A major security flaw has been detected in the popular PHP framework CodeIgniter4. The tag of a critical vulnerability, CVE-2025-54418,…
Threat actors have been observed exploiting a now-patched critical SAP NetWeaver flaw to deliver the Auto-Color backdoor in an attack…
The financial capital of India, Mumbai, has suffered staggering financial losses amounting to Rs 1,127 crore (approximately $135 million) between January…
Google has announced that it’s making available a security feature called Device Bound Session Credentials (DBSC) in open beta to…
Chinese companies linked to the state-sponsored hacking group known as Silk Typhoon (aka Hafnium) have been identified as behind over…
Cybersecurity researchers have disclosed now-patched critical security flaws in the firmware of Dahua smart cameras that, if left unaddressed, could…
Apple on Tuesday released security updates for its entire software portfolio, including a fix for a vulnerability that Google said…
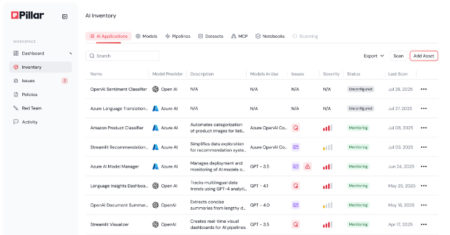
In this article, we will provide a brief overview of Pillar Security’s platform to better understand how they are tackling…
Cybersecurity experts have released a decryptor for a ransomware strain called FunkSec, allowing victims to recover access to their files…
Cybersecurity researchers are calling attention to an ongoing campaign that distributes fake cryptocurrency trading apps to deploy a compiled V8…
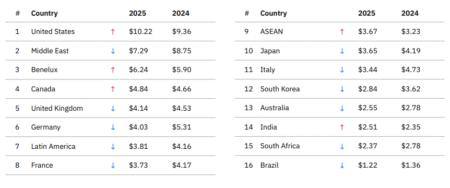
Data breaches in the U.S. are getting more costly even as they’re getting cheaper in the rest of the world. …
The viral women-only dating safety app Tea, built to flag red flags, gets flagged itself – after leaking over 70,000…
Apple has rolled out a wide-ranging series of Apple security updates and Rapid Security Responses, spanning iOS, iPadOS, macOS, tvOS,…
Threat actors are actively exploiting a critical security flaw in “Alone – Charity Multipurpose Non-profit WordPress Theme” to take over…
Security Operations Centers (SOCs) are stretched to their limits. Log volumes are surging, threat landscapes are growing more complex, and…
The financially motivated threat actor known as UNC2891 has been observed targeting Automatic Teller Machine (ATM) infrastructure using a 4G-equipped…
China’s top cybersecurity authority, the Cyberspace Administration of China (CAC), has officially summoned representatives from Nvidia to address alleged security…
Cyber threats and attacks like ransomware continue to increase in volume and complexity with the endpoint typically being the most…
The North Korea-linked threat actor known as UNC4899 has been attributed to attacks targeting two different organizations by approaching their…
Cybersecurity researchers have disclosed details of a new phishing campaign that conceals malicious payloads by abusing link wrapping services from…