CVE ID : CVE-2025-7848
Published : July 29, 2025, 10:15 p.m. | 1 hour, 12 minutes ago
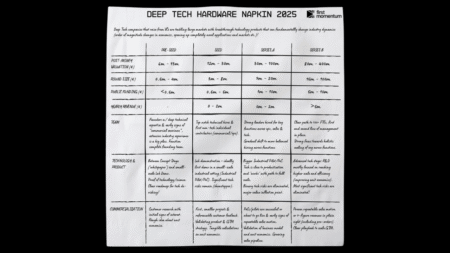
Description : A memory corruption vulnerability due to improper input validation in lvpict.cpp exists in NI LabVIEW that may result in arbitrary code execution. Successful exploitation requires an attacker to get a user to open a specially crafted VI. This vulnerability affects NI LabVIEW 2025 Q1 and prior versions.
Severity: 7.8 | HIGH
Visit the link for more details, such as CVSS details, affected products, timeline, and more…