The Division 2 has seen a resurgence with its latest DLC, reaching heights of engagement not seen in more than…
11 bit studios’ Frostpunk 2 is finally headed to Xbox Series X|S and PlayStation 5 in September 2025, with the…
One of Xbox’s biggest Game Pass hits this year, Oblivion Remastered, just hit a massive milestone. However, “Mixed” PC reviews…
Sony is following Microsoft’s multiplatform strategy, looking to acquire a bigger third-party publishing footprint across PC and even rival consoles.…
On this week’s episode of the podcast, freeCodeCamp founder Quincy Larson interviews Nick Taylor. He’s a software engineer from Montreal…
Intel CEO Lip-Bu Tan announces 15% job cuts and cancels expansion plans as the company refocuses on core products, cost…
This is Part 3 of a three-part series (links at the bottom). In Part Two, we moved from concept to execution by…
Welcome back to our session on Agile and Accessibility, where we bring together two powerful forces in inclusive product development.…
Welcome back to our series exploring the fusion of Agile principles and Accessibility practices to create products that serve everyone.…
Intro In this post I’d like to share a workflow “attacher” implementation I built on a recent Sitecore XM Cloud…
by George Whittaker Introduction In recent times, two critical Linux security frameworks, AppArmor and SELinux, have seen noteworthy acceleration in…
Before rushing to prove that you’re not a robot, be wary of deceptive human verification pages as an increasingly popular…
ESET Research has been monitoring attacks involving the recently discovered ToolShell zero-day vulnerabilities Source: Read More
SpaceX’s Starlink internet service suffered a major international outage, disconnecting tens of thousands of users for over two hours. The…
A recent analysis of enterprise data suggests that generative AI tools developed in China are being used extensively by employees…
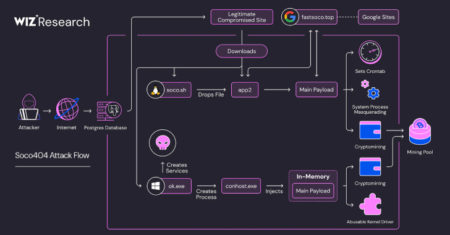
Threat hunters have disclosed two different malware campaigns that have targeted vulnerabilities and misconfigurations across cloud environments to deliver cryptocurrency…
Russian aerospace and defense industries have become the target of a cyber espionage campaign that delivers a backdoor called EAGLET…
The threat actor known as Patchwork has been attributed to a new spear-phishing campaign targeting Turkish defense contractors with the…
The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) sanctioned a North Korean front company and three…
Post Content Source: Read MoreÂ




![How to turn Open Source into a Job with Nick Taylor [Podcast #181]](https://devstacktips.com/wp-content/uploads/2025/07/68ffabee-3e00-485f-b8a4-8f80078ca0cd-DJcKdh-450x253.png)