10 Reasons To Build a Full-stack Python Development Company Page Updated On GET A FREE QUOTE Top 10 Use Cases…
Cloudsmith, providers of an artifact management platform, announced its ML Model Registry, which can act as a single source of…
Kong Inc., a leading developer of cloud API and AI technologies, today announced the acquisition of OpenMeter, a leading open-source…
If you’ve read any of my stuff or listened to one of my presentations before, you’ve likely heard my snarky…
The EIC Scaling Club’s 120 European deep tech scaleups have collectively raised over €1.2 billion in funding within the scope…
Discover seven practical GSAP tips that will help you create smoother, smarter, and more creative web animations with less code.…
David G saw a pull request with a surprisingly long thread of comments on it. What was weirder was that…
The Laracon AU 2025 schedule is now live, with the full list of talk titles published today! The post Laracon…
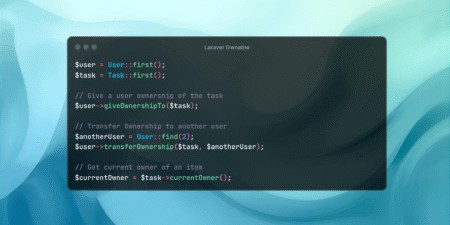
Handle ownership relationships between Eloquent models in a flexible way with Laravel Ownable. The post Handle ownership relationships between Eloquent…
Transform messy Laravel controllers with 15+ lines of calculations into clean, three-line coordinators using custom collection methods. This practical tutorial…
This seriously raised the hairs on the back of my neck. Source: Latest newsÂ
You have options, but the truth is, trusting browser extensions is getting harder. Source: Latest newsÂ
The new format also fixes one major complaint. Source: Latest newsÂ
Ugreen’s Nexode 65W charger has two ports and a retractable USB-C cable, yet it still delivers 65W of power. Source:…
Almost 7 in 10 iPhone owners plan to snag an iPhone 17, though the high price is a barrier for…
Incogni and DeleteMe are data removal services that can help you lock down your data, but they specialize in different…
The Elecom Nestout power bank is one of the toughest power banks I’ve tested. Source: Latest newsÂ
I film often, and sometimes I do it with my phone. With the latest release of the Android Camera app,…
Clearing your Galaxy Watch cache helps address battery drain, software bugs, or other performance issues. Here’s how to do it.…
Ming-Chi Kuo’s report says the number of folding iPhones that Apple is planning to manufacture are now on track to…