ASUS built the T500 to offer a desktop-class RTX graphics card paired with an Intel Core laptop CPU. Does it…
Here are all the new Xbox games launching this week from September 1 through 7, including Team Cherry’s Hollow Knight:…
Gears of War: Reloaded has crossed 1 million players, marking the first official milestone for Xbox and The Coalition’s multiplatform…
The iBuyPower MK9 Pro RGB Mechanical Keyboard is a reliable PC gaming accessory with Linear switches that you can rely…
Xbox Game Studios and Obsidian Entertainment invited me to preview The Outer Worlds 2, and I’m even more excited to…
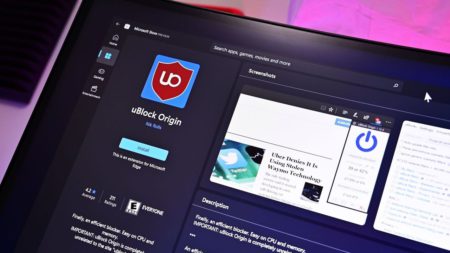
uBlock Origin vanished from Microsoft Edge after a mistake, but it’s back. Here’s why it happened and how to restore…
PlayStation and Xbox swapped Twitter banners, with PlayStation promoting Gears of War and Xbox spotlighting Helldivers 2 — a move…
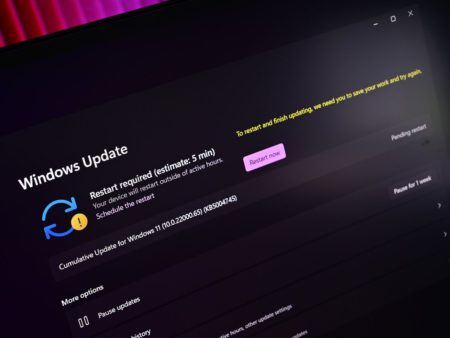
Windows 11 version 25H2 is now available in the Release Preview Channel, which is the last stop before general availability.…
Borderlands 4’s endgame brings Ultimate Vault Hunter Mode, weekly challenges, Firmware gear sets, Specializations, and Pearlescent loot to keep Vault…
Snapdragon X-powered Windows on Arm PCs can finally connect to Meta Quest headsets thanks to a new Mixed Reality Link…
In mere days before Hollow Knight: Silksong is finally released upon home consoles and PC, Team Cherry has divulged the…
Meta is seemingly having a hard time keeping its relatively new employees despite multimillion-dollar offers, with several members jumping ship…
Instead of ray tracing, Battlefield 6 doubles down on optimization, giving players high FPS, broad accessibility, and better stability across…
The US now owns 9.9% of Intel and wants the chipmaker to retain control of its foundry business. Source: Read…
CDKeys is officially rebranding as Loaded, but gamers have had a mixed response so far. Source: Read More /
Helldivers 2’s CEO says split-screen co-op is “technically feasible” and even 8-player lobbies could be possible, as the game surges…
Winux is a Linux operating system heavily inspired by Windows 11 and 10, from the Start menu to desktop icons…
Salesforce CEO Marc Benioff recently revealed that he scaled down the company’s support staff from 9,000 to 5,000 due to…
Microsoft’s next flagship Surface Pro is in development. Here’s everything we think we know, and what we want to see…
Windows 11 now delivers super wideband stereo audio over Bluetooth, improving game chat, Teams calls, and voice apps with clearer,…