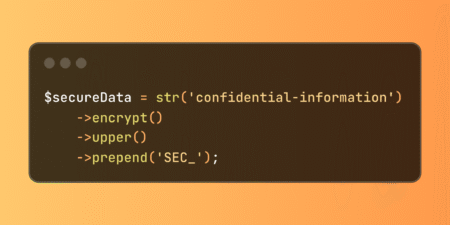
Simplify Laravel string encryption with new fluent methods that eliminate pipe workarounds. These integrated encrypt and decrypt functions maintain clean…
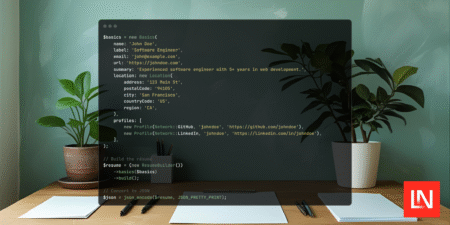
Resume PHP is a library that provides a type-safe way to build and work with resumes following the JSON Resume…
Microsoft just added a bunch of new features into the AI-powered Copilot Mode in its Edge browser. But some of…
The Dell Premium 16 is a sleek follow-up to the iconic XPS line with impressive hardware and stunning 4K touchscreen.…
No matter if you use Linux for a desktop or server, backups are a crucial component of ensuring you always…
Back Market offers verified refurbished tech devices for a lower price than buying new, but should you buy it? Source:…
The new Dell 14 Premium picks up where the XPS model left off, as a sleek and modern workstation for…
The Wyze Lamp Socket v2 can power your Wyze Cam and lets your outdoor lighting work seamlessly with your camera.…
If you find yourself constantly looking for ways to remember the last time you communicated with someone, Android will soon…
What if you didn’t have to touch your screen or type on a keyboard? Source: Latest newsÂ
Tired of balancing monitors and mice on your server rack? This $90 gadget might be the remote-access fix your cluttered…
When you trade in a qualifying phone under an Unlimited Ultimate plan, you can get the brand new Samsung Galaxy…
A series of images on X hint at a redesigned camera bar for the upcoming iPhone 17 series, in line…
Passkeys are stored within your device’s operating system or credential manager. So, what happens if your device falls into the…
Gamers are using Death Stranding to trick UK age verification laws, fooling Discord’s face scan system without a real face…
Several more Xbox games are launching this week, from July 28 through August 3, including the early access release of…
ByteDance, best known in the west for TikTok, has a new AI-infused code editor forked from Microsoft’s Visual Studio Code.…
AdGuard for Windows now includes a new feature called “Disable Windows Recall,” designed to prevent the controversial Windows Recall tool…
Xbox has announced some huge news for Hollow Knight: Silksong fans, at least if they’re going to be at Gamescom…
World of Warcraft Source: Read More /