a code formatting tool that helps maintain common code style across team members and IDEs. The post ClangFormat…
Next month, Samsung will show off its three most cutting-edge devices at its third Unpacked event of 2025 – and…
Smart plugs are an easy, budget-friendly way to upgrade your home. Here are a few clever ways to use them…
Nuance Audio’s smart glasses offer a discreet, innovative alternative to traditional hearing aids, with built-in speakers and a powerful companion…
Ahead of the iPhone 17 launch event, you can snag a current-gen model for significantly less than retail with this…
If you use Apache Spark to write your data pipeline, you might need to export or copy data from a…
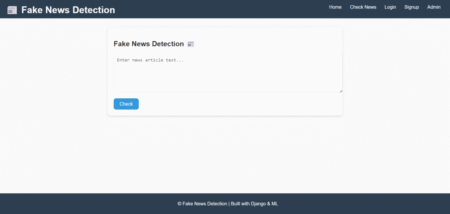
“Fake News Detection System Project using Python ML” is a web-based application aimed at combating the growing challenge of online…
Post Content Source: Read MoreÂ
Post Content Source: Read MoreÂ