The EcoFlow Trail Series prioritizes ease of use, making it a suitable portable battery for camping or travel. Source: Latest…
I’ve watched many people spend huge amounts of money keeping their computers running or up to speed. But they don’t…
The new Kindle Colorsoft Kids offers a more engaging and focused e-reading experience for children. Source: Latest newsÂ
Watch your pictures come to life in six-second clips, or let Google’s AI edit your photos into an entirely different…
The privacy-minded Brave browser doesn’t want Recall snooping on your online activities, though you can turn the option back on…
The new Qi2 25 W standard is especially good news for Android users. Here’s why. Source: Latest newsÂ
The public preview arrives amid a surge of investment from leading tech companies in AI-powered coding assistants. Source: Latest newsÂ
Motorola is holding a new promotion for its flagship foldable that slashes hundreds of dollars off the 2025 Razr Ultra.…
Apple’s newest operating system for Macs, Tahoe, is coming soon. If you’re not sure if your device is compatible with…
As Bee AI is acquired by Amazon, interest in AI-first hardware continues to buzz. Source: Latest newsÂ
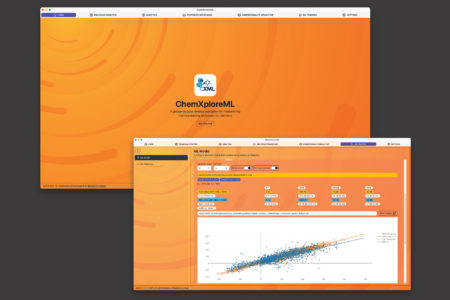
One of the shared, fundamental goals of most chemistry researchers is the need to predict a molecule’s properties, such as…
City life is often described as “fast-paced.” A new study suggests that’s more true that ever. The research, co-authored by…
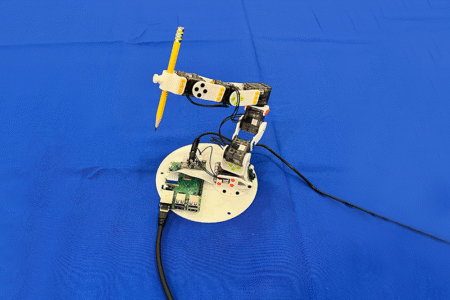
In an office at MIT’s Computer Science and Artificial Intelligence Laboratory (CSAIL), a soft robotic hand carefully curls its fingers…
First, a confession: When I was learning to code, my “workflow” was a mess. Sticky notes. Google Docs. Random Trello…
Discover why design systems are essential for consistent UX in 2025. Learn how top companies like Google, Apple, and IBM…
In the world of software development, speed, scalability, and user experience are paramount. Flutter, with its expressive UI toolkit and…
If you’re building something on your own, you don’t have time to mess around with bloated platforms or complicated setups.…
Practice communication, develop creativity, and build confidence. Our top 5 picks for AI companion apps. Continue reading 5 Best AI…
Explore top C++ compilers like GCC, MSVC, and Clang, plus IDEs such as Visual Studio and CLion. Learn how to…
As we all know, in the world of reels, Photos, and videos, Everyone is creating content and uploading to public-facing…